Addressing VMSA-2021-0002 for vCenter 7.0
*NOTE* This article is specifically for addressing VMSA-2021-0002 for vCenter 7.0. If you are looking for previous versions, please see this article: VMSA-2021-0002 for vCenter 6.5 and vCenter 6.7
As per VMSA-2021-0002, the affected vCenter version is 7.0 with CVE-2021-21972, CVE-2021-21973, CVE-2021-21974.
For more details, please refer to VMware KB: https://kb.vmware.com/s/article/82374
For any queries on this procedure or on VMSA 2021-0002, post your question here - https://community.broadcom.com/vmware-cloud-foundation/communities/community-home?CommunityKey=47d275f3-6e8e-45c2-8b72-b62f261013fd
To mitigate the issues vCenter 7.0 needs to be patched to 7.0 U1c or above.
- vCenter Server 7.0 Update 1c | 17 DEC 2020 | ISO Build 17327517
- The latest patch available on the default repository is 7.0U1d for Feb 2021
-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
- Please take a non-memory, non-quiesced snapshot of the vCenter VM (if standalone), before implementing any change.
- In case there are multiple vCenter servers linked, do take powered down snapshots of all nodes before proceeding with vCenter update.
- If DRS is set to Fully Automated, please change it to Manual while updating.
- Make note of the host IP/FQDN where vCenter VM is deployed.
- Ensure that you have the login credential for the ESXi host which has the vCenter VM.
- vCenter Server will be rebooted during the process.
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Below is an example on patching VCSA 7.0.1 U3, Build 16858589 to 17327517
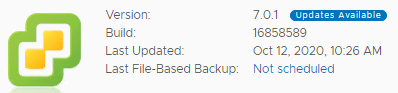
1 In a browser open VAMI (VMware Appliance Management Interface): https://<vCenterFQDN>:5480
2 Login as root
3 In the Navigator tab (on the left), click Update
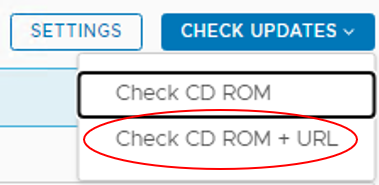
4 In CHECK UPDATES drop down change the option to check CD ROM + URL (make sure there is internet connectivity to vCenter server)
Alternatively, you can download 7.0 Update 1c build 17327517 from the download portal, and attach the iso to the CDROM of the vCenter server VM
5 Select a patch released on Dec 17, 2020 or later.
However, VMware recommend patching to the latest available version.
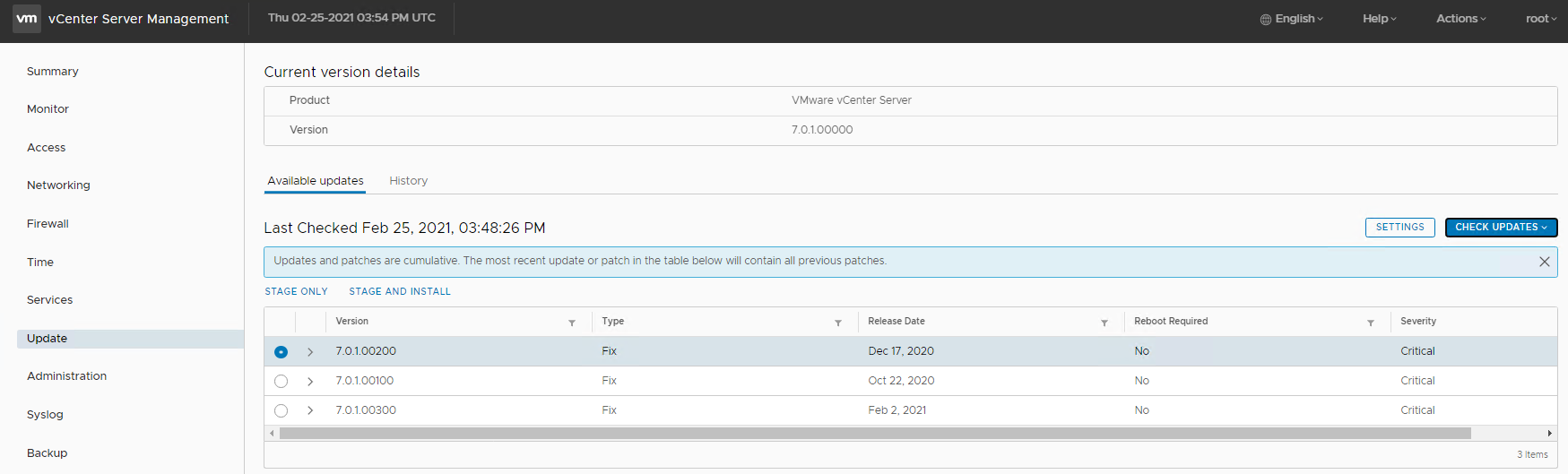
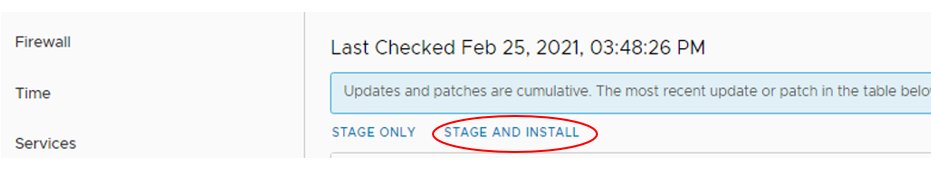
6 Select STAGE AND INSTALL
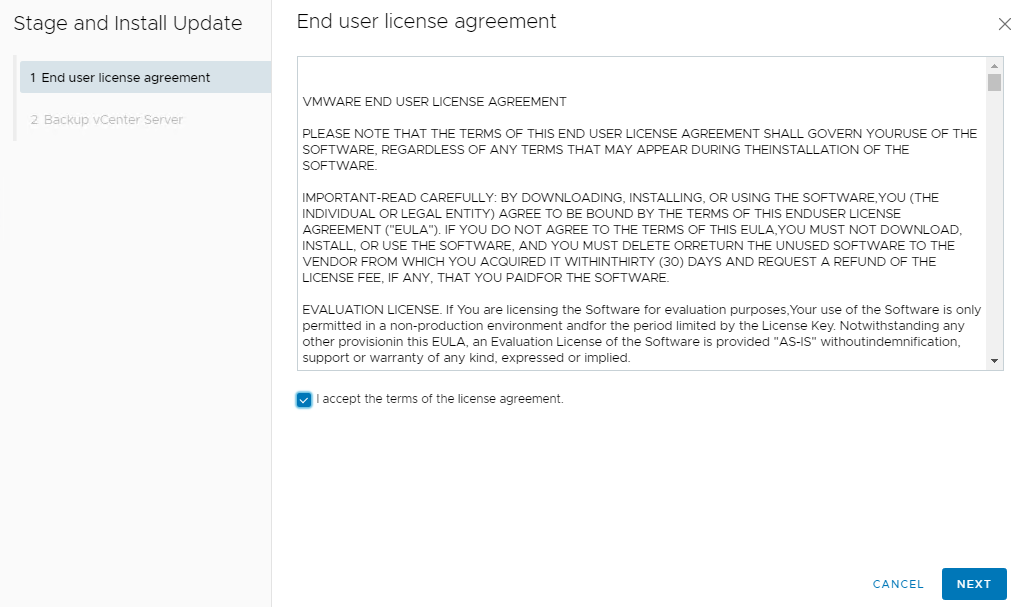
7 Accept End user license agreement and click on NEXT
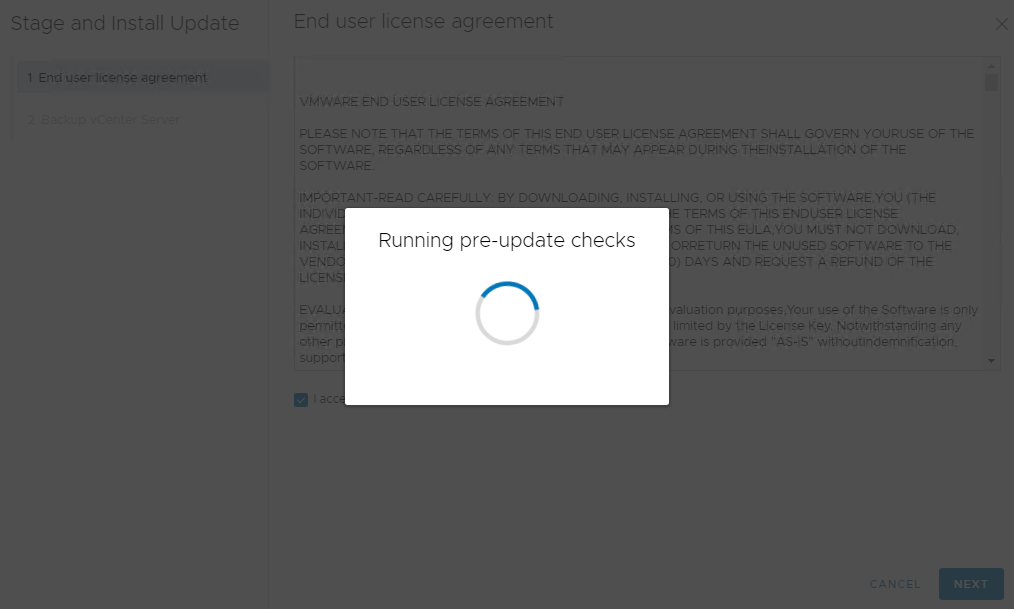
8 It will start Running pre-update checks
9 Enter Single Sign-On administrator password (Default SSO administrator: administrator@vsphere.local) and click on NEXT
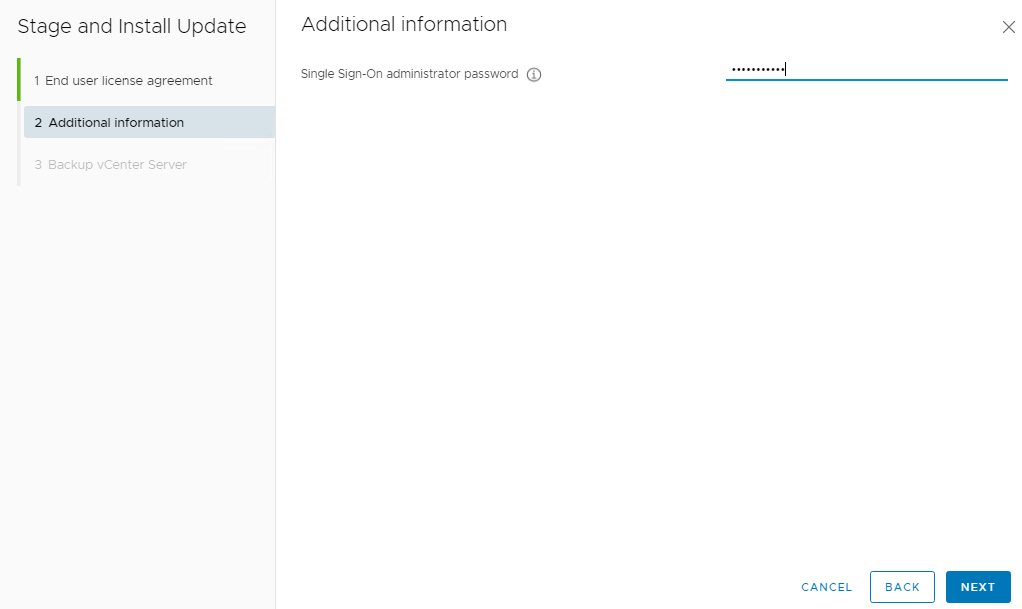
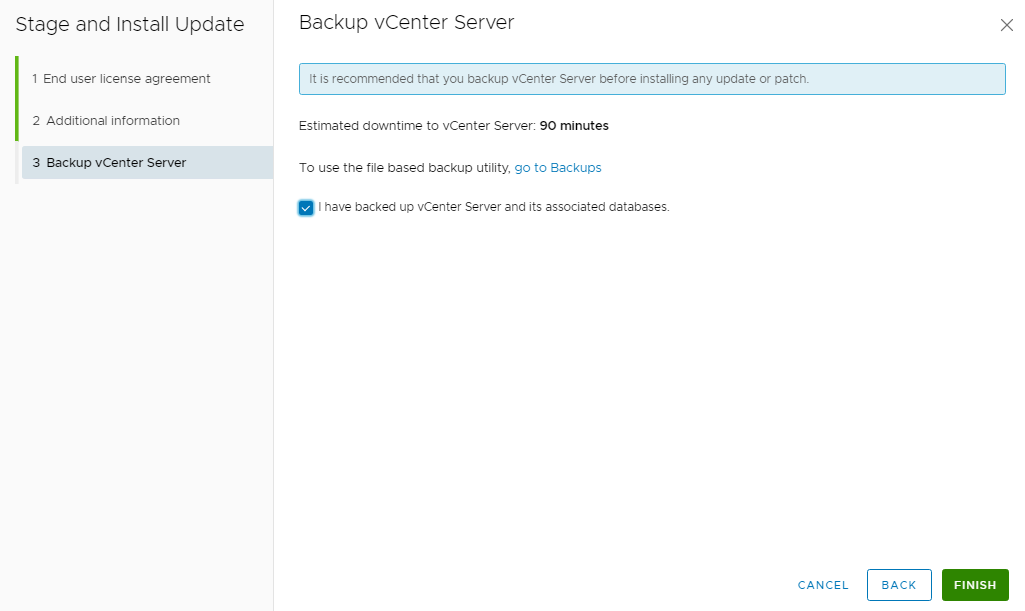
10 Check the box in Backup vCenter Server screen if you have taken a vCenter Backup and click FINISH
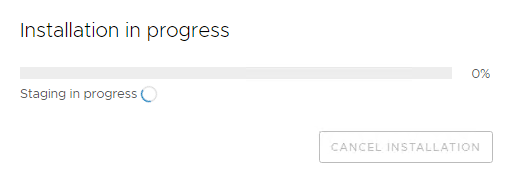
11 You will see Installation in progress as follows
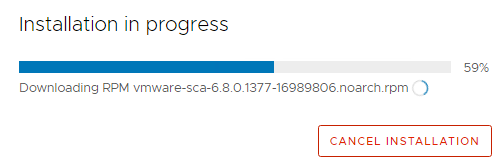
12 Click on CLOSE
13 The vCenter is patched with the build 17327517
*NOTE* This article is specifically for addressing VMSA-2021-0002 for vCenter 7.0. If you are looking for previous versions, please see this article: VMSA-2021-0002 for vCenter 6.5 and vCenter 6.7