I can confirm that vCenter 5.5 (U2) communicates with hosts (5.5 U2) via SSLv3 only, the reason being vCenter only supporting SSLv3 in its initial SSL Client Hello packet when connecting to an ESXi host::
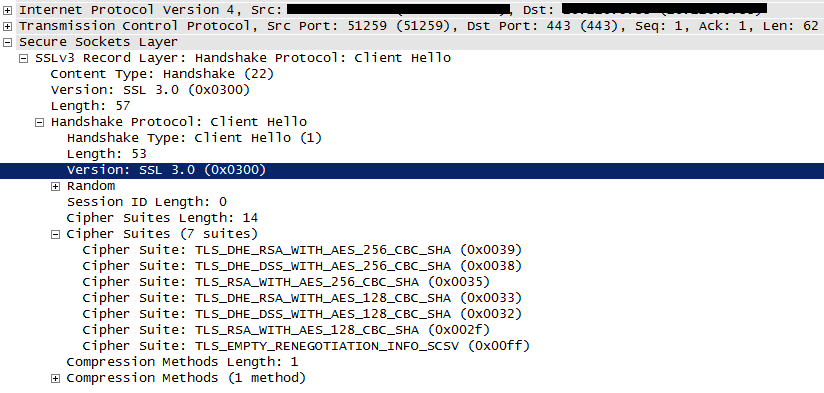
Note: The SSL/TLS communication socket between vCenter and vpxa agents on hosts is always initiated from the vCenter vpxa.exe process acting as the Client connecting to port 443 of a host and not vice versa (what protocols vCenter supports on port 443 is irrelevant).
ESXi supported TLS1 along with SSLv3 since a long time ago, and since ESXi 5.5 it comes libraries from the openssl 1.0.1 tree that support TLS1.1/1.2 as well, which can be confirmed from a host:
# openssl s_client -connect [ESXi Host Name goes here]:443 < /dev/null 2>1 | grep 'SSL-Session' -A2
SSL-Session:
Protocol : TLSv1.2
Cipher : AES256-GCM-SHA384
I suspect configuration changes have to be made to the vCenter Java application so the Client sends a TLS version in the handshake Hello. When I lanuch the Java control panel on the vCenter via the command below I can see that SSLv3 and TLSv1 are supposedly enabled, but the handshake Client Hello sent by vCenter to the Client is SSLv3 only:
"C:\Program Files\Common Files\VMware\VMware vCenter Server - Java Components\bin\javaw.exe" -Xbootclasspath/a:"c:\Program Files\Common Files\VMware\VMware vCenter Server - Java Components\lib\deploy.jar" com.sun.deploy.panel.ControlPanel
It's possibly overwritten somewhere in the application and I haven't tried to disable SSLv3 there since I don't have a test environment available at the moment. Anyways it would be nice if VMware either completely removed that KB article or opened it up to the public instead of saying:
You are not authorized to access this article. It may have been moved or the reference is out-of-date.