Hi,
This article is a How-To on how to enable, create and implement custom file type signatures in DLP.
In this example I'm going to use a scenario I've recently been working on which proved to be an interesting challenge, triggering DLP actions against standard 7Zip files; but also triggering seperate actions against encrypted password protected 7Zip files.
Firstly we will look at creating the custom file signature script which will be used to instruct DLP to detect a specific unique signature, which is referred to as a magic byte unique to every file type.
1. Create a new folder directory on the local machine which will be used for testing.
2. Create multiple notepad documents with varying text. (Blank documents will be misleading and will likely fail this exercise, must have multiple documents of the same type.)
3. Using 7zip create a few test files both non password protected and password protected for analysis.

4. Install the Symantec tool called File Analyzer from the below link:
https://www.symantec.com/connect/downloads/file-analyzer
5. Install to a directory of your choice and then browse to the install location.
6. Run analyzer_gui.exe
7. Once File Analyser is running select the directory location of your test files and enter .* into the File Name Filter box to show all files.
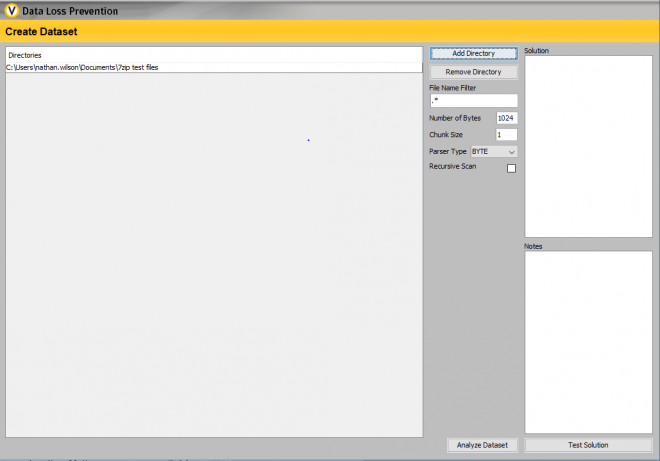
8. Click Analyze Table Data and select the .7z tab to filter out your example .txt files.
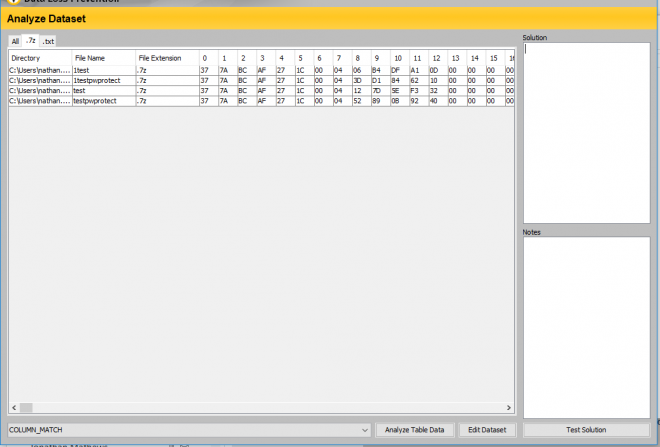
9. We now need to look at each collumn and identify the 'magic byte' mentioned earlier; this can be in the first byte or the last, but will always match the the file type created. For example a password protect .7z will match another password protected .7z; however will not match a standard .7z file.
10. Once reviewed you should have found the below magic byte for .7z (This will be different for all file types)
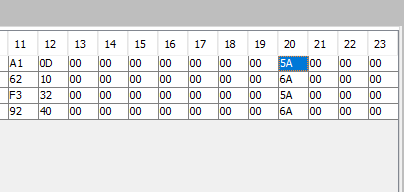
As you can see in byte 20, there's 2 matches. These matches are for a standard .7z file (5A) and a password protected .7z file (6A) this number is unique to this file type.
11. Now we have to start looking at a scripted solution to tell DLP to look at this byte and any sanity checks you'd like to include. At this stage in the guide I'd recommend using the Symantec guide to create the script but I will also provide a translation of mine in laymans terms.
https://support.symantec.com/en_US/article.TECH220442.html
My script for standard .7z files: ## Please Note, this software is not case sensitive, but DLP is; Int1 + int1 will NOT match. ##
$Int1 = getHexStringValue('006A');
$Int2 = getHexStringValue('377ABCAF');
$Int3 = getBinaryValueAt($data, 0x13, 2);
$Int4 = getBinaryValueAt($data, 0x0, 4);
assertFalse ($Int1 == $Int3);
assertTrue($Int2 == $Int4);
Translation:
Int1 = Tells the script to use '006A' as the magic byte to match somewhere in the file.
Int2 = Tells the script to use '377ABCAF' as a byte comparison somewhere in the file.
Int3 = This points the script at a hexidecimal location within the file, 0x13 in Hex is 19, so the script will look at Byte 19 and the following byte ,2 tells the script to look at 19 and the next byte. Which in the situation of .7z is 006A.
Int4: This points the script at the hexidecimal location of 0x0 which is 0, and tells it to read the first 4 bytes 0-3 as instructed by the ,4.
AssertFalse: This compiles the results of Int1 and Int3, and states if this matches 006A then it matches the script requirement but catagorises this as a false match.
AssertTrue: This compares Int2 and Int4 and if they match it matches the scripts requirements.
Example of the script working in File Analzer:
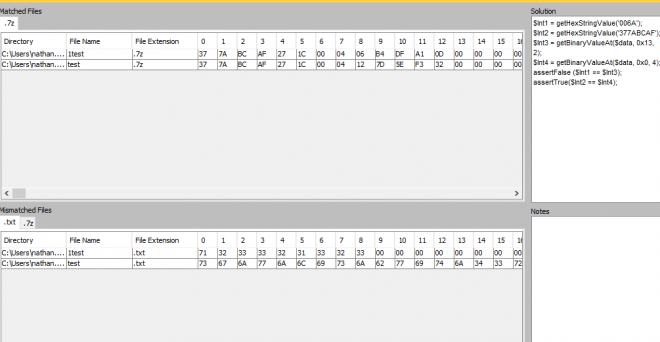
As you can see, it has matched the non password protected .7z files as they meet the scripts requirements, and has filtered out to Mismatched the password protected files as they do not meet the script requirements.
Now you have an understanding of the scripting logic below is the script used to identify password protected .7z files which is very similair to the above:
$Int1 = getHexStringValue('006A');
$Int2 = getHexStringValue('377ABCAF');
$Int3 = getBinaryValueAt($data, 0x13, 2);
$Int4 = getBinaryValueAt($data, 0x0, 4);
assertTrue ($Int1 == $Int3);
assertTrue($Int2 == $Int4);
12. We now need to enable custom file extensions within DLP, as they are not natively enabled.
13. Please UNC/PUTTY to your DLP host operating system and browse to \SymantecDLP\Protect\config\Manager.properties (15.0 and below) or to Symantec/DataLossPrevention/Enforce Server/15.1/Protect/config/Manager.properties (15.1 and above).
14. Now search for the line com.vontu.manager.policy.showcustomscriptrule = false

15. Change this value to = True and exit.
16. Restart your DLP Enforce server services.
17. Once your DLP instance is back up and running go into an existing policy or create a new and select 'Add Rule'

As you can now see you have a 'Custom File Type Signature' rule option to select
If you do not have this option please review the above steps for enabling or see https://help.symantec.com/cs/dlp15.0/DLP/v48848719_v120691346/Enabling-the-Custom-File-Type-Signature-condition-in-the-policy-console?locale=EN_US )
18. Insert the relevant information and the script designed earlier:
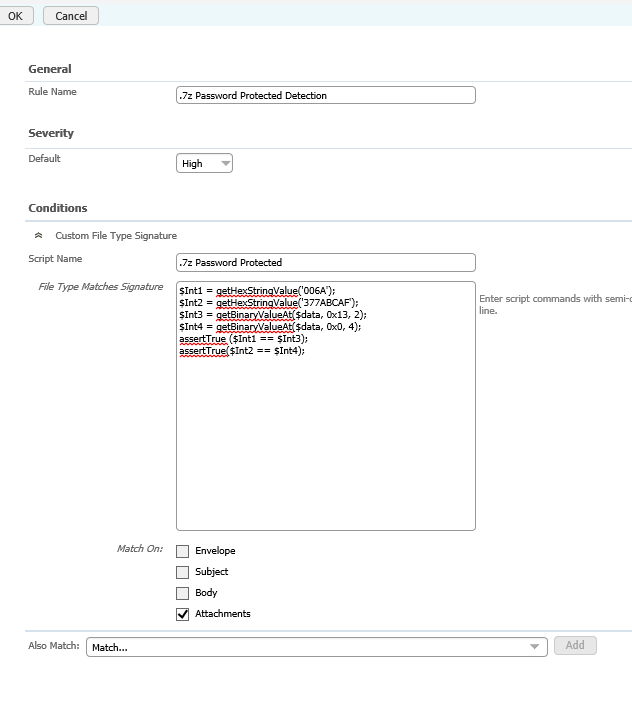
Conclusion: You now have a custom file extension rule operational in DLP, this method can be applied to any file type not just .7z so please use this guide as a reference to what you're trying to achieve.
The process can be a little tedious and frustrating at times but the overall results once you've completed are extremely valuable.
This guide has been previously submitted by my colleague, I've created my own guide on this purely to add my twist on custom file extensions ana a refresher with newer versioning being available.
Previous article:
https://www.symantec.com/connect/articles/data-loss-prevention-dlp-create-custom-file-type-signature
I hope you've found this article helpful and informative.
