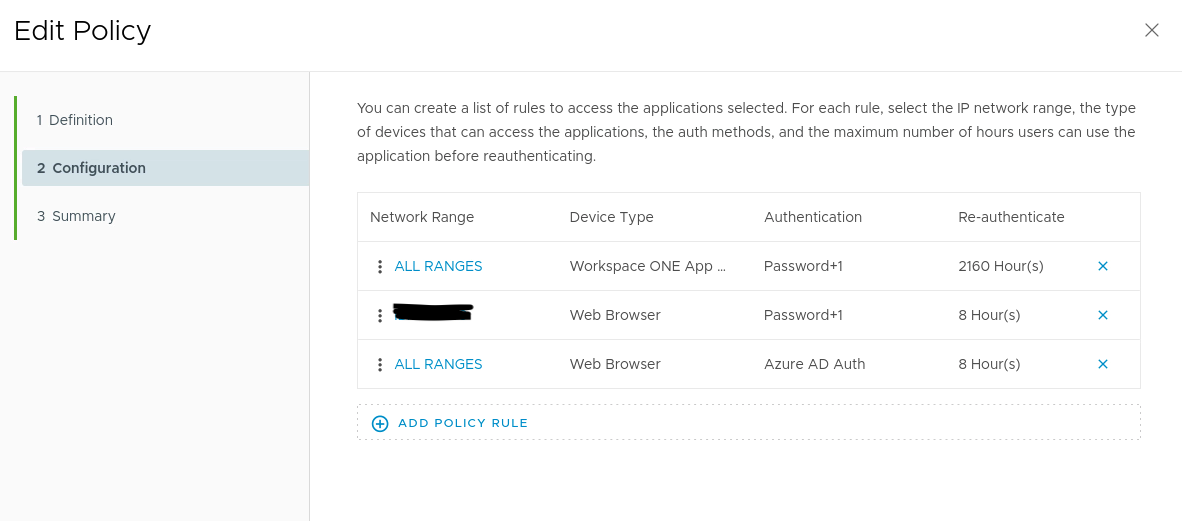
So I created a separate policy, and that didn't seem to work.
But following the directions in the blog; and then adding to the default policy, a special management network, that uses the original Password / fallback Password (Local Directory). It works.
From the special management network, it uses normal auth method and you can login as the admin account you created at install; or you can change domain to use local AD.
From anywhere else, when you click login, it goes out to Azure AD requiring MFA.