Wiz Research team discovered a series of unauthenticated Remote Code Execution vulnerabilities in Ingress NGINX Controller for Kubernetes. Today the Ingress-nginx team released a new version fixing critical security issues. The most critical one is the CVE-2025-1974: ingress-nginx admission controller RCE escalation.
Under certain conditions, an unauthenticated attacker with access to the pod network can achieve arbitrary code execution (RCE) in the context of the ingress-nginx controller. This could lead to the disclosure of Secrets accessible to the controller. The CVE-2025-1974 means that anything on the Pod network has a good chance of taking over your Kubernetes cluster, with no credentials or administrative access required.
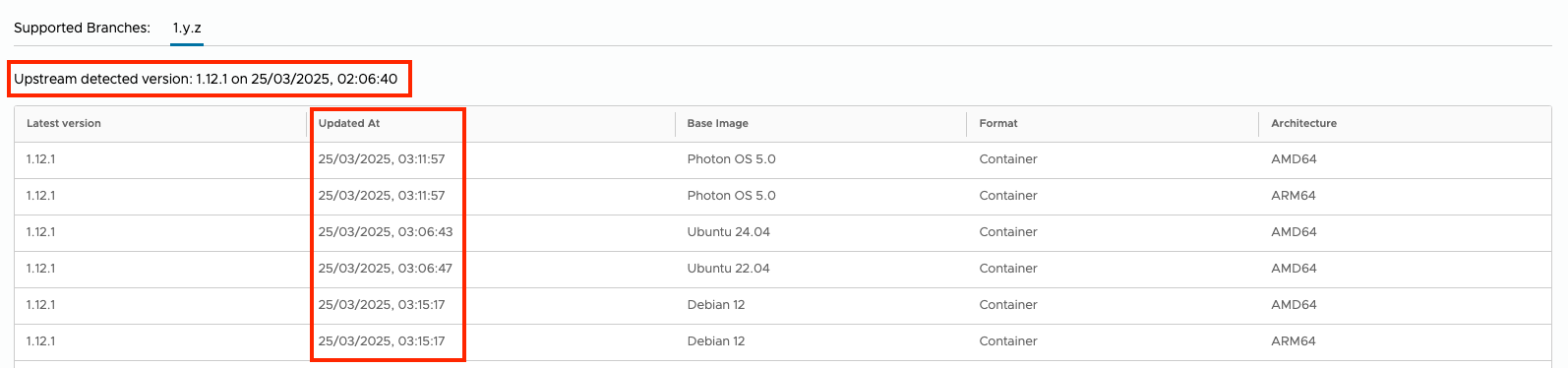
The fixed version is Nginx Ingress Controller 1.12.1 and it was already released just 2 hours after the official release in Bitnami DockerHub, Bitnami Premium and Tanzu Application Catalog in all the supported Distros like PhotonOS, RHEL UBI, Debian and Ubuntu.
If you use ingress-nginx, you should take action immediately and update it in your K8s clusters to keep yourself safe.
The Bitnami Helm chart for Nginx Ingress Controller is not affected if it was deployed using the default parameters for the installation. The “admissionWebhooks” property is not enabled by default; that is the feature affected by this CVE, but it is strongly recommended to update it to address the rest of CVEs fixed in v1.12.1 (CVE-2025-1097, CVE-2025-1098, CVE-2025-24514). For more information please check the Wiz Research post.
In any case, the Bitnami Helm chart was already released v11.6.12 with the container image update after the official release and customers. Bitnami Open Source users, Bitnami Premium and Tanzu Application Catalog customers are able to upgrade their installations in a simple way via Helm.
#Security
#Kubernetes
#bitnami