There's no TPM device in that VM's configuration file. You can verify this by going back to the VM's Settings and check for the existence of the TPM device. If you removed the TPM device, then yes, there most likely will be files changed in the VM bundle.
At this point you could try to restore all the non-VMDK files in the VM from a backup. If you do that, you'd probably have to replace all the files not named .vmdk. There are some linkages between the vmx and the other files that I'd suspect might not be correct if you try to piece together individual files.
You can also add the TPM device back to the VM since it's already encrypted. Go back to the VM's settings and click on the "Add device" button. You should see the TPM device available to add back into the configuration. Once you power on the VM you have to treat the situation the same as a physical PC that has had its motherboard swapped and the TPM is now wiped. (the major thing to be aware of is if Windows has enabled BitLocker - you'd need the BitLocker recovery key in that case).
Original Message:
Sent: Jan 26, 2025 10:47 PM
From: Fred Macondray
Subject: VM encrypted itself, don't know the password (part.2) (after 13.5 update)
That got me back, I was wondering why today the vmx was corrupted. It showed up in Fusion by path and not name.
Now it says encryption is enabled, but there's no TPM chip:
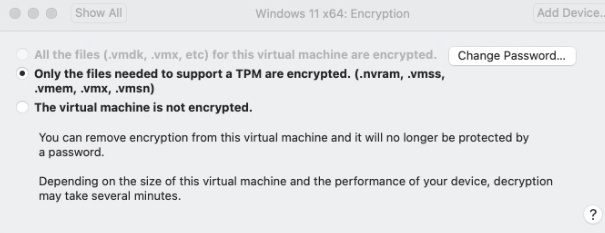
When I look at file dates in the bundle, only two files were changed after I removed the TPM chip. I've considered replacing those files, but I suspect that might not work due to differences.
I'm working on moving TAR file as the system didn't let me import the drive due to disk space issues.
Original Message:
Sent: Jan 26, 2025 10:16 PM
From: Technogeezer
Subject: VM encrypted itself, don't know the password (part.2) (after 13.5 update)
I just took a look at the .vmx file. Line 20 is corrupted.
it seems to have a funky couple of bytes at the beginning of the line. The line should read:
nvram = "Windows 11 x64.nvram"
It might be a quick experiment to shut down Fusion completely, making a copy of this VM, manually fixing the .vmx file's line 20, then trying to power on the VM once more.
------------------------------
- Paul (technogeezer)
Original Message:
Sent: Jan 26, 2025 09:57 PM
From: Technogeezer
Subject: VM encrypted itself, don't know the password (part.2) (after 13.5 update)
Yes, encryption keys are not stored in the VM. If you chose to have them remembered, they're kept in the user's login keychain.
You might want to check the user's login keychain to see if there's an entry for "VMware Fusion encryption" is present. The "Where" field of those entries points to the associated VM.
If you're going to restore from a Veeam backup, then restore the VM's entire bundle to another folder and see if it'll power up -- assuming you have the password memorized or you can find the password for the original VM in the user's login keychain. But I wouldn't try stitching together .vmx et. al. files of a VM's bundle from a backup into an existing VM without preserving the original first. And verifying that your backup can power on.
I'm seeing some .vmx corruption in one of the vmware-vmfusion.log files you just posted. Without the .vmx file I can't tell what;s broken or if it can be repaired. Duh. I just saw the .vmx file. Let me see if I can see what the power on is complaining about...
If the original VM's disks aren't encrypted, it's pretty quick to rebuild the VM with a copy of the original VM's virtual disks.
I appreciate the positive comments about those of us here in the forum that jump in to help others. I do wish there was more participation by Broadcom folks though. There's only so much us mere mortal users know about the internals of Fusion -- and we do get issues that only that deep internals knowledge can help solve.
------------------------------
- Paul (technogeezer)
Original Message:
Sent: Jan 26, 2025 08:55 PM
From: Fred Macondray
Subject: VM encrypted itself, don't know the password (part.2) (after 13.5 update)
We set the encryption password, but it doesn't say if the key is in there. Would there be a separate entry?
We also have a veeam backup. I didn't realize the key was not stored with the VM Bundle.
I will give making a new VM a try. I saw a post about doing that and have been preparing.
I'd still love to know what was causing that dialog to behave that way. Correct logs uploaded here.
BTW, your presence here makes me hopeful that the new "self support" system might be OK!
Thanks
Fred
Original Message:
Sent: Jan 26, 2025 07:52 PM
From: Technogeezer
Subject: VM encrypted itself, don't know the password (part.2) (after 13.5 update)
All of the vmware-vmfusion*.log files are from 2022. Can you make sure that you've posted them from the /Home/username/Library/Logs/VMware Fusion folder -- the Library folder of the user that's running Fusion.
I'd not trust an OVF export of a VM to be able to restore it -- especially if the source VM has a TPM device.
It might be better to re-create this VM. Since the VM is not fully encrypted, the .vmdk files are not encrypted. Create a new Windows 11 VM (Create a custom virtual machine in the "Select an installation source dialog"). Make it a Windows 11 VM so it will ask for encryption (partial encryption should be your choice). But instead of creating a new virtual disk, use an existing virtual disk. Locate the broken VM's virtual disk in the file selection dialog that appears (the dialog will let you drill into an existing VM's bundle file to find the .vmdk file),. Select the broken VM's virtual disk and make sure you elect to elect to make a copy of it for the new VM. That'll leave the original vmdk files intact.
You may need to validate the user's login upon startup of this new VM since the TPM is reset. You won't be able to restore the old TPM from backup since it's encrypted with the old encryption method and keys.
------------------------------
- Paul (technogeezer)
Original Message:
Sent: Jan 26, 2025 04:00 PM
From: Fred Macondray
Subject: VM encrypted itself, don't know the password (part.2) (after 13.5 update)
More details would help:
- What is the exact version of Fusion you're using?
- What's the macOS version and Mac model that you're using?
- What build of Windows 11 is being used in the VM?
- Can you provide details on how the virtual machine is configured. Attaching the .vmx file for the VM would help (found in the VM's bundle).
- Is the VM partially or fully encrypted?
- I'm assuming that since you say you have the VM's encryption password, you did not create this VM on Fusion 12 and used the "hack" of editing the .vmx file to enable a (broken) "partial encryption" preview feature?
- How is the virtual disk is configured (size and if it's configured to break up the disk into pieces). A file listing (using the
ls-alR path-to-vmwarevm-file in a Terminal window, not a screen shot of the Finder window) would be helpful.
- Any snapshots active for the VM?
- Is the VM stored on a folder that's configured for cloud storage sync'ing (e.g. OneDrive, iCloud, Google Drive, Dropbox), or on anything other than a local drive formatted as HFS+ or APFS?
- What are the exact steps that the user is performing?
- Trying to launch the VM. Before pressing play, the message to upgrade encryption comes up. Choosing either button crashes Fusion.
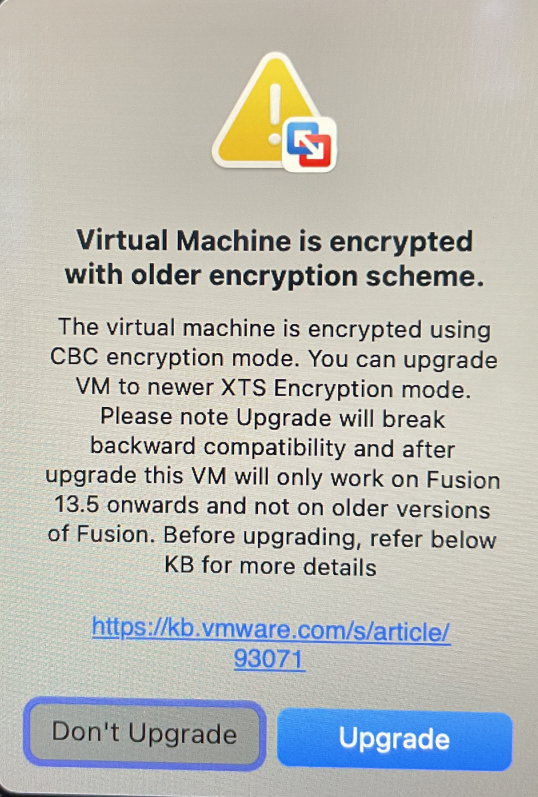
- What exactly was the crash message.
- No message, it just quits.
- Can you provide Fusion logging? (the ~/Library/Logs/VMware Fusion/vmware-vmfusion*.log files and the vmware*.log files found in the VM's bundle)
- Is the encryption crashing Fusion or does the encryption complete and then the VM crashes?
- I think it's a pre-OS issue
- Is there sufficient disk space to hold a complete copy of the VM during the re-encryption process?
- I believe so, there's 1.3TB free
Note that I did attempt removing the TPM chip but it had no effect on the message last night, but today I'm getting an unable to load error:
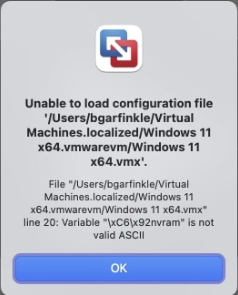
I imagine I will need to restore those files that were encrypted using the TPM?
I have a TAR Export and an OVF export I can use. Should I replace the TPM and the .nvram, vmss, mvx and vmsn files?
Thanks for your thorough reply!
Fred
Original Message:
Sent: Jan 26, 2025 12:21 PM
From: Technogeezer
Subject: VM encrypted itself, don't know the password (part.2) (after 13.5 update)
@Fred Macondray
"Fusion crashed" is a very vague description.
More details would help:
- What is the exact version of Fusion you're using?
- What's the macOS version and Mac model that you're using?
- What build of Windows 11 is being used in the VM?
- Can you provide details on how the virtual machine is configured. Attaching the .vmx file for the VM would help (found in the VM's bundle).
- Is the VM partially or fully encrypted?
- I'm assuming that since you say you have the VM's encryption password, you did not create this VM on Fusion 12 and used the "hack" of editing the .vmx file to enable a (broken) "partial encryption" preview feature?
- How is the virtual disk is configured (size and if it's configured to break up the disk into pieces). A file listing (using the
ls-alR path-to-vmwarevm-file in a Terminal window, not a screen shot of the Finder window) would be helpful.
- Any snapshots active for the VM?
- Is the VM stored on a folder that's configured for cloud storage sync'ing (e.g. OneDrive, iCloud, Google Drive, Dropbox), or on anything other than a local drive formatted as HFS+ or APFS?
- What are the exact steps that the user is performing?
- What exactly was the crash message.
- Can you provide Fusion logging? (the ~/Library/Logs/VMware Fusion/vmware-vmfusion*.log files and the vmware*.log files found in the VM's bundle)
- Is the encryption crashing Fusion or does the encryption complete and then the VM crashes?
- Is there sufficient disk space to hold a complete copy of the VM during the re-encryption process?
It's generally safe to remove the encryption on a Windows 11 VM. But you need to remove the TPM device first. Then decrypt. Then re-encrypt the VM and add the TPM device back in. (Windows 11 doesn't like to run without a TPM device). This is usually not much of a problem -- except if you have BitLocker enabled in Windows. You'll shouldn't try to remove a TPM device from a VM with BitLocker enabled without making sure you have the BitLocker recovery key (either printed, saved to a thumb drive, or available in the user's Microsoft Account). Removing a TPM device is like swapping motherboards on a PC - the TPM is wiped and you'll need that recovery key to get access to the BitLocker enabled VM once the TPM is added back to the configuration.
------------------------------
- Paul (technogeezer)
Original Message:
Sent: Jan 25, 2025 09:25 PM
From: Fred Macondray
Subject: VM encrypted itself, don't know the password (part.2) (after 13.5 update)
Greetings,
We're in a situation that seems related to this post. Fusion 13, Windows 11 VM. We do have the password, however the message alerting the user to the need to upgrade the encryption from CBC to XTS both now produce a predictable crash of Fusion.
The VM is confiugred only for TPM related use, drives are not encrypted.
If we cannot get past the error, we may need to try removing the TPM and Encryption. I'm not sure this is safe.
We are now restoring the system to Hyper-V as a quick user access solution, but I would really like to know how to make that upgrade dialog work.
Any ideas?
Thanks in Advance,
Fred
Original Message:
Sent: May 12, 2024 11:18 PM
From: Technogeezer
Subject: VM encrypted itself, don't know the password (part.2) (after 13.5 update)
I'm grasping at straws a bit here.
Was this VM created fresh and installed from ISO, or was it a converted VHDX file (a Windows Insider Preview).
Do you have a copy of the VM from before the upgrade? If so, it would be interesting to examine both the .vmx file and the VMDK fike descriptors to get some kind of indication of why the VM got automatically encrypted.
Did this VM have a TPM device before upgrade?
Did you open a support case with VMware? This isn't an official VMware tech support forum.
------------------------------
- Paul (technogeezer)
Original Message:
Sent: May 12, 2024 07:57 AM
From: Jacinto Perez Calavera
Subject: VM encrypted itself, don't know the password (part.2) (after 13.5 update)
I have the same issue. vmware fusion 13.5.1 (23298085) and Windows 11.
I can't believe that upgrading a software product encrypts the hard disk and doesn't provide/save the password. I followed the suggestions of VMWARE to encrypt, and I have been trapped in a nightmare, without any manufacturer solution!!!.
I'm very disappointed with the product and with the support. It's highly below a professional quality standard.
Original Message:
Sent: Oct 24, 2023 04:21 PM
From: digifox55
Subject: VM encrypted itself, don't know the password (part.2) (after 13.5 update)
Hello, I read these topics: VM-encrypted-itself-don-t-know-the-password and VM-asking-for-password but I still need help.
I updated Fusion 13 Pro from v. 13.0.2 to 13.5 a few days ago. I have a M2 MacBook with Sonoma, and run several vms of Win11 ARM.
After updating I noticed that I could only open my default vm file, all the other vms raised a popup saying "The virtual machine "Windows 11 64-bit arm" is encrypted. You must enter its password to continue.". I am sure I had never enabled encryption before. In fact I could close and reopen my default vm with no password prompt.
After noticing that my def-vm wasn't properly scaling the resolution anymore (no way to stretch it to fit it to the window), I decided to downgrade to 13.0.2. As soon as I went back to 13.0.2 not only my other-vms kept asking me the password, but also my def-vm has become encrypted with the same prompt. I went back to 13.5 again and def-vm is still encrypted.
Any ideas to recover my instances? Could a full macos time-machine backup lead me to a point where the vms aren't encrypted?
Thank you so much in advance!