Hello there.
If we have not met yet, my name is Warren Sealey, and I am the Technical Director for Symantec Email Security. As part of my role, I regularly speak to customers with highly aggressive attitudes towards phishing, ransomware and malware. Although we already offer industry leading SLAs for threat detection these customers have shared requirements for controls which they feel will make them safer.
Amongst these requests we have been asked to stop all emails which contain certain types of URL, emails where the domains used have been recently registered, and emails from particular parts of the world.
Whilst we recognize that these are valid requests, we don’t want to put them into the core detection engines because of the chance that they will convict emails that other customers may consider to be legitimate. So, to satisfy these needs we have built an email “firewall”, a policy engine which allows customers to create rules to convict emails based upon their corporate appetite for risk.
In this post I’m going to talk about the new features we’ve been releasing and then share how I’ve been helping customers onboard them safely and effectively.
The email firewall
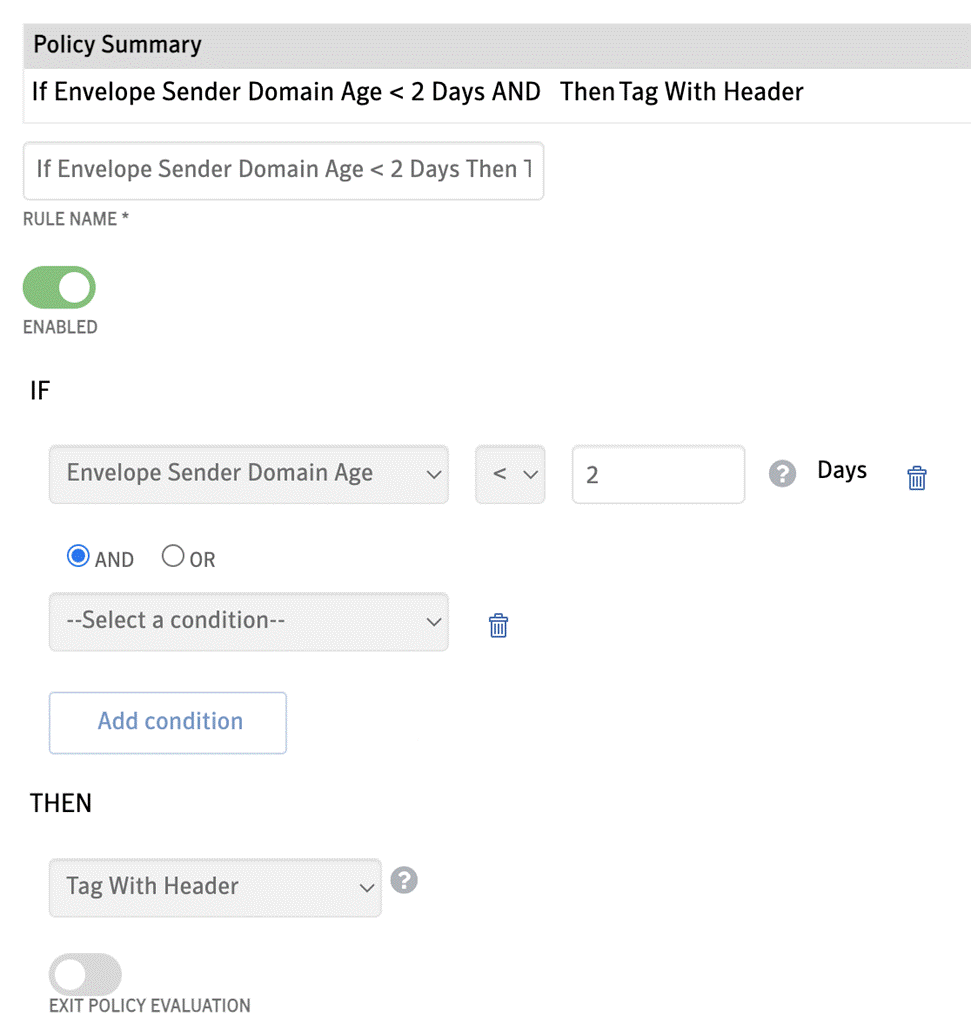
We call our new email firewall our “scan time” policy engine and we have positioned it at the end of the scanning stack after the existing malware, spam, image and data protection controls. As we built the solution we kept in mind that email security is a constantly changing battle with the regular emergence of new threats. To support this we have built a flexible policy engine which lets us develop and release new detections and actions much more quickly than we were able to before.
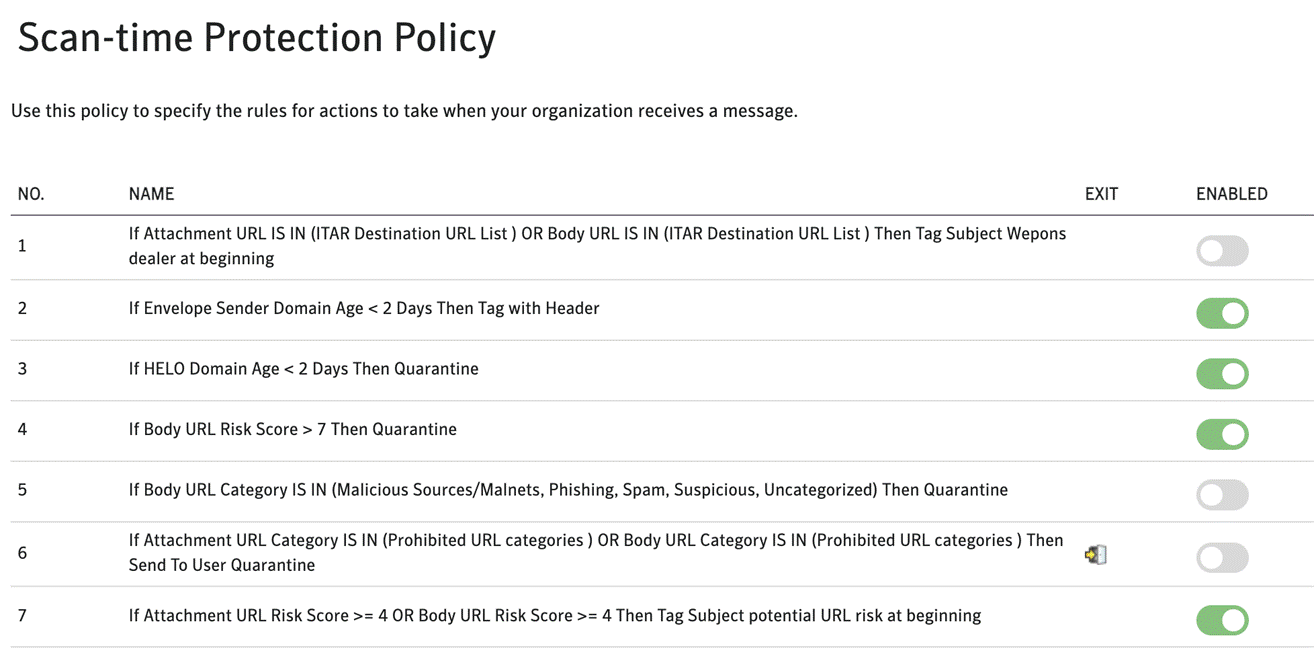
How it differs from our data protection engine
Existing users of our email security service have queried how this new engine compares to our existing data protection feature. The main difference is that data protection is focused on information protection threats, preventing the release of confidential information, driving our encryption solution, and controlling emails based on their content. The scan time policy engine is focused on threat protection, stopping emails containing spam, malware, phishing, etc. Also, the new engine has a much faster response time with changes reflecting across the infrastructure in close to real time.
New convictions
Based on our customer’s requests our first four new convictions are:
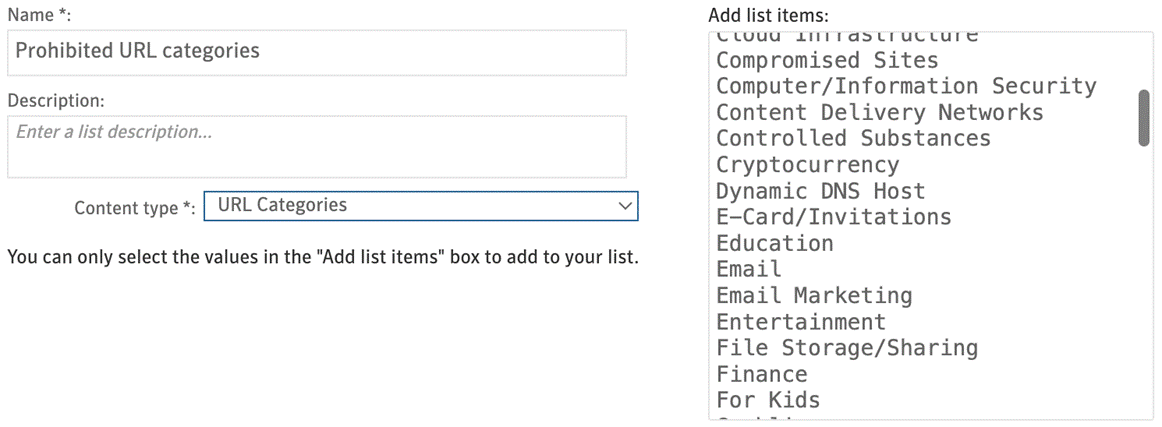
● URL categories - A sync with 60 plus Symantec web security service categories gives our customers the ability to convict emails based on the URL in the URLs in the body / attachments of the mail. - For a detailed list of the categories please review https://sitereview.bluecoat.com/#/category-descriptions
● URL risk levels - This technology comes from our web isolation solution and URL risk levels are calculated based on the traffic volumes, age, hosting location, and several other factors. There are 10 levels with 1 being the safest and 10 being the highest risk. https://docs.broadcom.com/doc/need-for-threat-risk-levels-in-secure-web-gateways-en provides a detailed explanation of how we calculate the risk levels for a site.
● Domain age - This has been one of our most requested indicators, many customers have suggested to us that recently registered domains are likely to be malicious.
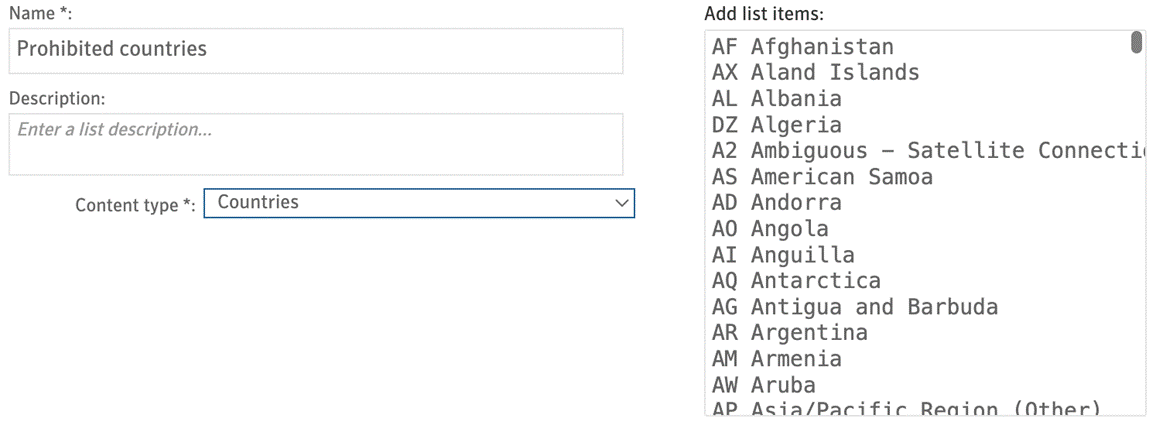
● Geographic IP locations - Some of our customers are governed by laws which prohibit them from doing business in certain countries and others know that they don’t have contacts in those regions. To help them minimize their attack surface we can now identify emails based on Geo-IP.
New actions!
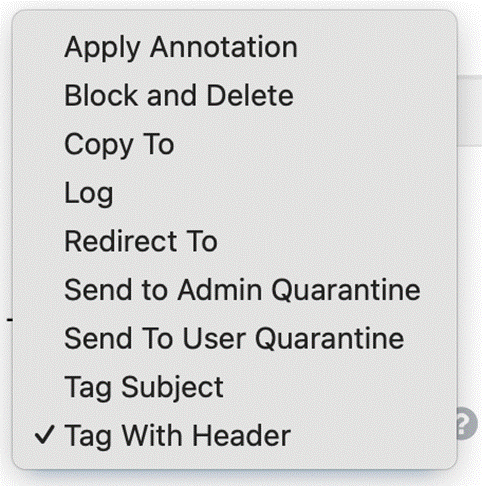
In addition to our existing actions, we have also released some new ways to handle convicted emails:
● Two types of quarantine - High security and low security. We’ve always had separate spam and malware quarantine areas, the spam quarantine can be set up to be accessed by the individual users and the malware quarantine which is only accessible by administrators with the appropriate permissions. For the policy engine we allow customers to choose which quarantine to use based on how they want the emails to be managed.
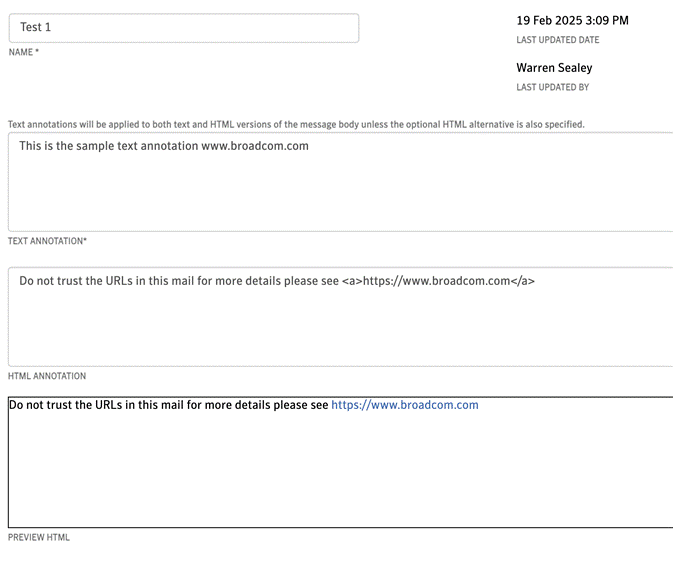
● Annotate - We’ve always supported subject line tagging but customers tell us that users commonly ignore subject line tags and that they need something more noticeable. To support this we have introduced mail body annotations where we will add a HTML formatted block of test to the body of the mail.
How to deploy
With all new technology the big question is how to deploy safely. In this case safe means without causing false positives. My suggestions for this process is as follows:
- Create some conservative policies such as:
- URL categories that you may have already prohibited via your web proxy
- The most high risk URLs (risk level 9 and 10)
- VERY new domains (less then 10 days)
- A couple of countries where you know you have no customers
- Set these rules to “log only” and activate them
- Create a report in the ClientNet portal and select scan time policy incidents. I’d suggest setting the report to send a link to a download in the portal and have it run once per week.
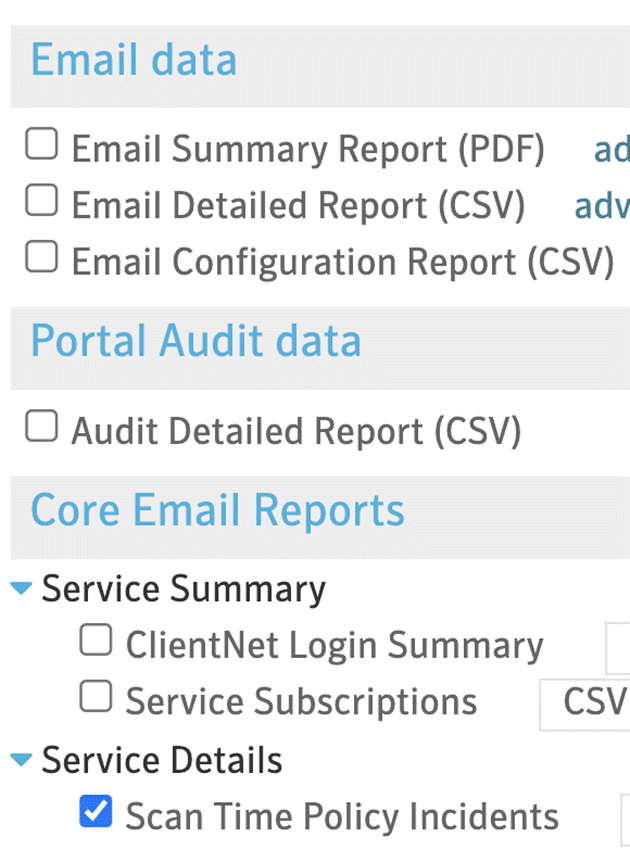
Analyzing the report results
The report generated in the process suggested above will be a CSV file but one of the fields will contain .json formatted data. That data contains useful information including the URL, its risk level, category, domain ages, and geoIP information. There are various ways to extract that information but I’ve used a spreadsheet with some calculated fields. N.b. these formulas are for excel on a Mac, this version of excel has different features to many others so you may want to build these differently depending on the spreadsheet you are using.
Category name
=MID(L2, FIND("category_name"":""", L2) + LEN("category_name"":"""), FIND(""",", L2) - FIND("category_name"":""", L2) - LEN("category_name"":"""))
URL
=MID(L2, FIND("url"":""", L2) + LEN("url"":"""), FIND("}]}", L2) - (FIND("url"":""", L2) + LEN("url"":"""))-1)
Risk level
=MID(L2, FIND("risk"":", L2) + LEN("risk"":"), FIND(",""url", L2) - (FIND("risk"":", L2) + LEN("risk"":")))
Once you have analyzed a couple of weeks worth of data you will be in a good position to understand if you need to adjust your policies or if you are ready to change the action to something more aggressive. With the customers I have worked with I’ve commonly ended up with two policies for URL categories, one for the most “dangerous” sites and another for less dangerous but potentially non-work related sites. You can set one policy to block emails and the second to log, annotate, or tag the subject line to warn the recipient of the mail.
Post delivery scanning
This article has been focused on evaluating the email before it has been delivered to the recipient, Broadcom also offers a “clicktime” feature which uses URL rewriting to check the category and risk level of a URL at the time the user clicks the link. This provides another way of controlling access to sites if you don’t want to block the mail but you either want to stop the user accessing the page or allow them to access it through an "isolation" chamber.