If you want to use authentication in DMZ with no access to an authentication IDP, it's no possible obviously.
You can do these things though:
- use policy substitution realm and get the information from the LAN using headers, which means it's authorization on the DMZ.
- use the same method but also use LDAP if it's available from the DMZ to fetch information on the user.
It's not documented well enough but if you dig into it, it can work.
Example:
LAN:
Authenticate with AD or something,
;<Proxy>
;client.effective_address.request("$(request.header.X-Forwarded-For)")
define action Auth_Forward
set(request.header.X-Forwarded-For, "$(x-cs-client-effective-ip)" )
;set(request.x_header.BC_Auth_User, "$(cs-username)" )
set(request.x_header.BC_Auth_User, "$(cs-user)" )
set(request.x_header.BC_Auth_Groups, "$(groups)" )
end
define action Auth_Forward_CONNECT
set(forward.http_connect.header.X-Forwarded-For, "$(x-cs-client-effective-ip)" )
;set(forward.http_connect.x_header.BC_Auth_User, "$(cs-username)" )
set(forward.http_connect.x_header.BC_Auth_User, "$(cs-user)" )
set(forward.http_connect.x_header.BC_Auth_Groups, "$(groups)" )
end
<Proxy>
action.Auth_Forward(yes)
<Forward>
action.Auth_Forward_CONNECT(yes) forward("DMZ") forward.fail_open(no)
DMZ
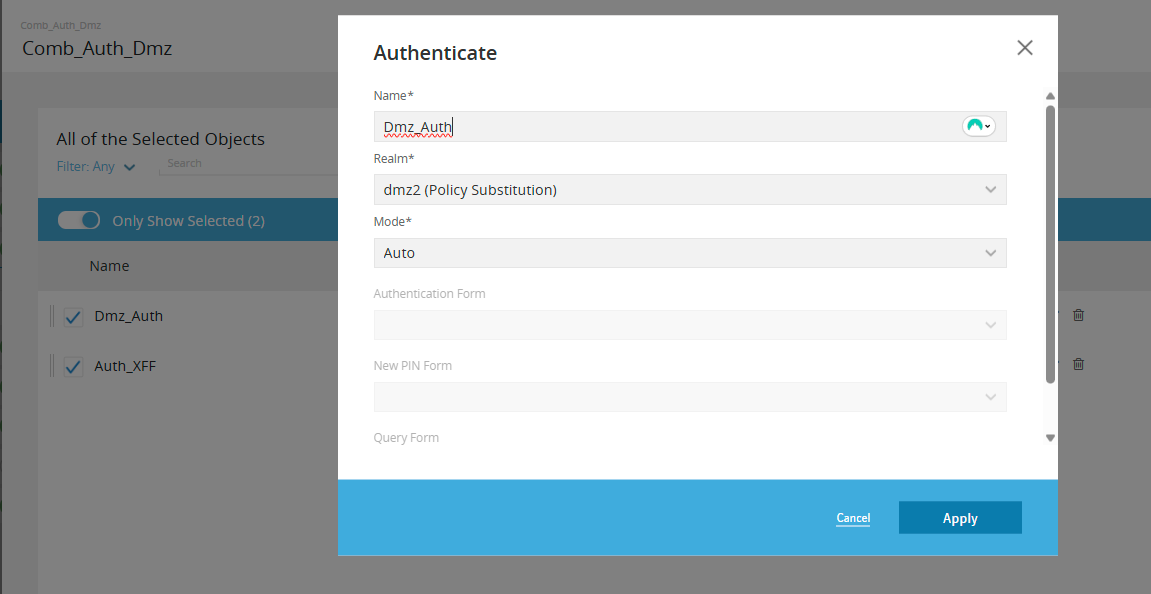
You will also need to use CLI in the DMZ proxy for additional configuration
Policy Substitution Realm
Original Message:
Sent: Jun 03, 2025 06:03 AM
From: Dominique Kanana
Subject: Proxy Chaining
Hi team,
How can I achieve this:
ProxySG version: 7.3.22
Scenario:
workstation > lan > dmz > isolation
During testing, I disabled the authentication CPL policy in the DMZ while retaining traffic forwarding. This allowed successful routing to the isolation service, with both the client source IP and user identity visible in the logs.
However, I am still able to use LAN authentication in the DMZ. The issue occurs when I try to forward to isolation, I receive an error at that point.
Errors:
Authentication Error - Bad Configuration.
Instruction to Administrator: Web Isolation did not receive the authenticated user information for the shared-domain.
Make sure to send the user information for all required Web Isolation domain.
. This webpage is blocked due to missing identity information.
Thank you,
Dominique.