
For folks in the internet security world, this past summer has been filled with accounts of malvertising affecting almost every segment of the ad-supported internet. Malvertising occurs when a malicious actor places an ad on a popular website and uses that ad (which may include code such as JavaScript or Flash) to deliver malware to an end user’s computer. For example, a user visits a favorite news site which is unknowingly hosting a malicious ad. When that ad is displayed in the user’s browser, it infects the computer by exploiting a vulnerability, triggering a drive-by-download, or fraudulently prompting the user to install malicious code. Once the bad actor has a foothold, the computer can be used for other nefarious acts, such as stealing credentials and contacts, or turning the computer into a bot controlled by the attacker. Malvertising is not an end in itself, but has become increasingly popular.
Brazil targeted
In April 2015, Symantec began detecting a malvertising campaign targeting Portuguese speakers, particularly those located in Brazil. Portuguese speakers accounted for as much as 75 percent of all victims in this campaign, with more network detections affecting Portuguese speakers than any other during this time. Most of the affected IP addresses in the campaign can be traced to Brazil. Portuguese-speaking victims are attacked when visiting any of several thousand ad-supported websites, including the popular MSN, Universo Online, and Globo Portuguese-speaking websites. Code, contained in malicious ads, loads on the visited websites and attempts to re-direct users to malicious sites.
Over the course of the summer, we recorded nearly 150,000 attacks per day from the same attacker who delivered their payload through one of two domains. In April 2015, the attacks came from the sepabi.com domain. When that domain began to attract suspicion, the attacker registered a new abespi.com domain (which happens to be an anagram of sepabi.com). Once the new domain was established, attacks triggered from the older domain dropped off, further suggesting that the two domains were related. It’s interesting to note the abespi.com domain was registered to Jake Muller (most likely a reference to a character in the popular video game Resident Evil) and includes a Californian post office box mailing address. The other domain, used earlier in the year, was registered in Cyprus but did not have any zombie-fighting video game references.
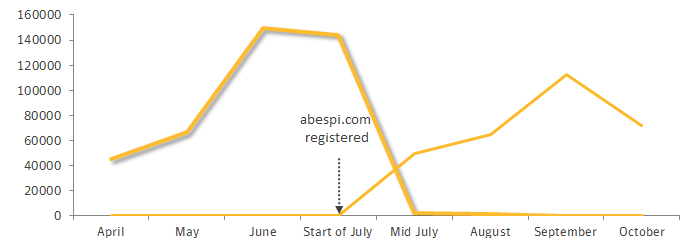
Figure. Attacker moved to different domain to avoid attracting attention
The appeal of malvertising
One reason malvertising is particularly attractive to the bad guys is that it allows attackers to target the users they are most interested in. Just as valid advertisers can target a user for a specific ad (“I only want to pay to advertise my snowshoes to people who live where it snows”) malicious actors can target their malware to a specific set of people (“I only want to trigger my malware on computers where the user is likely to use online banking”). Malware authors can tailor their malicious code to target almost any subset of users, by geography, time of day, company, interests, or recent internet activity. Attackers using malvertising can also leverage the reputation of the legitimate sites the malicious ads are placed on. People visiting a well-known trusted website generally don’t expect to be targeted with malicious code. By placing malicious ads on popular websites attackers can also maximize the amount of people targeted.
Protection
Norton Security, Symantec Endpoint Protection, and other Symantec security products detect the attacks discussed in this blog with the following IPS detections:
Mitigation and work for publishers
The best way to protect yourself against such attacks is to keep your browser and Flash versions up to date and use a solid malware protection solution such as Norton Security. In addition to this, security providers, online publishers, and other participants in the ad tech industry will need to work more closely together to share information about such attacks when they occur.;
Symantec has begun to reach out to publishers affected by this attack but, due to the sheer number of affected publishers, we recommend that ad-supported Brazilian sites take steps to eradicate these malicious actors from their ad supply chain by working with their ad partner to blacklist these malicious sites. And as always, we recommend everyone to keep their operating system and anti-malware protection up to date.