What Is Endpoint Security?
Any device that is connected to an organization’s network systems is known as an endpoint.
Endpoint security is the protection and monitoring of end-user devices, such as smartphones, laptops, desktop PCs and POS devices, and network access paths, such as open ports or website logins. It goes beyond antivirus tools and includes the use of security software, like Endpoint Detection and Response (EDR) tools, on central servers as well as tools on the device itself, such as ad blockers.
Tools used for endpoint protection typically include features for the detection of intrusions, such as bypassed firewalls, and behavior analysis, such as login attempts by multiple users from the same IP address. EDR security is vital to the protection of a company’s data as it secures the entry points that attackers might exploit to gain access to valuable information.
Because of the outbreaks of various cyberattacks such as WannaCry ransomware, fileless malware, and more, network security has gained the attention that it actually deserves. Enterprises are now well-aware of the potential damage that can occur when hit by any such cyberattacks. As a result, companies have started deploying advanced security measures, powerful firewalls, and solid monitoring systems for networks and datacenters.
Endpoint security proves much more diverse than it initially appears. Far from just protecting your digital perimeter, these solutions protect huge lengths of your IT environment. In fact, you consider the components of the solutions as types of endpoint security; these components can serve as individual solutions for your enterprise.
However, endpoint protection platforms serve as a way to enjoy the benefits of these types of endpoint security. Usually, this better suits your enterprise in the modern cybersecurity era—missing a crucial component could spell doom for your business.
Here are the 11 types of Endpoint Security you need to know:
1. Internet of Things (IoT) Security
IoT devices are becoming more ubiquitous in enterprise infrastructures as they help facilitate communications and business processes. Unfortunately, IoT devices generally inherent endpoint security. Manufacturers don’t prioritize IoT security in their products or place poor protections on those devices.
To combat this issue, providers offer IoT security as one of the types of endpoint security for enterprises. In fact, these solutions work to improve visibility in IoT devices, provide a consistent and easily upgradable layer of cybersecurity, and close security vulnerabilities into the network.
2. Antivirus Solutions
Perhaps one of the most popular and well-recognized types of endpoint security, antivirus solutions still provide critical capabilities. These include anti-malware capabilities.
As such, enterprises can protect themselves against signature-based attacks, which still arise on occasion. Additionally, antivirus solutions can scan files for malicious threats via consulting against threat intelligence databases. Enterprises can install antivirus solutions directly onto their endpoints to identify unknown signatures.
However, antivirus solutions often prove limited in defending against more advanced cyber threats. Moreover, enterprises often rely too much on antivirus alone for their digital perimeter. Of the types of endpoint security, this one certainly needs the support of others.
3. Endpoint Detection and Response
A darling among the other endpoint security tools, EDR offers a capability which fits with the detection-mitigation model of modern cybersecurity. Indeed, EDR solutions continuously monitor all files and applications entering your enterprise’s endpoints. Additionally, EDR solutions can offer granular visibility, threat investigations, and detection of fileless malware and ransomware. Also, EDR provides your investigation teams with alerts for easy potential threat identification and remediation.
4. URL Filtering
URL filtering works to restricts web traffic to trusted websites; in turn, this prevents users from accessing malicious websites or websites with potentially harmful content. As an added bonus, URL filtering can prevent surreptitious downloads on your network, granting you more control over what gets downloaded where and by whom.
5. Application Control
Unsurprisingly, application control does exactly what it says on the tin; it controls applications’ permissions, ensuring strict restrictions on what they can or cannot do. To accomplish this, it uses whitelisting, blacklisting, and gray-listing to prevent malicious applications from running and compromised applications from running in dangerous ways. As enterprises continue to embrace the cloud and the potential of third-party applications in their business processes, this proves incredibly important.
6. Network Access Control
Surprisingly, network access control overlaps with identity and access management. After all, its primary focus is on securing access to network nodes. As a result, network access control determines what devices and users can access and do what on your network infrastructure. Among the types of endpoint security listed here, this one emphasizes the importance of firewalls and data limitations the most.
7. Browser Isolation
The threat facing web browsers can prove overwhelming to comprehend on a first look: surprise downloads, zero-day attacks, ransomware, cryptojacking malware, and malicious browser-executable code. Moreover, these merely skim the surface of potential cyber attacks. Browser isolation works to execute browsing sessions in isolated environments where it cannot reach valuable digital assets. Therefore, activity remains restricted to isolated environments and safe interactive media streams. Additionally, the tool destroys web browser codes after the user finishes browsing.
8. Cloud Perimeter Security
Endpoint security can no longer merely concern itself with your users’ devices. In addition, it must form a protective perimeter around your cloud environments and databases. Cloud providers are not responsible for your enterprise’s cybersecurity; hackers can target your cloud-stored assets with impunity unless you intervene.
Cloud perimeter security allows your enterprise to harden your cloud infrastructure against incoming threats.
9. Endpoint Encryption
Among the types of endpoint security, encryption often suffers from the most neglect. Yet its capabilities contribute meaningfully to any business’ digital perimeter. It prevents issues such as data leaks (whether intentional or not) via data transfer by fully encrypting that data. Specifically, it encrypts data stored on endpoints.
10. Secure Email Gateways
Email constitutes the main means of data traffic entering and exiting your digital network. Thusly, hackers exploit emails to conceal and transmit their attacks through emails more than any other attack vector. In fact, they could use email as their malware-delivery system as much as 90% of the time if not more.
Secure email gateways monitor incoming and outgoing messages for suspicious behavior, preventing them from being delivered. They can be deployed according to your IT infrastructure to prevent phishing attacks.
11. Sandboxing
A “sandbox” serves as an isolated and secure digital environment which perfectly replicates your typical end-user operating system. As such, it can contain potential threats for observation. Your IT security team can then determine their intentions before allowing them into the network proper. This tool can help contain zero-day threats and works well against zero-day attacks.
Endpoint security is of vital importance, and any negligence in doing so can prove fatal to an Enterprise. With employees relying more on smartphones and home PCs or laptops to connect to the organization’s network to proceed with their work, a centralized security solution that works within an organization will no longer serve the purpose of securing the endpoints.
Here are the best practices that should be followed by Enterprise Organizations:
1. Stop usage of Common Passwords and use multi-factor authentication
Passwords are your first line of security defense. Cybercriminals attempting to infiltrate your network will start by trying the most common passwords.
BEST PRACTICE: Ensure use of long (over 8 characters), complex (include lower case, upper case, numbers and non-alpha characters) passwords.
If you’re still relying on usernames and passwords, your systems are not secure.
All endpoints in the organization must follow multi-factor authentication such as one-time passwords, biometrics such as fingerprint, face, or retina scanning along with the regular username and passwords.
2. Secure Every Entrance
All it takes is one open door to allow a cybercriminal to enter your network. Just like you secure your home by locking the front door, the back door and all the windows, think about protecting your network in the same way.
Consider all the ways someone could enter your network, then ensure that only authorized users can do so.
- Ensure strong passwords on laptops, smartphones, tablets, and WIFI access points.
- Use a Firewall with Threat Prevention to protect access to your network.
- Secure your endpoints (laptops, desktops) with security software such as Anti-virus, Anti-SPAM and Anti-Phishing.
- Protect from a common attack method by instructing employees not to plug in unknown USB devices.
3. Define, Educate and Enforce Policy
Have a security policy and use your Threat Prevention device to its full capacity. Spend some time thinking about what applications you want to allow in your network and what apps you do NOT want to run in your network. Educate your employees on acceptable use of the company network. Make it official.
Then enforce it where you can. Monitor for policy violations and excessive bandwidth use.
- Set up an Appropriate Use Policy for allowed/disallowed apps and websites.
- Do not allow risky applications such as Bit Torrent or other Peer-to-Peer file sharing applications, which are a very common methods of distributing malicious software.
- Block TOR and other anonymizers that seek to hide behavior or circumvent security.
- Think about Social Media while developing policy
4. Be Socially Aware
Social media sites are a gold mind for cybercriminals looking to gain information on people, improving their success rate for attacks. Attacks such as phishing, spearphish or social engineering all start with collecting personal data on individuals.
- Educate employees to be cautious with sharing on social media sites, even in their personal accounts.
- Let users know that cybercriminals build profiles of company employees to make phishing and social engineering attacks more successful.
- Train employees on privacy settings on social media sites to protect their personal information.
- Users should be careful of what they share, since cybercriminals could guess security answers (such as your dog’s name) to reset passwords and gain access to accounts.
5. Keep your systems updated
Keeping your systems updated in terms of hardware and software is one of the most fundamental measures to be taken in order to avoid cyberattack. Yet, a considerable number of cyberattacks and issues are being reported due to outdated systems globally. Keeping systems updated and adapting to the market is one of the best and easy ways to stay safe.
Apart from updating central software and network systems, companies need to make sure that all end devices’ firmware must be updated to the latest version. If this is left to the users to update their devices, they may skip this or put it off. Therefore, companies either have to force their employees to update the devices or simply roll out forced updates to the devices. This makes sure that all devices in an enterprise are updated, leaving no room for compatibility issues or malware attacks. Managing endpoints from a central location will make this process easy.
6. Encrypt Everything
One data breach could be devastating to your company or your reputation. Protect your data by encrypting sensitive data and make it easy for your employees to do so.
Ensure encryption is part of your corporate policy.
- Sleep easy if laptops are lost or stolen by ensuring company owned laptops have pre-boot encryption installed.
- Buy hard drives and USB drives with encryption built in.
- Use strong encryption on your wireless network (consider WPA2 with AES encryption).
- Protect your data from eavesdroppers by encrypting wireless communication using VPN (Virtual Private Network).
7. Segment Your Network
A way to protect your network is to separate your network into zones and protect the zones appropriately. One zone may be for critical work only, where another may be a guest zone where customers can surf the internet, but not access your work network.
Segment your network and place more rigid security requirements where needed.
- Public facing web servers should not be allowed to access your internal network.
- You may allow guest access, but do not allow guests on your internal network.
- Consider separating your network according to various business functions (customer records, Finance, general employees).
8. Maintain Your Network and Disable ports you don’t need
Your network, and all its connected components, should run like a well-oiled machine. Regular maintenance will ensure it continues to roll along at peak performance and hit few speed bumps.
- Ensure operating systems of laptops and servers are updated (Windows Update is turned on for all Systems).
- Uninstall software that isn’t needed so you don’t have to check for regular updates (e.g., Java).
- Update browser, Flash, Adobe and applications on your servers and laptops.
- Turn on automatic updates where available: Windows, Chrome, Firefox, and Adobe.
- Use an Intrusion Prevention System (IPS) device to prevent attacks on non-updated laptops.
Unsecured or open ports serve as an easy means of intrusion and have been the entry point for many recent and destructive cyberattacks. Every organization must secure all network ports and disable ports that are not in use. Every endpoint must be port restricted and every port must be secured to make sure end users are using only what is needed. Endpoint devices such as Bluetooth/infrared devices and modems must be disabled when not in use.
9. Endpoint security: Enforcing least privilege
Enforcing privilege security on endpoints should be a fundamental part of any business’s essentials. Applying advanced security measures and firewalls are now not enough to secure endpoints in a corporate network. To stay secure, enterprises need to follow a more sophisticated approach, and the principle of least privilege is one such effective method of securing the endpoints.
By following the principle of least privilege, only the minimum privileges or permissions are given to the employees. This ensures that not everyone is provided with administrative access, which they don’t really require. Having more than required privilege poses a threat of numerous errant or malicious actions, which can be performed at an endpoint. There is also a possibility that devices having administrative rights can be used as a means of corrupting the entire organization’s network system. Enforcing least privilege will also contain and reduce the impact of cyberattacks on endpoints.
10. Cloud Caution
Cloud storage and applications are all the rage, but be cautious. Any content that is moved to the cloud is no longer in your control. And cybercriminals are taking advantage of weaker security of some Cloud providers.
- When using the Cloud, assume content sent is no longer private.
- Encrypt content before sending (including system backups).
- Check the security of your Cloud provider.
- Don’t use the same password everywhere, especially Cloud passwords.
11: Don’t Let Everyone Administrate
Laptops can be accessed via user accounts or administrative accounts. Administrative access allows users much more freedom and power on their laptops, but that power moves to the cybercriminal if the administrator account is hacked.
- Don't allow employees to use a Windows account with Administrator privileges for day-to-day activities.
- Limiting employees to User Account access reduces the ability for malicious software (better known as malware) to do extensive damage at the "administrator" privileged level.
- Make it a habit to change default passwords on all devices, including laptops, servers, routers, gateways and network printers.
12. BYOD Policy
Start with creating a Bring-Your-Own-Device policy. Many companies have avoided the topic, but it’s a trend that continues to push forward.
It comes back to educating the user.
- Consider allowing only guest access (internet only) for employee owned devices.
- Enforce password locks on user owned devices.
- Access sensitive information only through encrypted VPN.
- Don’t allow storage of sensitive information on personal devices (such as customer contacts or credit card information).
- Have a plan if an employee loses their device.
Best practices for Endpoint Security Solutions covering:
- Antivirus
- Device control
- Host-IPS
- Behavioral protections
- Location awareness
- Network access control
- Application control
The first tip pertains to the select of an endpoint security solution: regardless of what tool(s) you select, look for native support of Active Directory (AD) and the ability to support the types of devices that you have. This will make it so much easier to control everything from one vantage point.
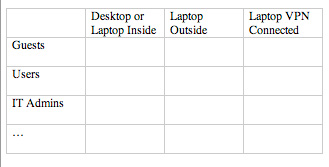
1. Identify Users/Workstations
AD security groups are by far the most versatile for which to match your security policy. A simple and basic approach is to define the following groups in AD:
-
- Workstations: laptops/desktops
- Security groups: IT admins/users/guests
Of course, you can define additional groups as needed to provide more granularities with your security policies.
2. Document your Security Policies in a table
To help complete the above table, here are some best practices for each endpoint security project. Keep in mind that you will want to review them individually but then combine them into a single set of policies that can work hand-in-hand together to provide the best possible protection and control.
3. Best practices for Antivirus
-
- Schedule a full scan once a week as a minimum, preferably at lunch time. For the laptops, a full scan should be triggered every time they make a connection to the corporate network.
- Enforce full scans on removable devices when each is plugged in.
- The AV signature updates should be performed every three hours.
- Configure the workstation to directly download signature updates from the AV vendor's public online server(s) in case your internal AV server is offline due to hardware or software issues.
4. Best practices for Device Control
-
- Wi-Fi must be disabled inside the corporate network. This should also be applied to all workstations, laptops and servers. Wi-Fi USB keys can be found everywhere for $20, and these need to be controlled.
- Modems, Bluetooth and infrared must be disabled to prevent any communications that are not controlled by corporate policy.
- U3 features in USB keys must be disabled as they can be used as a falsely-detected (fake) CD-ROM drive, enabling malware to corrupt this component to run automatically on the workstation. When browsing removable devices on the endpoint, the U3 CD-ROM can be mistaken to be the real CD-ROM drive.
- Audit all devices that are plugged in and capture all activity when files are written to removable devices. This will allow you to monitor the extraction of information, giving you a view into how your USB devices are used. With this information, additional policies can be set based on your findings.
- Block access to any executables and scripts from removable devices and the CD or DVD drives. This will prevent any malware from running as a result of any unknown vulnerability being exploited before it gets patched.
- Encrypt all of the data written to high-volume removable storage devices such as CD, DVD and USB backup volumes.
All these controls and restrictions must have the capability to be temporarily disabled. This should be available through a built-in challenge/response or Captcha. This ensures that the temporary exception is controlled by the IT staff and can be managed to exist for a specified/limited amount of time.
5. Best practices for Host-IPS and Behavioral Protections
-
- Keylogger protection: Most malware programs include some form of a keylogger engine to recover passwords, credit card numbers and other personal data. Be sure to enable keylogger protection as part of your host IPS policy.
- Network monitoring: Set the policy to monitor any application attempting to make network connections. Unauthorized connections can help to detect a malware process attempting to call home.
- Rootkit protection: Using a predefined whitelist of the drivers loaded by Windows, you can detect malware that appears on the surface to be valid but in fact has been signed with stolen certificates from the driver's hardware or software vendor (such as CF Stuxnet with the Realtech certificate).
- Prevent DLL injections: The favorite technique used by malware programs to prevent the antivirus product from removing them is to inject themselves in a running DLL. Antivirus can't remove or quarantine a DLL that has already been loaded. Typically, malware will load itself in system processes like winlogon.exe or explorer.exe.
Using a learning mode or testing mode for intrusion prevention and behavioral protections is mandatory in order to be able to conduct a test-drive of the protection such that exceptions can be made for false-positives. This improves the level of trust when deploying the software as well, especially when it comes time to upgrade or install a new application as this is the action that will mostly trigger a false-positive.
Buffer overflow protections are now mandatory. A good example is the recent vulnerabilities targeting Microsoft Windows and Adobe Acrobat. The timeframe to receive the fix can be up to one month when exploit in the wild are on Internet in a matter of hours.
6. Best practices for Application Control
Cyber thieves will take advantage of the areas of your operating system that change frequently to support legitimate applications. Therefore, you must secure the windows registry to prevent the auto-load of malware:
-
- AutoRun keys
- Internet explorer ActiveX and module
- Injection of DLL in the system (winlogon, etc.)
- Windows services
- Drivers
Prevent applications from copying executables or scripts to network shares. This will prevent worms from spreading inside the corporate network.
Prevent "Print Screen" and "Copy/Paste" capabilities within sensitive applications such as financial application and health record applications.
Enforce a rule that only allows specific applications to save files on a remote server.
7. Best practices for Location Awareness
The level of security must not only be based on the user that is currently logged in, but also on the location from which he is connecting and the context of his connection. This includes the type of connection, the level of security with the connection, and so on.
In the case of a laptop, the machine should possess three different policy levels depending upon its location: inside the corporate network, outside the corporate network, or connected to the Internet through a VPN. Other connection types may be blocked, such as attempting to connect to the Internet through an unsecured Wi-Fi connection that is not going through the corporate VPN.
To be able to determine the location, you need a solution that can detect the network interfaces that are activated (this is mandatory for VPN Control); can collect the IP information for the machine (IP address, DNS, etc…); and can use the local and network Active Directory information to determine the machines type, role, groups and so forth. It is dangerous to use a simple server presence to test the machine's location because if the server goes offline the location will no longer be valid and all your workstations will be operating under a false policy as if they were not connected to the corporate network.
Here is an example of how location settings will match most companies:
-
- Location inside: With the LAN interface only activated, check that the workstation is authenticated with LDAP
- Location VPN: With the VPN interface activated and the right IP address from the VPN subnet.
- Location Outside: neither inside nor VPN.
With these three locations identified, the following policies can be applied:
-
- Policy inside: White list network interface to only allow the LAN interface. This prevents any unexpected (potentially malicious or otherwise insecure) bridge across another network interface.
- Policy VPN: Limit network incoming/outgoing connections to the minimum required. This helps with security, of course, but also helps to save on VPN bandwidth.
- Policy outside: The network connection should be available for a limited time and only for purposes of establishing a VPN connection. The scenario of a user connected through a hotspot must first be tested. Then, the user should be allowed a window of opportunity (a good amount of time is three minutes) where they can open a Web connection (http/https) in order to pay for and authenticate to the hotspot portal (such as that of their hotel). Once authenticated to the hotspot, the VPN connection can be established.
8. Best practices for Network Access Control (NAC)
In order to put the basic NAC capabilities in place, 802.1x is the core layer that will prevent unauthorized workstations from connecting to the corporate network. The easiest way to accomplish this for a Windows-based environment is through Microsoft Active Directory and its built-in OS supplicant that is fully operational beginning with Windows XP SP2.
With 802.1x in place, the next step is to implement a network-based NAC implementation such as Cisco's NAC, Microsoft's NAP or Juniper's UAC. This will provide the necessary mechanisms to establish a workstation with in a VLAN based on its status (clean, quarantined, guest system, etc.).
Finally, an endpoint protection technology compatible with your NAC implementation rounds out the NAC capabilities as the endpoint agent will provide the in-depth health status of the workstation in addition to helping with the quarantining, cleansing/repair, and control of the workstation.
Here are the controls required to ensure a good level of NAC-based security policy:
-
- Check that the workstation has all of the patches for the operating system and applications that could introduce vulnerabilities into the network environment (Microsoft Office, Adobe Acrobat and Flash, etc.)
- Check that the antivirus status and signatures are up to date and that the system has performed routine scans with the latest signatures.
- Check for the deployment/management (or lack or misconfiguration) of software installed and running (Microsoft SMS, Landesk, Altiris, etc.).
If a workstation fails on any one or all of the above checks, it should be placed in quarantine. While in quarantine, it should be limited to:
-
- Receiving a notification explaining the status of the workstation to the user and the administrators should be notified by e-mail.
- If 802.1x is available, the workstation should be placed within a dedicated quarantine virtual LAN.
- It should be limited to "Read-only" on USB and other removable devices (that could be used to gain access via a wireless network, for example).
- Network connections must be restricted to only allow for remediation activities, updates (items such as patches and signatures updates), and notifications (such as the e-mail gateway).
- E-mail and Web browser applications should deny access to any files being downloaded, opened or uploaded in order to prevent worm spreading but allow the employee to work with his mail.
- The endpoint protection product should provide automatic remediation, repairing and cleaning of the workstation without any administrator interaction, automatically moving the workstation from the quarantine VLAN to the production VLAN once complete.
In selecting an endpoint protection solution, the NAC health check should be fast -- less than a minute. Additionally, the endpoint protection's NAC capabilities should load immediately after the system is loaded. Finally, the endpoint protection product should provide the same NAC-level of protections for the endpoint even when the endpoint is not connected to a corporate network or VLAN.
Best Practices for Employees from Enterprise / Corporates / Small Business:
- Always lock your computer before leaving your desk.
- Use a strong password and change the password periodically.
- Ensure encryption is enabled in the official asset.
- Ensure that the antivirus agent is updated.
- Ensure that the proxy (URL filtering) solution is installed and enabled.
- Avoid connecting the official asset to unsecure Wi-Fi / internet connection.
- Do not connect any unauthorized or unapproved devices to official systems.
- Do not connect any external storage media without performing an antivirus scan.
- Keep your laptops/desktops updated with the latest security patches.
- Use only approved and licensed applications, remove unwanted software / plugins.