Introduction
This is the twenty-third in my Security Series of Connect articles. For more information on how to keep your enterprise environment secure using often-overlooked capabilities of Symantec Endpoint Protection (and the OS upon which it functions), see Mick's Greatest Hits: Index of Helpful Connect Security Articles. This article was last updated in May 2019.
This article hopes to give admins the techniques they need to eliminate one of their network's most persistent ransomware pests: Ransom.Wannacry, also known as WCry and WannaCrypt.
What is Wanncry, and Why Won't it Go Away?
Since its appearance in May 2017, Symantec has released a great deal of information about Wannacry and how to combat it. Full details on its history and how it functions can be found in:
Webinar: Don't Cry Over WannaCry Ransomware
The good news: this existing information about how the Wannacry threat operates remains accurate. Though slightly different samples appear from time to time, no one today is facing a new strain of this threat- just the same code that others have successfully defeated.
With the proper care and action, administrators can eliminate Wannacry for good. Administrator involvement is the key. Wannacry will remain in a network until steps are taken to remove it. It will not go away by itself.
Are You Ready to Fight WannaCry?
Symantec released protection against Wannacry on May 12, 2017. Scanning for the threat with definitions older than that won't do much good. From the Symantec Endpoint Protection Manager (SEPM), export a Computer Status log and confirm if there are Symantec Endpoint Protection (SEP) clients which have failed to update their definitions.

You may be surprised to discover clients which are malfunctioning and unable to update their signatures, or even clients with releases of SEP that have gone past their End Of Life years ago. These clients are incapable of mounting an effective defense against Wannacry. (Some columns hidden for clarity...)
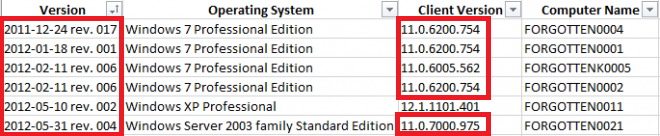
If the SEPM shows no Wannacry detections but corporate firewalls or DNS servers are seeing traffic to the distinctive Wannacry domains iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com and ifferfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com, there is an infected computer in the network without SEP installed. Find it and fix it because it is trying to spread that infection to others! In large organizations it is common for a few forgotten boxes, locked in closets or remote offices, to continue computing away. Just because these machines do not appear in a management console, it doesn't mean that they don't exist.
Configuring a client to detect unmanaged devices
https://www.symantec.com/docs/HOWTO80763
Remember: a working, supported SEP client on every computer is the starting point. Get one installed!
Help! Hundreds of Computers are Infected!!
First off: are computers actually being encrypted? If so, they may look like this:

Wannacry has a worm component to spread and a payload that encrypts. It's been rare to see ransom-demanding damage done since the early days of this threat. Mostly, today, it's just the constant annoyance of the worm component causing alarm.
| Do invest the effort necessary to wipe out Wannacry even if no encryption is happening. Other destructive threats function by abusing the same EternalBlue SMB vulnerability that WannaCry uses. Patching and hardening defenses against Wannacry will provide protection from them as well. |
Each infected machine will attempt to spread Ransom.Wannacry to other computers that it can reach. If SEP is installed on those computers and is running with signatures newer than 2017, SEP's Auto-Protect capabilities should be able to stop it from falling victim. However, it will log a successful detection of Ransom.Wannacry. That detection will be forwarded to the SEPM to be displayed there. New admins running a Risk Report can give themselves a heart attack by seeing hundreds of Wannacry events from all across their company.
Examining the action taken for all those events will show the great majority of Actual Actions are successful protections against attempted infection.
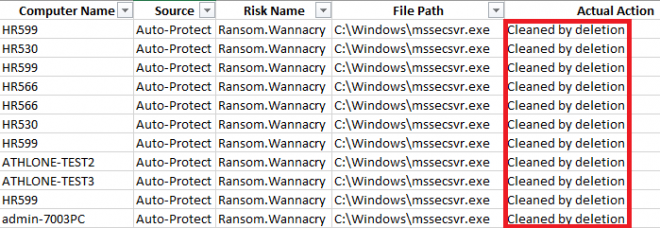
The solution to a persistent Ransom.Wannacry outbreak is to identify and clean the handful of computers in the network that are actually infected.
This will require action by the network admins. Having SEP installed on the computers in the network will not be enough to automatically safeguard the security of the organization. SEP is a good tool, but it is only one tool- it is up to the network admins to use it. SEP is also not a replacement for following best practices and proven computer security techniques.
The following article is full of good advice- completely invaluable for fighting Ransom.Wannacry and other outbreaks. The steps within may not be convenient, but they are necessary. Following these procedures will work.
Best Practices for Troubleshooting Viruses on a Network
http://www.symantec.com/docs/TECH122466
Tracking Down the Infected Computers, Part 1: Risk Tracer
The SEPM's Risk Reports can also tell admins which computers are highly likely to have attempted to infect their peers. All details can be found in the following article:
What is Risk Tracer?
Article URL http://www.symantec.com/docs/TECH102539
Enable and use Risk Tracer to locate those computers in the organization that are infected with Ransom.Wannacry- then isolate them! Only let them back onto the network when they are completely clean and secure.
Tracking Down the Infected Computers, Part 2: IPS
IPS is a very strong defense against this threat: three signatures in particular...
21331 Attack: SMB Double Pulsar Ping
23875 OS Attack: Microsoft SMB MS17-010 Disclosure Attempt
30239 Audit: Unimplemented Trans2 Subcommand
Those not only block suspicious EternalBlue-related traffic, but provide the IP Address of the remote computer which attempted to spread the infection. Export the IPS events (Network Threat Protection, Attacks) as csv, then open with your favorite spreadsheet program to see which Remote Host IPs are sending the malicious traffic. (Some columns hidden for clarity...)
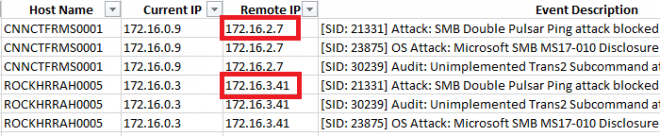
Isolate those remote machines and only let them back onto the network when they are completely clean and secure!
What if the IP Address is from Outside the Organization?
If the network is configured to allow SMB connections from anywhere, IPS logs can display the Remote Host IP as an address from the public Internet. Follow the advice from US-CERT, Microsoft and other experts: disable ancient versions of SMB, and configure perimeter firewalls to keep SMB traffic within your own network only!
Kill it with fire: US-CERT urges admins to firewall off Windows SMB
https://www.theregister.co.uk/2017/01/18/uscert_warns_admins_to_kill_smb_after_shadow_brokers_dump/
SMB Security Best Practices
https://www.us-cert.gov/ncas/current-activity/2017/01/16/SMB-Security-Best-Practices
Guidelines for blocking specific firewall ports to prevent SMB traffic from leaving the corporate environment
https://support.microsoft.com/en-ie/help/3185535/guidelines-for-blocking-specific-firewall-ports-to-prevent-smb-traffic
Tracking Down the Infected Computers, Part 3: NMap
NMap is a great tool for spotting which computers are open to infection via the EternalBlue vulnerability. Scan your network and patch any machines missing security update MS17-010 to keep them safe!
As it is not a Symantec tool, NMap will get a nod here but not an elaborate set of instructions on how to use it. I'll leave that to the experts at SANS.
Using nmap to scan for MS17-010 (CVE-2017-0143 EternalBlue)
https://isc.sans.edu/forums/diary/Using+nmap+to+scan+for+MS17010+CVE20170143+EternalBlue/22574/
Microsoft released patches for Windows XP and Windows Server 2003 even though they are past their End Of Life, so there really is no excuse!
| Vulnerability scans of your network are highly recommended best practice. Whatever your favorite tool to identify unpatched, vulnerable computers is, be sure to use it regularly! |
Effectively Cleaning Machines
Once those infected computers have been identified:
- Isolate the computer from the network (pull out the network cable), then reboot
- Perform a full system scan and then reboot again
- Check the logs to confirm the complete removal of Ransom.Wannacry (and any other threats!)
- Apply all missing Microsoft patches and ensure that autorun is disabled on the computer
As a best practice, provide the user who will be logging in to that machine with a new, strong password.
Conclusion
Many thanks for reading! Following the actions above should leave you with a safer, better-secured Wannacry-free network.
Please leave comments and feedback below.