How to block applications in SEP using MD5
1. Firstly we need to obtain the file Checksum.exe .
The file is located on the root folder of the SEP client (%programfiles%\Symantec\Symantec Endpoint Protection\Checksum.exe)
2. After we obtained the file and we need to have the program that we want to block installed (or if the program doesn't need installation then we need the executable file).
3. I would suggest copying the Checksum.exe program to c:\ to make the procedure easier.
4. Assuming that the file is in C:\ then what we do is:
· click Start-->Run-->CMD.EXE
· A command line will appear.
· Navigate to the folder where the Checksum file is located.
· Run the following command:
Checksum.exe **result file location** **application location**
**Result file location** = the location and name of the result file
**application location** = the location of the application we want to extract its fingerprint.
For example: Checksum.exe c:\result.txt c:\programfiles\ Symantec\Symantec Endpoint Protection\smcgui.exe
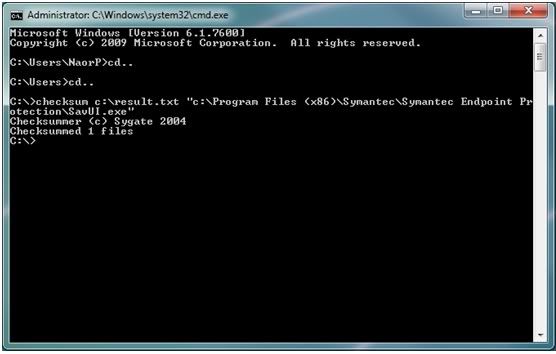
· As you can see I wanted to find out what is the checksum of savui.exe and exported the result file to result.txt
· The procedure should take only a couple of seconds and you should see "Checksummed 1 file".
· When we open the output file this is the answer we will get:
9213d1c5f877272231f6763f143d554c c:\Program Files (x86)\Symantec\Symantec Endpoint Protection\SavUI.exe
· The part with the unique ID is the Fingerprint of the file and we also have the path of the file.
5. Using the Fingerprint extracted with SEP:
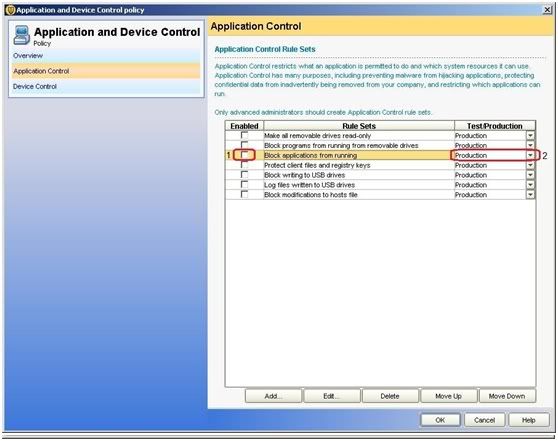
· Open the SEPM
· Go to Policies and click on Application and Device control policies
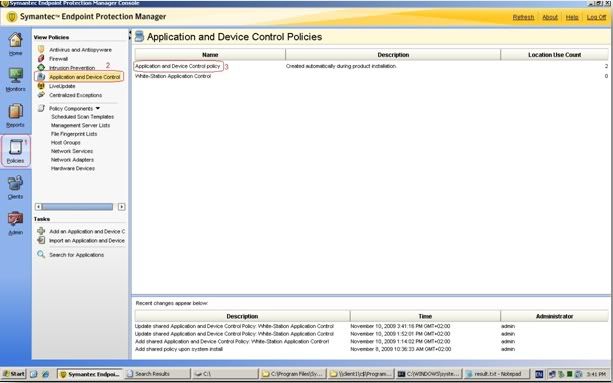
· Right click on the Policy and click edit (I decided to use the default application control policy but you could create your own if you'd like).
· Click on Application control "Block application from running" and "edit"
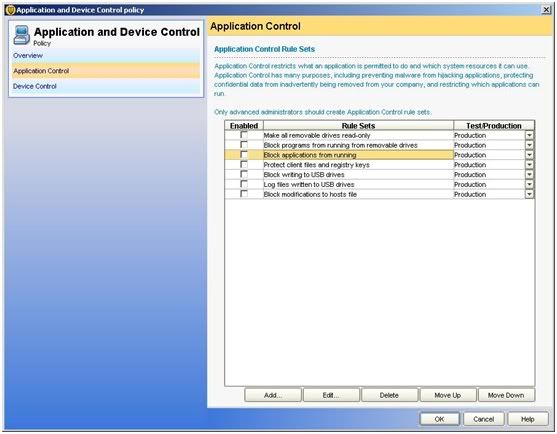
· Go to "apply this rule to the following processes" and click on "Add"
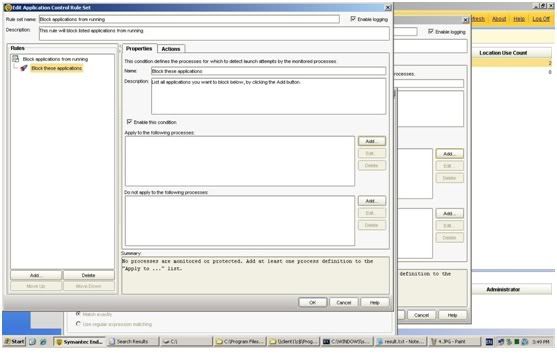
· click on "Options" and then 2 new fields will come out.
· click on Match the fingerprint and there paste the Unique ID we have foung earlier: 9213d1c5f877272231f6763f143d554c
· Click on OK and that is it. SEP will block the program that you want.
· One Reminder: you need to apply the policy on clients and make sure that the Application policy is on production so that it would block the software.
I have also uploaded the file here.
Enjoy,
Naor Penso
Security Engineer
Netcom Malam-Team