Some of the key takeaways from December’s Latest Intelligence, and the threat landscape in general, include an increase in the number of web attacks blocked by Symantec, the return of a particularly nasty disk-wiping threat, and how Symantec played a vital role in two law enforcement operations.
Web attacks
Last month, the number of web attacks blocked by Symantec per day increased to 388,000, up from 291,000 the previous month.
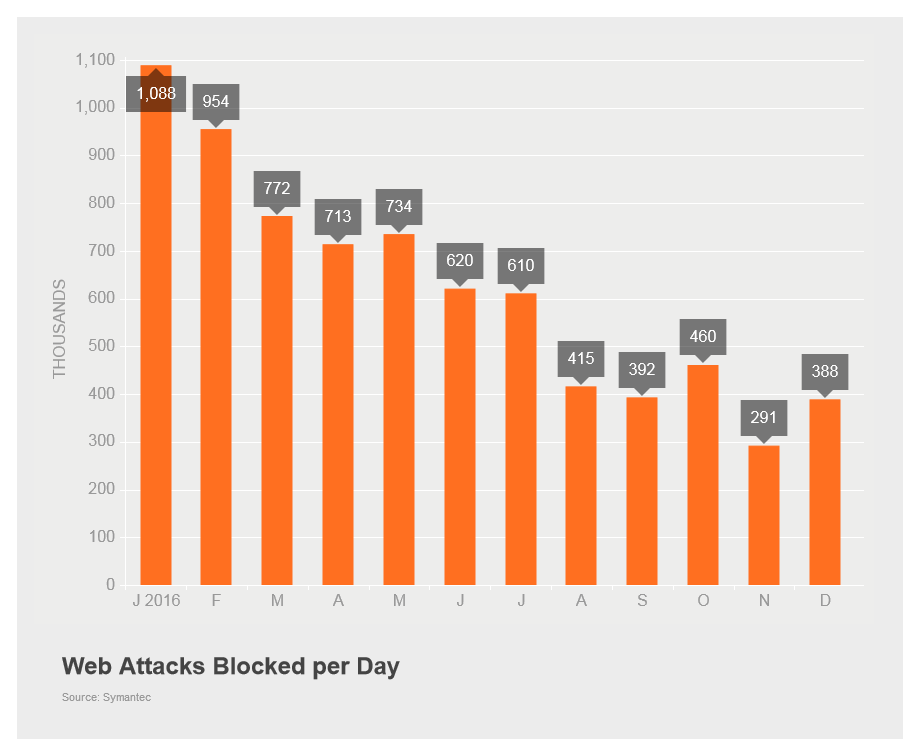
Figure 1. The number of web attacks blocked increased in December to 388,000 per day.
There was no change in the exploit kit top-three rankings for December. RIG retained the number one spot for the fourth month in a row with 34.8 percent of all exploit kit activity. Fiesta’s activity rose slightly to 4.2 percent, holding the kit at its number two spot. And although Magnitude also increased its activity from the previous month (up from 2.6 to 3.2 percent) it still placed third after being knocked from second place by Fiesta in November.
Yet another new exploit kit arrived on the scene in December. Dubbed Stegano after steganography, a method of hiding content within other data, the new exploit kit hides its attack code in individual pixels of malicious advertisements hosted on popular news sites.
Malware
The number of new malware variants seen in December dropped to 19.5 million (down from 71.2 million in November). This is the lowest levels seen since last July. The drop might be the result of a decline in activity surrounding the Kotver (Trojan.Kotver) family of threats, which saw significant activity from August to November last year.
Symantec continued to play an important role in the battle against cybercrime last month, helping to severely impact the operations of the Avalanche malware hosting network, which is responsible for a variety of spam, phishing, and malware operations. The international takedown operation dismantled infrastructure used by at least 17 malware families including the Zeus financial Trojan (Trojan.Zbot), and ransomware families such as Trojan.Ransomlock.P and Trojan.Bebloh.
Last month also saw three Romanian men charged for allegedly operating a longstanding fraud operation known as Bayrob that conned victims out of millions of dollars. Symantec assisted the FBI in the long-running investigation that lead to the arrests. Symantec has tracked the Bayrob gang’s activity since 2007 when it began using malware (Trojan.Bayrob) to infect computers and display fake online auction pages to mislead users into thinking they were conducting legitimate purchases.
The use of malicious PowerShell scripts is on the rise, according to research conducted by Symantec in December. Over the course of six months, our research found that 95.4 percent of PowerShell scripts submitted to Symantec were malicious. Attackers are using the framework’s flexibility to download their payloads, traverse through a compromised network, and carry out reconnaissance. Prevalent threats that use this technique include W97M.Downloader, Trojan.Kotver, and JS.Downloader.
We also saw the return of the infamous disk-wiping malware known as Shamoon (W32.Disttrack) in December. The malware made headlines back in 2012 when it was used in attacks against Saudi energy companies. Last month, Shamoon re-emerged in a fresh wave of attacks against new targets in Saudi Arabia.
Spam
The global spam rate declined slightly in December to 54.2 percent, down 0.1 percentage points from November. Organizations with 1,001-1,500 employees had the highest spam rate in December and the Construction sector was the industry with the highest spam rate, increasing 2.1 percentage points to 63.3 percent.
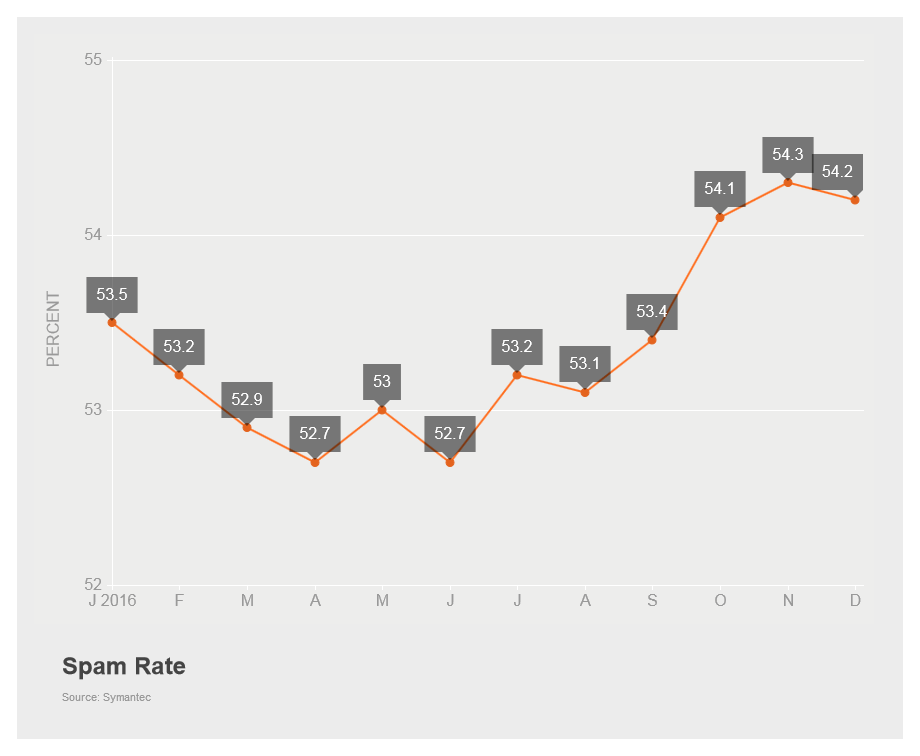
Figure 2. The global spam rate declined slightly in December, to 54.2 percent
Reports emerged in December of an improved version of the old hailstorm spam technique being used to spread Dridex (Trojan.Cridex) and Locky (Ransom.Locky). This proves that the email spam problem shows no signs of disappearing. The technique uses multiple IP addresses to send out high volumes of spam over a short time period and is derived from snowshoe spamming.
Phishing
Phishing continues to be a major threat to organizations, as highlighted last month when the LA County Chief Executive Office issued a public notice revealing that 756,000 Californians would be receiving breach notification letters because 108 LA County employees fell for a phishing email scam earlier in the year.
The phishing rate decreased last month, down to one in 3,357 emails. In particular, the Mining sector saw a significant drop in phishing activity during December, down from one in 972 emails in November to one in 5,423. Businesses with 1-250 employees had the highest phishing rate for December with one email in 3,575 being a phishing attack.
Mobile
The month also saw researchers discover at least 28 low-cost Android phone models that included built-in software that downloads adware and potentially unwanted apps. The downloader software (Android.Malapp) was found in the firmware of phone models manufactured by several brands. In some instances the software could also make phone calls, display advertisements, and opens links in the phone’s browser.
December became the sixth month in a row in which no new Android malware families were discovered. However, the number of Android variants per family increased yet again to 59.
This is just a snapshot of the news for the month. Check out the Latest Intelligence for the big picture of the threat landscape with more charts, tables, and analysis.