There are two ways that devices can be identified in Symantec Endpoint Protection (SEP) 11 and 12: 1. by Class ID, 2. by Device ID. There are advantages and disadvantages of using either method and there is a different functionality for each method. This article will be discussing these two IDs and how to use then in SEP.
Class ID
A Class ID is a generic category of devices that are designated by the Windows operating system. A Class ID is always listed as a Guid. Here are some examples of Class IDs.
- Disk Drives - {4d36e967-e325-11ce-bfc1-08002be10318}
- Storage Volumes - {71a27cdd-812a-11d0-bec7-08002be2092f}
- USB devices - {36FC9E60-C465-11CF-8056-444553540000}
- DVD/CD-ROM - {4D36E965-E325-11CE-BFC1-08002BE10318}
- IDE - {4d36e96a-e325-11ce-bfc1-08002be10318}
- PCMCIA - {4d36e977-e325-11ce-bfc1-08002be10318}
In SEP, wildcards are not supported on Class IDs.
For a list of Class IDs you can click here.
Device ID
A Device ID (also known as a Device Instance ID in Windows) is a specific ID that is given to each device. A Device ID can be much more useful for blocking or allowing devices because it is made by concatenating a list of data about the particular device. Device IDs are generally in a more readable format.
Here are two common formats for Device IDs:
<class>\<type>&<vendor>&<model>&<revision>\<serial number>
<class>\<type><vendor><model><revision>\<serial number>
Here are some examples of Device IDs for a few devices:
- SanDisk Micro Cruzer - USBSTOR\DISK&VEN_SANDISK&PROD_CRUZER_MICRO&REV_2033\0002071406&0
- Apple iPod - �USBSTOR\DiskApple___iPod____________1.62\4&3656B0&0
- Hitachi IDE Hard Drive - IDE\DISKHTS541060G9SA00_________________________MB3IC60H\4&14AA9DA8&0&0.0.0
For Device IDs we support wildcards. Both * and ? are supported.
- Asterisk [*] - means zero or more of any character
- Question mark [?] - means a single character of any value
Here are some examples of using wildcards:
Any USB Storage device
Any USB Disk
Any USB SanDisk drive
- USBSTOR\DISK&VEN_SANDISK*
Any USB SanDisk Micro Cruzer drive
- USBSTOR\DISK&VEN_SANDISK&PROD_CRUZER_MICRO*
A specific SanDisk device
- USBSTOR\DISK&VEN_SANDISK&PROD_CRUZER_MICRO&REV_2033\0002071406&0
Generally I recommend using Device ID's over Class IDs for most use cases.
Hardware Devices
Both the Class IDs and the Device IDs can be added to the SEP manager under the Policy Components --> Hardware Devices section.

Device Viewer
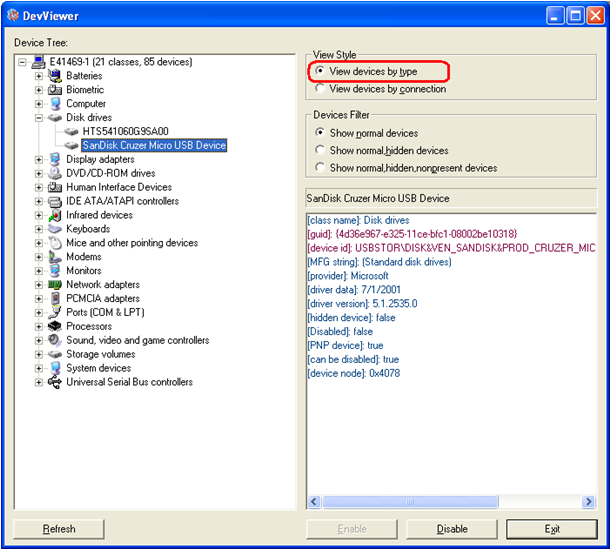
On the SEP CD or DVD under the Tools\NoSupport folder you will find the Device Viewer (DevViewer). The Device Viewer can be used to get either the Class ID or the Device ID of a particular device. It also has the ability to let you copy the IDs to the clipboard so that you can paste into the SEP manager (using Ctrl+V).

The Device Viewer also gives you the ability to view devices by type or by connection.
By type:
By connection:

Device Control
SEP has the ability to block devices using either Application Control or Device Control. Device Control gives the ability to completely disable a device. When a device has been disabled this way you can see it as disabled even in the Windows Device manager. Device Control can be useful if you do not want your users to use the device at all. With Device Control you can use both Class IDs and Device IDs.

Device Control also allows you to block devices at any node in the tree. If you block a device at one node then all devices below that node (all children) will be blocked also. Conversely if you exclude a device then all the devices above that node will also be excluded.
In the example below, if you want to block the SanDisk Cruzer you can block it by blocking the USB Mass Storage Device:

Note: on Windows 2000, XP and 2003 if you disable a USB device with SEP's Device Control then the operating system will power down the device. Devices such as Androids, iPods, cameras and other types of portable devices will not be able to get charged. On newer operating systems such as Windows Vista, Windows 7 and 2008 the operating system will allow the devices to receive power even if they are disabled.
Application Control
If you want to do more granular blocking of devices you can do that by using the Application Control feature. Application Control is a very powerful engine that allows you to block read, write or execute on a device. If you want to you can even go to the level of controlling what individual applications can do. For example you could create a policy using Application Control to block any program that is running off a USB drive from changing the registry or modifying files on the host computer.
With Application Control you can only use Device IDs. Class IDs will not work. Device IDs are allowed in the following places:
Program Definition
- Application Rule process
- Launch process
- Terminate process
File Definition

You can only block a device with Application Control that is at the end of a node in the tree, unless the end node is "Generic volume" or "Storage volume". In these two cases you will block the device that is one up from the last node (the parent of the last node).
In the example below you cannot block the SanDisk Cruzer Micro at either the "USB Mass Storage Device" node or at the "Generic volume" node:

Most Device ID's that are supported by Application Control will have one of these types:
USBSTOR
- Example: USBSTOR\DISK&VEN_SANDISK&PROD_CRUZER_MICRO&REV_2033\0002071406&0
FCD
- Example: FDC\GENERIC_FLOPPY_DRIVE\4&371082C9&0&0
IDE
- Example: IDE\DISKHTS541060G9SA00_________________________MB3IC60H\4&14AA9DA8&0&0.0.0
SCSI
- Example: SCSI\DISK&VEN_WDC_WD50&PROD_00KS-00MNB0&REV_700.\4&1291CDED&0&000
Note: Application Control can only block devices that are seen by Windows as disk drives and have drive letters associated with them. Devices that do not add drive letters (such as an iPhone or iPad) will need to be blocked using Device Control.