We did have to backout our implementation last summer due to issues with the 21.1 releases of IG FTP.
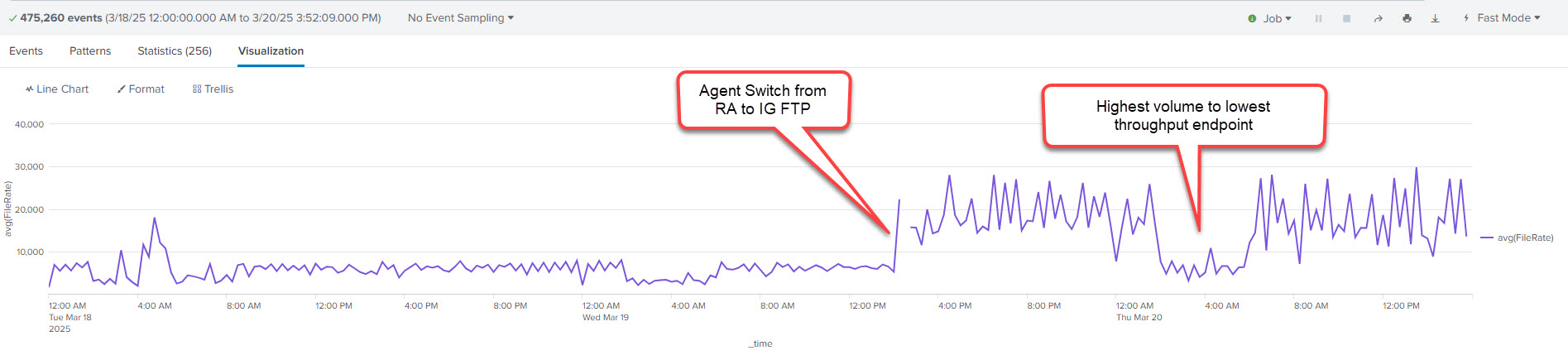
We have completed our migration and using Splunk to analyze our IG FTP Agent report logs, we have seen a significant increase in average throughput. This must be negotiating for much higher transfer rates with the new Agent.
Original Message:
Sent: Jun 21, 2024 04:12 PM
From: Eric Lontz
Subject: Automic IG FTP Agent Deployment Notes
We are currently running 21.0.5hf4 of Automation Engine and some of our customers were using algorithms the RA FTP Agent couldn't support with its old JSCH.
We are in the process of migrating but I thought I would share with you some of the things we encountered on this. Be aware some of the notes in additional switches have not been verified. I hope some of this information can be of help.
IG FTP Agent Notes
- Automic IG FTP Agent Version notes
- Agent Version 21.0.0, has a SFTP Key Authentication bug
- Agent Version 21.0.1 has a FTPES/FTPS bug (resolves key authentication bug)
- Agent Version 21.1.0 fully functional (resolved FTPES/FTPS bug)
- Version 21.1.0 uses SSH-2.0-JSCH_0.2.17
- https://github.com/mwiede/jsch
- This only supports known secure algorithms, keys, ciphers and macs
- Uses JDK
- If Migrating from RA FTP to IG FTP be sure to remove the RA FTP plugin from UC_ECC_PLUGINS in client 0
SMD (V21+) Changes
- You do not need to specify the path to the jar file in the uc4.smd file
- You do not need to specify any ini path in the uc4.smd file
Java Notes
- Java does not like any key that is not a base 64 number. Some customer have host keys in odd bases.
- To allow this edit the java.security file in the ./lib/security/policy folder
- Lines 69 to 83 should look like the below. The first line is what allows non 64 base keys (this has to be added)
# List of providers and their preference orders (see above):
#
security.provider.1=org.bouncycastle.jce.provider.BouncyCastleProvider
security.provider.2=sun.security.provider.Sun
security.provider.3=sun.security.rsa.SunRsaSign
security.provider.4=sun.security.ec.SunEC
security.provider.5=com.sun.net.ssl.internal.ssl.Provider
security.provider.6=com.sun.crypto.provider.SunJCE
security.provider.7=sun.security.jgss.SunProvider
security.provider.8=com.sun.security.sasl.Provider
security.provider.9=org.jcp.xml.dsig.internal.dom.XMLDSigRI
security.provider.10=sun.security.smartcardio.SunPCSC
security.provider.11=sun.security.mscapi.SunMSCAPI
#
- JCE Policy is not needed past java 1.8_116 so ignore any references to it.
- JDK is required
- JSCH support (SSH-2.0-JSCH_0.2.17)
- KEX Algorithms supported by default
- curve25519-sha256,
- curve25519-sha256@libssh.org
- ecdh-sha2-nistp256
- ecdh-sha2-nistp384
- ecdh-sha2-nistp521
- diffie-hellman-group-exchange-sha256
- diffie-hellman-group16-sha512,
- diffie-hellman-group18-sha512
- diffie-hellman-group14-sha256
- ext-info-c
- kex-strict-c-v00@openssh.com
- Host Key Algorithms supported by default
- rsa-sha2-512
- rsa-sha2-256
- ssh-ed25519
- ecdsa-sha2-nistp256
- ecdsa-sha2-nistp384
- ecdsa-sha2-nistp521
- Ciphers supported by default
- aes128-ctr,aes192-ctr
- aes256-ctr
- aes128-gcm@openssh.com
- aes256-gcm@openssh.com
- MACs Supported by default
- hmac-sha2-256-etm@openssh.com
- hmac-sha2-512-etm@openssh.com
- hmac-sha1-etm@openssh.com
- hmac-sha2-256
- hmac-sha2-512
- hmac-sha1
- Compression supported by default
- zlib@openssh.com
- zlib
- none
Allowing Insecure...
Host Keys
- Sometimes you need to add back in a insecure key due to not everyone being up to date on their servers, such as ssh-rsa
- To allow this you need to modify the smd start command to contain 2 switches, -Djsch.server_host_key=<csvlist> and -Djsch.client_pubkey=<csvlist>
- for example
- -Djsch.server_host_key=rsa-sha2-512,rsa-sha2-256,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ssh-rsa
- -Djsch.client_pubkey=rsa-sha2-512,rsa-sha2-256,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ssh-rsa
- Be aware only the host_key and pubkey algorithms specified will be used
Key Exchange
- Sometimes you need to add back in a insecure key due to not everyone being up to date on their servers, such as diffie-hellman-group-exchange-sha1
- To allow this you need to modify smd start command to contain a single switch, -Djsch.kex=<csvlist>
- For example
- -Djsch.kex=curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256,ext-info-c,kex-strict-c-v00@openssh.com,diffie-hellman-group-exchange-sha1
- Be aware only the kex specified will be used
Ciphers
- Sometimes you need to add back in a insecure key due to not everyone being up to date on their servers, such as aes256-cbc
- To allow this you need to modify smd start command to contain a single switch -Djsch.cipher=<csvlist>
- For example
- -Djsch.cipher=aes128-ctr,aes256-cbc
- Be aware only the ciphers specified will be used
Additional switches
- -Djsch.prefer_known_host_key_types=<csvlist>
- -Djsch.enable_server_sig_algs=<csvlist>
- -Djsch.mac=<csvlist>
- -Djsch.compression=<csvlist>
- -Djsch.lang=<csvlist>
- -Djsch.dhgex_min=<csvlist>
- -Djsch.dhgex_max=<csvlist>
- -Djsch.dhgex_preferred=<csvlist>
- -Djsch.compression_level=<csvlist>
- -Djsch.preferred_authentications=<csvlist>
- -Djsch.check_ciphers=<csvlist>
- -Djsch.check_macs=<csvlist>
- -Djsch.check_kexes=<csvlist>
- -Djsch.check_signatures=<csvlist>
- -Djsch.fingerprint_hash=<csvlist>
- -Djsch.max_auth_tries=<csvlist>
SMD Start Command
- The SMD Start command is limited to 512 characters. this is from the end of DEFINE IGFTPAGENT; to the next semicolon for Start Path.
- The current SMD start command for this is
- DEFINE IGFTPAGENT_2;"C:\Program Files\Java\jdk-1.8\bin\java" -jar -Xrs -Xmx2G -Djsch.server_host_key=rsa-sha2-512,rsa-sha2-256,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ssh-rsa -Djsch.client_pubkey=rsa-sha2-512,rsa-sha2-256,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ssh-rsa -Djsch.kex=ecdh-sha2-nistp256,diffie-hellman-group-exchange-sha256,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256,diffie-hellman-group-exchange-sha1 -Djsch.cipher=aes128-ctr,aes256-cbc,aes256-ctr ucxjftp.jar;C:\Automic\Agents\rapidautomation\IGFTP\bin;WINTITLE=*UC4*
- it is using -Djsch.server_host_key= Djsch.client_pubkey= -Djsch.kex= and -Djsch.cipher=
- This is not all the secure algorithms it can support but instead what works with all our connections and is less than 512 characters
- The stuff in italics is some of the default algorithms, bold is the insecure one we needed.