This guide helps you during the setup of
SSL/TLS of your (product)'s installation. It will guide you through
all the necessary steps needed to setup an encrypted connection between your
installation and the browser of the users.
Preparations
1.
Open a cmd as
Administrator and move to the tomcat config directory (TOMCAT_HOME/conf/).
2.
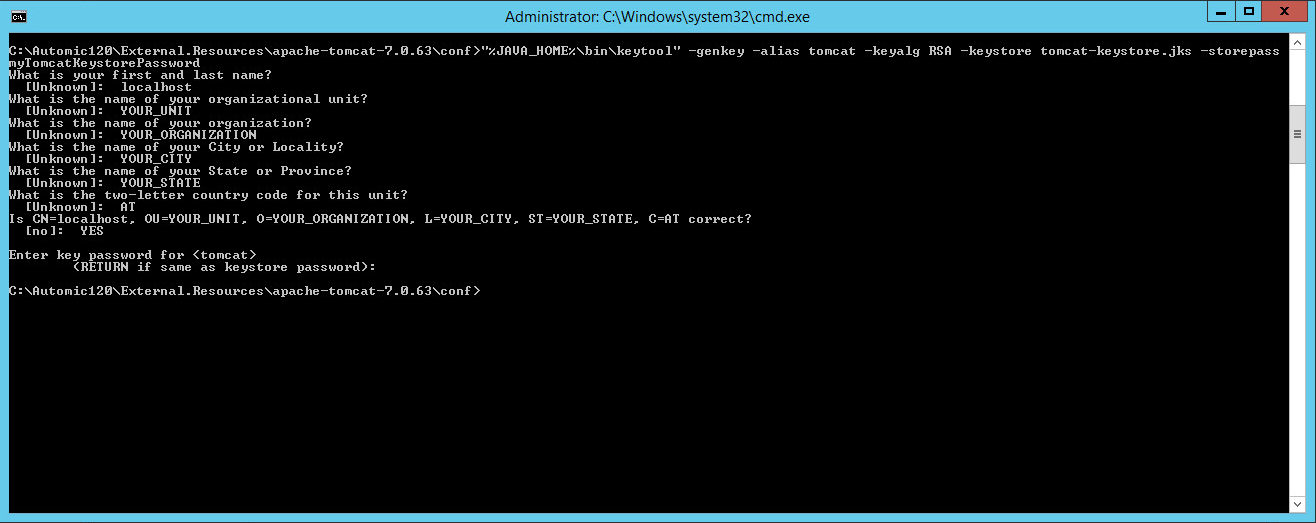
Create a keystore with
a self signed certificate using the following command:
|
> "%JAVA_HOME%\bin\keytool" -genkey -alias tomcat -keyalg RSA -keystore
tomcat-keystore.jks -storepass myTomcatKeystorePassword
What is your first and last name?
[Unknown]: localhost
What is the name of your organizational unit?
[Unknown]: YOUR_UNIT
What is the name of your organization?
[Unknown]: YOUR_ORGANIZATION
What is the name of your City or Locality?
[Unknown]: YOUR_CITY
What is the name of your State or Province?
[Unknown]: YOUR_STATE
What is the two-letter country code for this unit?
[Unknown]: AT
Is CN=localhost, OU=YOUR_UNIT, O=YOUR_ORGANIZATION, L=YOUR_CITY,
ST=YOUR_STATE, C=AT correct?
[no]: YES
Enter key password for <tomcat>
(RETURN if same as keystore password):
|
3.
Note that you have to use the hostname / domain of your AWI instance as your
first and last name, e.g. localhost in our example. This command will create
a new keystore file named tomcat-keystore.jks protected with the password myTomcatKeystorePassword located in the configuration directory. You can change
those values, i.e. the passwords as you like. The keystore contains a self-signed
certificate for your AWI instance. If you do not want to used certificates
signed by a certificate authority you can skip the next step.
4.
You now have to import
the certificate into your created keystore. If you have a chain certificate or
root certificate, you have to import them first into your keystore using the
following command.
|
> "%JAVA_HOME%\bin\keytool" -import -alias root -keystore tomcat-keystore.jks -trustcacerts -file <filename_of_the_chain_certificate>
|
5.
Afterwards you can
import your certificate.
|
> "%JAVA_HOME%\bin\keytool" -import -alias tomcat -keystore tomcat-keystore.jks -file <your_certificate_filename>
|
6.
Be aware that the
tomcat only supports keys and certificates in the JKS, PKCS11 or PKCS12 format. To import an existing certificate signed by your
own CA into a PKCS12 keystore using OpenSSL you would execute a
command like:
|
openssl pkcs12 -export -in mycert.crt -inkey mykey.key
-out
mycert.p12 -name tomcat -CAfile myCA.crt
-caname
root -chain
|
7.
For more advanced cases,
please consult the OpenSSL documentation.
Configure
tomcat
1.
Open the server.xml
file located in the configuration directory of your tomcat instance.
2.
Add the following
Connector configuration to your configuration file
|
<Connector
port="8443" protocol="org.apache.coyote.http11.Http11Protocol"
keyAlias="tomcat" keystoreFile="conf\tomcat-keystore.jks" keystorePass="myTomcatKeystorePassword"
maxThreads="150" SSLEnabled="true" scheme="https" secure="true"
clientAuth="false" sslProtocol="TLS" />
|
3.
Note that you have to
change the keystorePass to the set password before.

4.
Restart you tomcat
instance to apply the changes.
Access
Automic Web Interface
1.
You can now access the
Automic Web Interface using a secure connection by using https://YOUR_DOMAIN:8443/awi/ (e.g.https://localhost:8443/awi/)
2. If you are using a
self-signed certificate you may receive a warning that the connection is
untrusted, because is not possible to verify the identity. You can only avoid
this warning if you are using signed certificates by a trusted authority.
However the connection is encrypted in the same way as using a signed
certificate. You have to confirm that you want to use the self-signed
certificate.

3. You now can use AWI
over https.
References:
JAVA
Key Generation
https://docs.oracle.com/cd/E19509-01/820-3503/ggfen/index.html
Tomcat
SSL
http://tomcat.apache.org/tomcat-7.0-doc/ssl-howto.html
https://dzone.com/articles/setting-ssl-tomcat-5-minutes