Hi Phil,
I followed the official SGOS admin guide. In your article there is one more step - add the proxy as computer into domain.
I did that but no change.
In the pcap on the client I see that the proxy is offering negotiate. As you can see Kerberos is not listed as the health check is down:
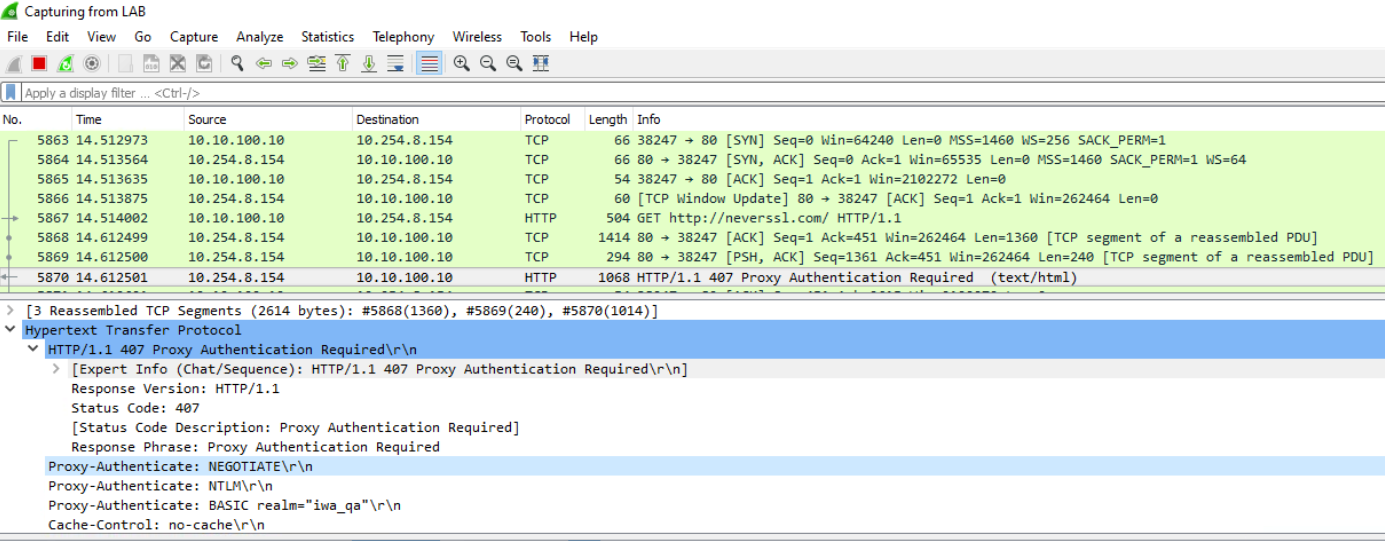
But I think the client is sending the Kerberos ticket anyway:
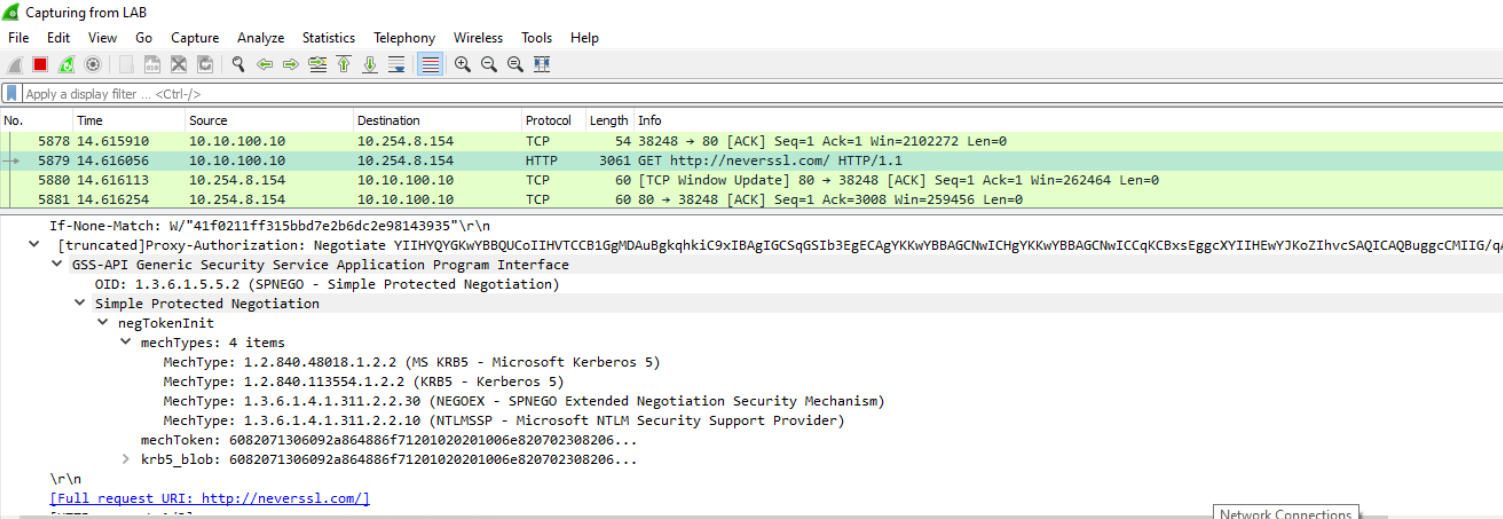
I don't think capturing between proxy and DC will have any benefit as that is proprietary over 16101.
On the DC in the event viewer, I see that the BCAAA user attempted kerberos authentication and requested service ticket.
I'm not sure where else to look.
Thank you.