This issue has me confused. I've tried a lot of troubleshooting steps. I'm just trying to create a rule to allow all Remote Desktop traffic.
At first I followed the Symantec guide to allow RDP, and targeted the MSTSC executable. This did not work, and showed the traffic was blocked. So, to test, I've created a rule to explicitly allow all traffic between my computer (202) and the test computer (162):
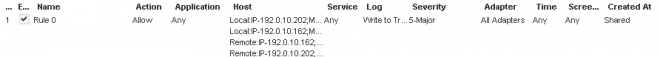
I make both computers update Policy via Symantec Endpoint Troubleshoot, and still get:
3/21/2018 2:29:24 PM Blocked 15 Incoming TCP 192.0.10.202 <Mac> 18007 192.0.10.162 <Mac> 3389 C:\Windows\System32\svchost.exe NETWORK SERVICE NT AUTHORITY Default 3 3/21/2018 2:29:13 PM 3/21/2018 2:29:22 PM Block all other IP traffic and log
As seen there, the default "Block All other IP Traffic" rule takes priority. The only way I can get RDP to be successful is by disabling that rule, or disabling the Sym Firewall. Both are not acceptable solutions.