The more and more SiteMinder customers want to integrate the application in cloud environment. This document will show how to integrate SiteMinder and AWS Cognito with SAML. With SAML integration, Users can access AWS Cognito integrated application without reauthentication.
This step-by-step guide helps how to configure Single Sign on between SiteMinder and Amazon Cognito service via SAML.
Perquisite
- SiteMinder 12.8 SP4 above
- SiteMinder Access Gateway 12.8 SP4 above and enable Federation Service
- AWS Sample Application to integrate with AWS Cognito service.
Quick introduction about Amazon Cognito
Amazon Cognito provides authentication, authorization, and user management for your web and mobile apps. Your users can sign in directly with a username and password, or through a third party such as Facebook, Amazon, Google or Apple.
https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-scenarios.html

There is AWS Cognito user pools and Identity pools. User pools are for authentication (identity verification). With a user pool, your app users can sign in through the user pool or federate through a third-party identity provider (IdP).
Identity pools are for authorization (access control). You can use identity pools to create unique identities for users and give them access to other AWS services.
AWS Cognito supports SAML and OIDC integration. In this tech note, it will show how to integrate SiteMinder and AWS Cognito User pools using SAML. Here is authentication flow for AWS Cognito integration by SAML IDP. https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-user-pools-saml-idp.html
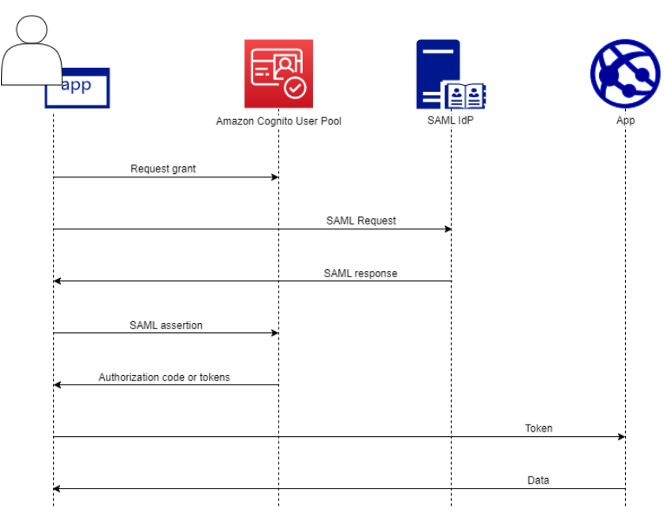
Step. A. Please prepare a sample application in AWS to integrate with AWS Cognito.
If you do not have it, you can create a server-less simple application with S3 bucket https://aws.amazon.com/getting-started/projects/build-serverless-web-app-lambda-apigateway-s3-dynamodb-cognito/module-1/
Once you setup a sample application, please verify the access.

Step. B Prepare SiteMinder SAML IDP environment.
Step. B1 Create Trusted Certificate and Private Keys
Login SiteMinder Admin UI -> Infrastructure-> X509 Certificate Management -> Trusted Certificate and Private Keys.
Click "Request Certificate" and input the value as required.

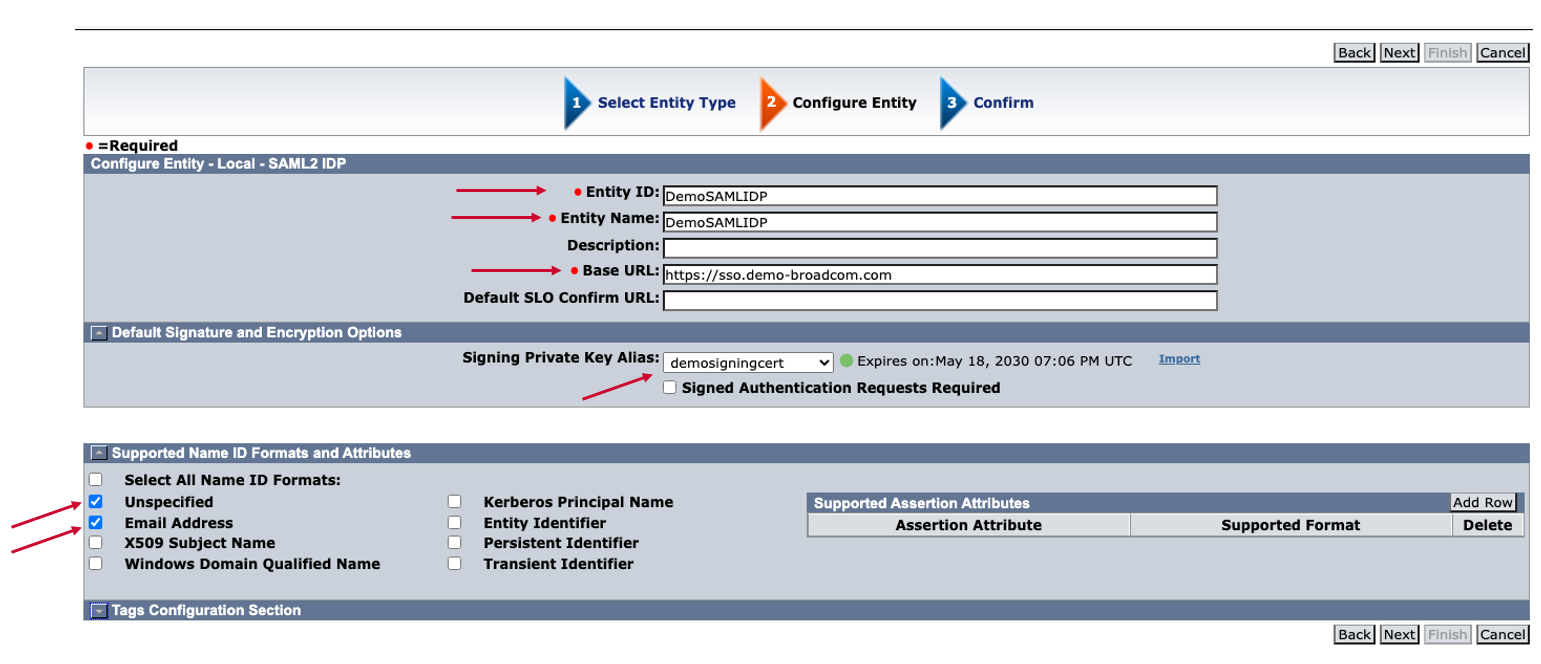
Step. B2 Create SAML Identity Provider
Login SiteMinder Admin UI -> Federation-> Partnership Federation-> Entities
Click "Create Entity" and select "Local" and "SAML2 IDP" in New Entry Type. Then, click next button.

Input the information based on your SiteMinder IDP.
Entity ID: Any Name (ex: DemoSAMLIDP)
Entity Name: Any Name (ex: DemoSAMLIDP)
Base URL: SiteMinder Access Gateway FQDN (ex: https://sso.demo-broadcom.com)
Signing Private Key Alias: Certificate Alias name in Step. B1
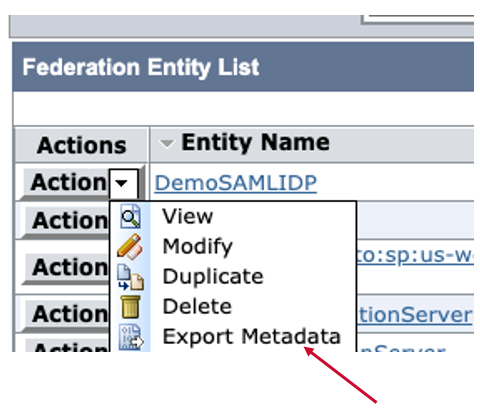
Step. B3 Export SiteMinder SAML Identity Provider
Login SiteMinder Admin UI -> Federation-> Partnership Federation-> Entities
Select Entity name, which is created in Step B2, and click "Action" and select "Export Metadata".
Partnership Name: Any Name
SSO Service URL: Enable HTTP-Redirect, Enable HTTP-POST
Verification and Signing Alias: Certificate alias name in Step. B1
Select Name ID Format: Email Address
Document Signing Alias: Certificate alias name in Step. B1
Document Signature Algorithm: RSAwithSHA256
Valid Day: 1


Step. C Set up AWS Cognito User Pool
Please see AWS Cognito document for the latest information. In this document, it will cover the basic configuration only. https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-user-identity-pools.html
Login AWS Console -> Amazon Cognito-> User pools-> Create user pool

Step. C1. Configure Sign-in experience.
Check "Federated Identity Providers" and select "Use name" and "Email" in Cognito user pool sign-in options.
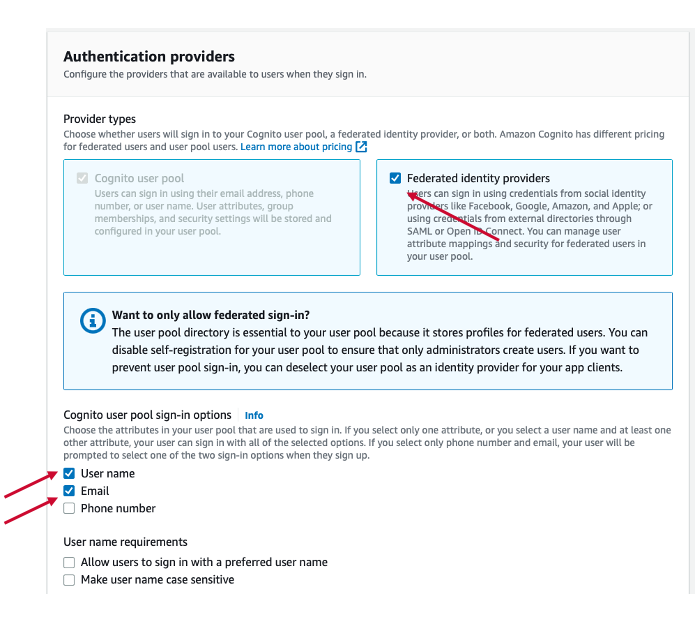
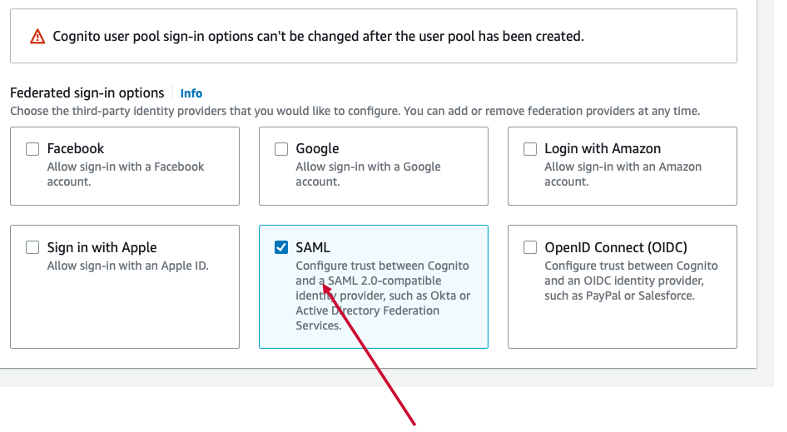
Select "SAML" option in Federated sign-in options and click "Next" button.
Step. C2. Configure security Requirements.
Select "Cognito defaults" options in Password Policy.

Select "No MFA" in Multi-factor authentication and select the setting as default.
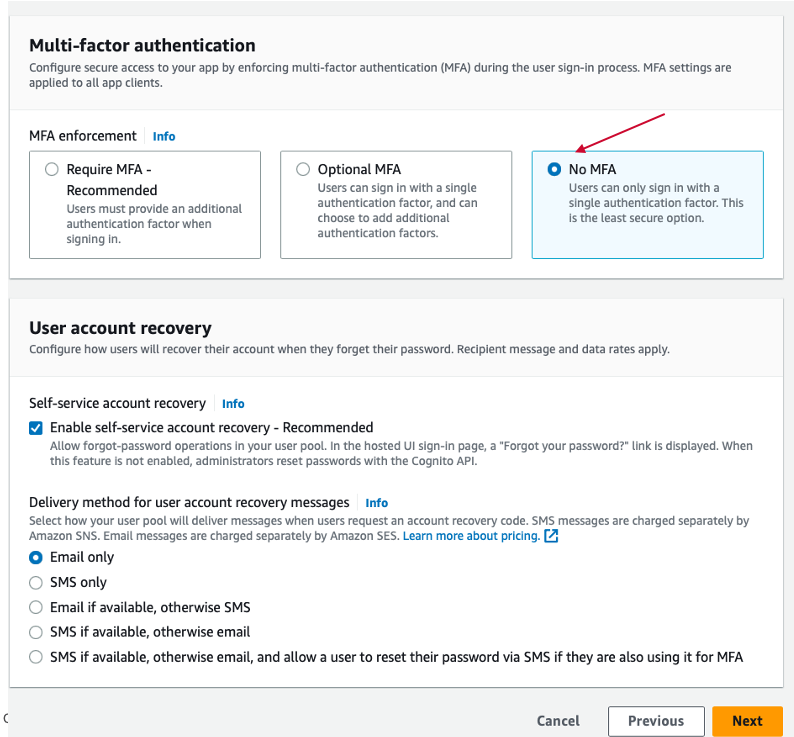
Click "Next" button.
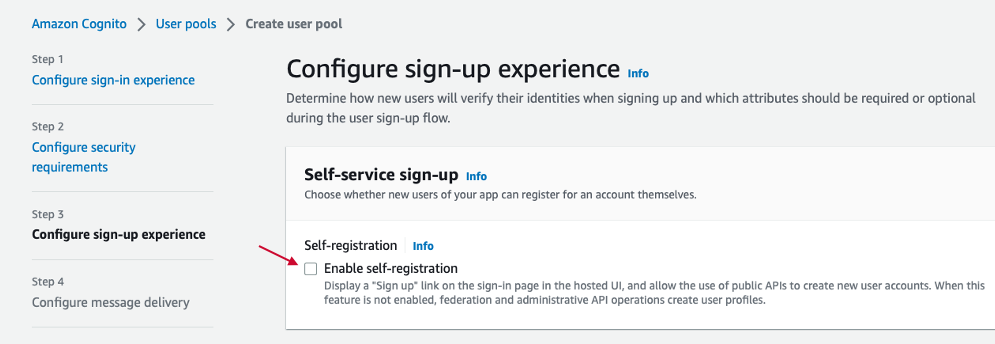
Step. C3. Configure sign-up experience.
Uncheck "Self-registration" option.
In Required attribute, please make sure that there is email.
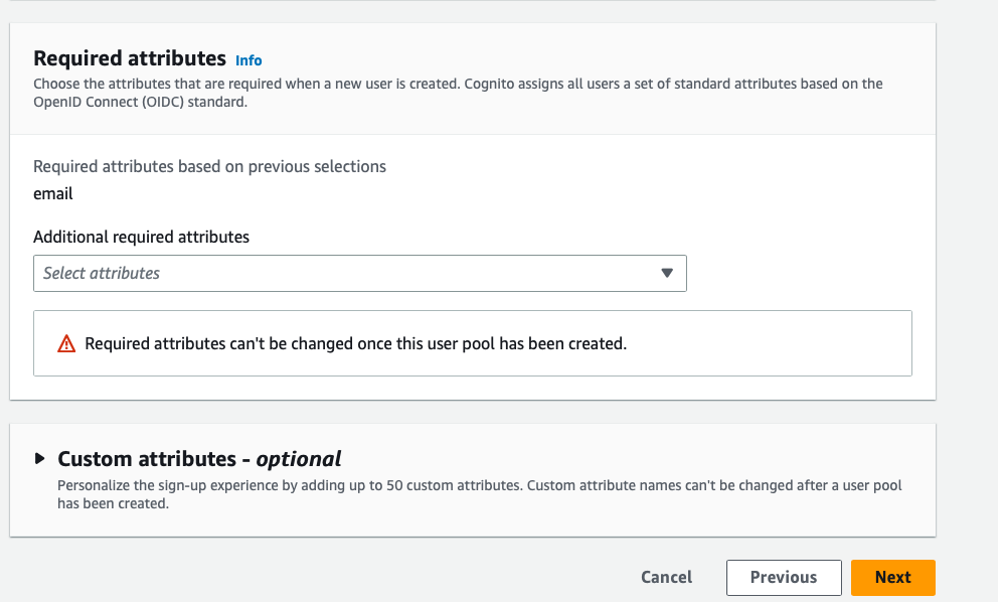
Click "Next" button.
Step.C4. Configure message delivery.
Please select the option, "Send email with Cognito" and leave it as a default for the rest of the configuration.

Step. C5. Connect federated identity providers.
In the Provider name, please input user friendly SAML Provider name. It should not have any space in the name. Do not select "Add sign-out flow"
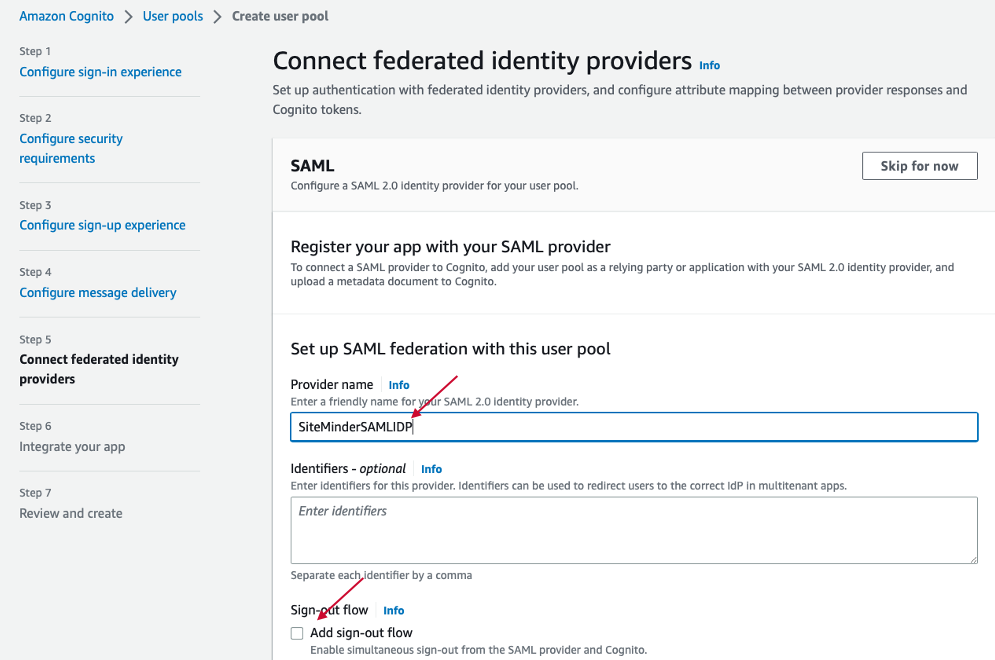
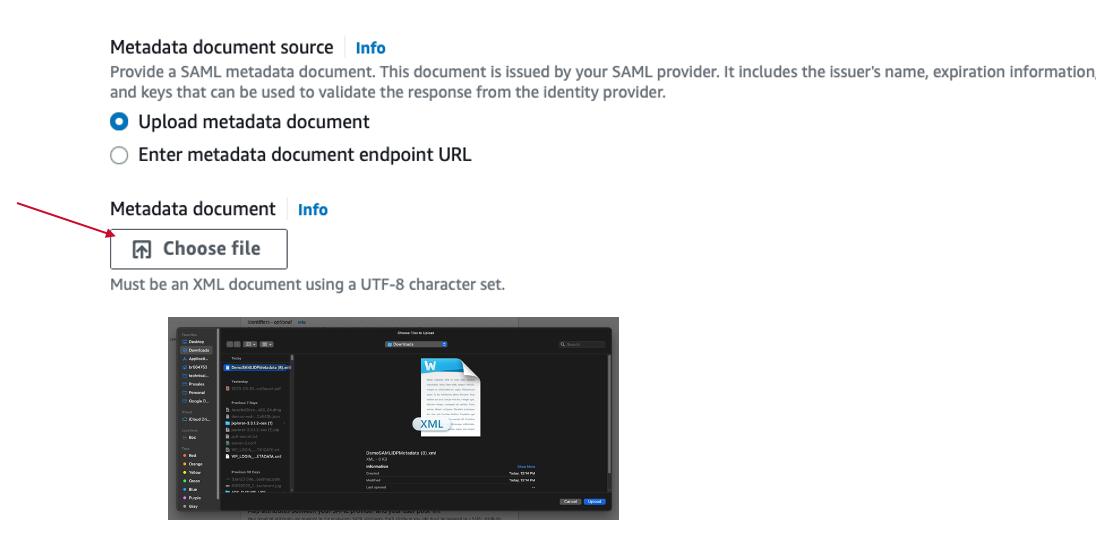
In the Metadata document source, please upload the SiteMinder SAML IDP file from Step2.3.
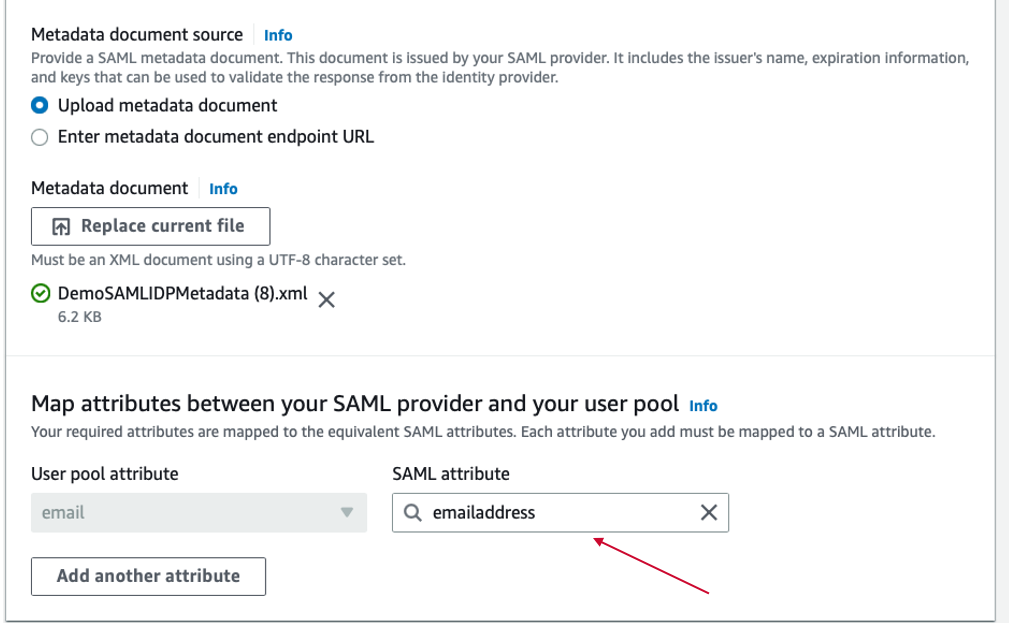
In the "Map attribute between your SAML provider and your user pool", please input "emailaddress". In SiteMinder SAML configuration, "emailaddress" should be included in SAML Assertion.
Click "Next" button.
Step. C6. Integrate your App.
Input "User pool name"
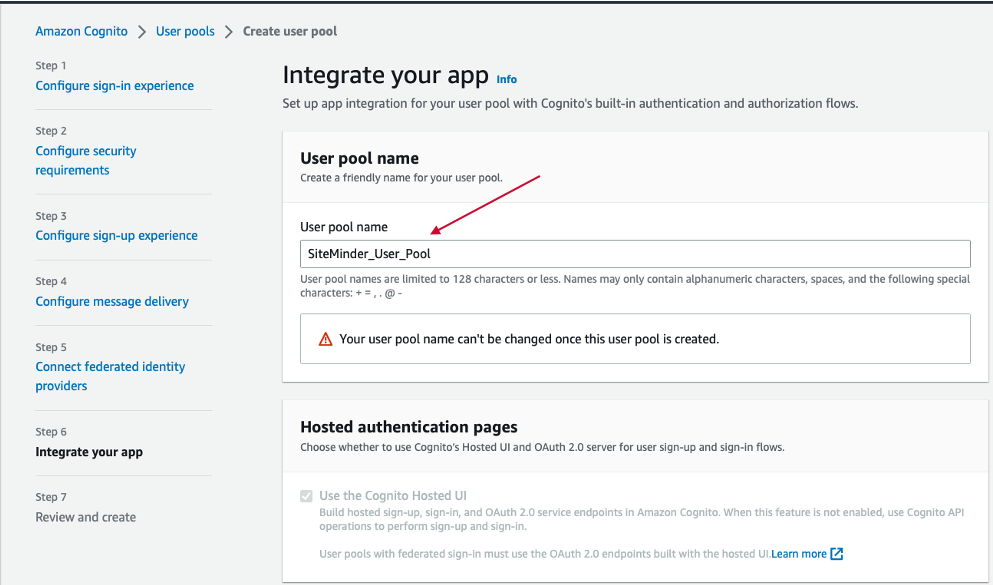
In the Domain section, please select "user a Cognito domain" if you do not have any own domain and enter any unique name in Cognito domain. In this guide, "demo-broadcom" is used and it is available.
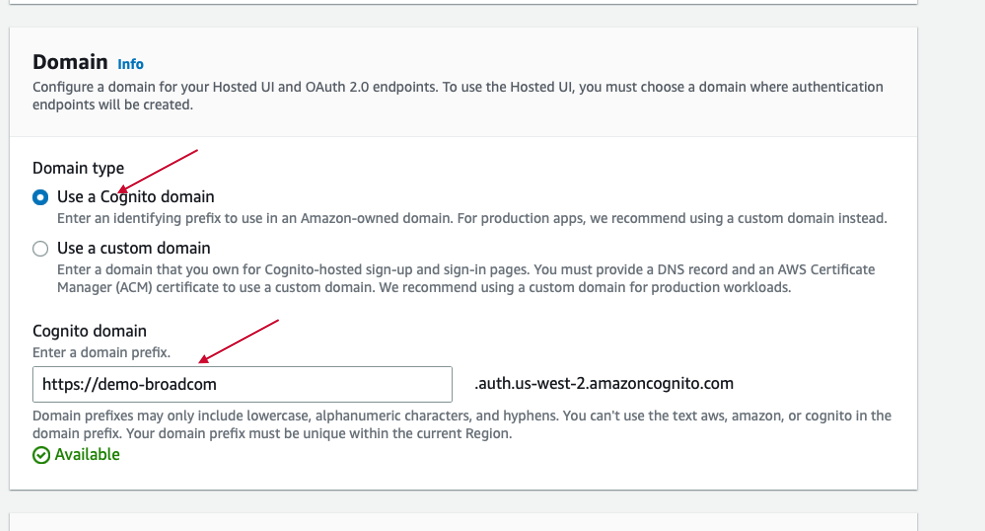
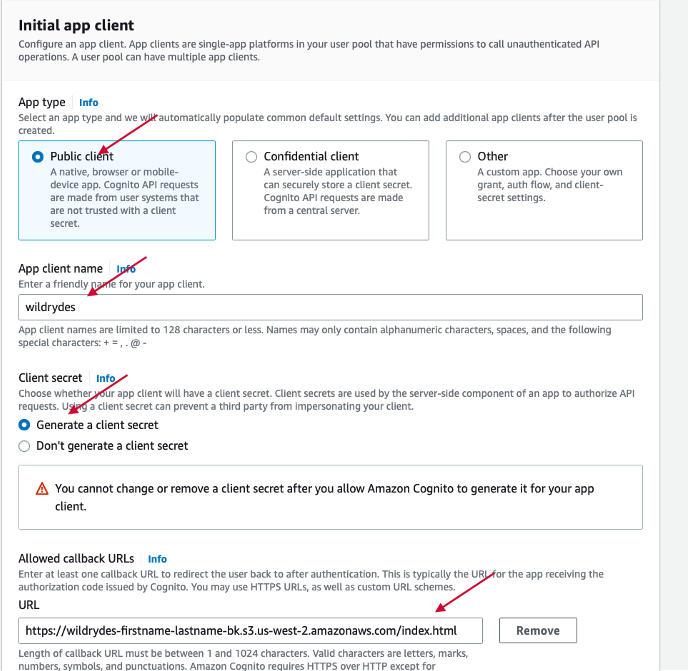
In the "initial app client" section, please select "Public client" and enter App client name and Allowed callback URLs. Allowed callback URL can be a sample application in AWS. In step. A, there is a sample application set up in AWS.
Step. C7. Review and create
If required, please click "Edit" button and change the configuration accordingly.
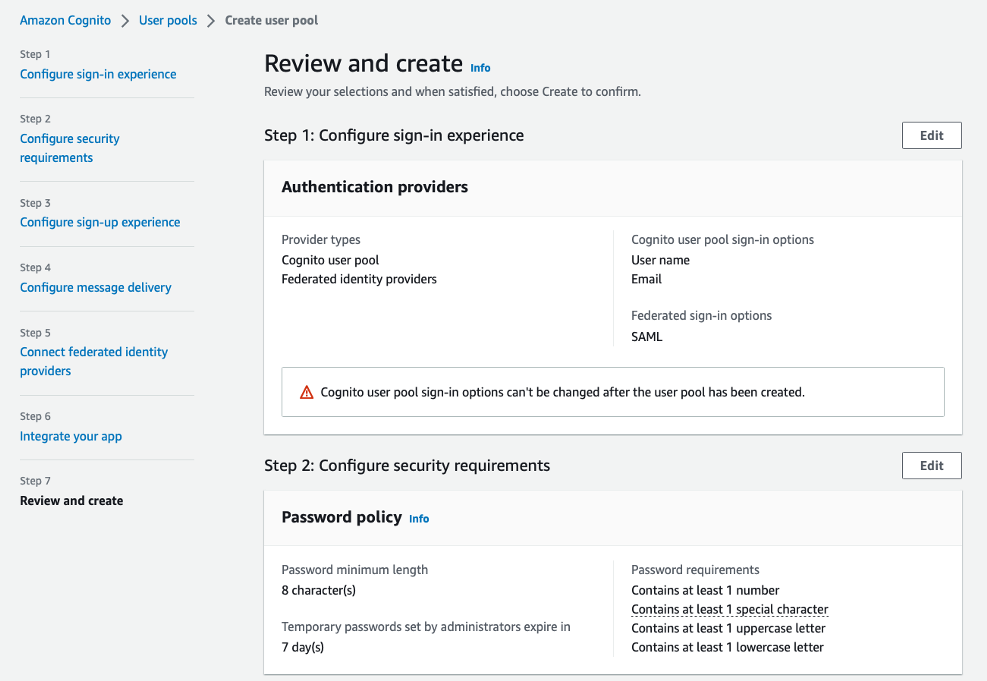
Please change the configuration when you have any error message. You can see the User pool name in the AWS console.
Step. D Config SAML SP in SiteMinder Admin UI
AWS Cognito does not provide SAML meta-data. Hence, it is required to create Service Provider manually.
https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-user-pools-configuring-federation-with-saml-2-0-idp.html
Login into SiteMinder Admin UI
Login SiteMinder Admin UI -> Federation-> Partnership Federation-> Entities
Click "Create Entity". Select "Remote" in Entity Location and "SAML2 SP" in New Entity Type

Click "Next" button.
In Configure Entity Screen, input Entity ID, Entity Name, Remote Assertion Consumer Service URLs, Name ID Format.
Entity ID: "urn:amazon:cognito:sp:<User pool ID>".
Entity ID: Any Name
Remote Assertion Consumer Service URLs: https://<cognito domain>/saml2/idpresponse
Remote SLO Service URL: blank
Name ID Format: Unspecified, Email Address
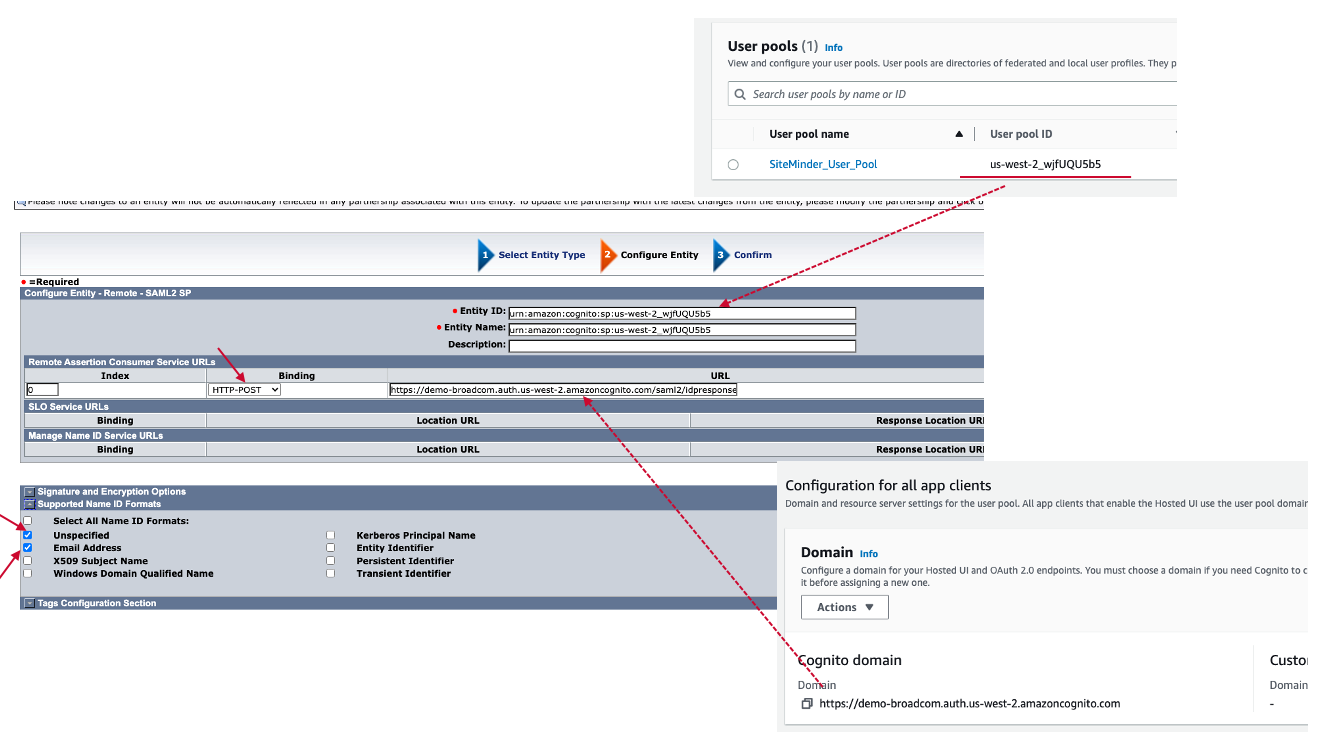
Click "Next" button.
Review the configuration and click "Finish" button.
Step. E Create SAML Partnership in SiteMinder
Login SiteMinder Admin UI -> Federation-> Partnership Federation-> Partnership
Click "Create Partnership" and select "SAML2 IPD -> SP" option.
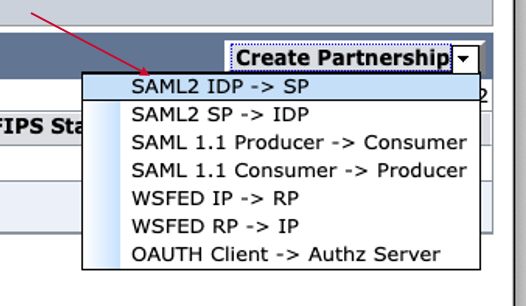
Please delete the uncompleted partnership, which is created during SAML IDP export (Step. B3).
Step. E1. Configure Partnership
Partnership Name: Any friendly Name
Local IDP: SiteMinder SAML IDP (Step. B2)
Remote SP: AWS Cognito SP (Step. D)
Available Directories: Select Any SiteMinder User Directory to access AWS Applications
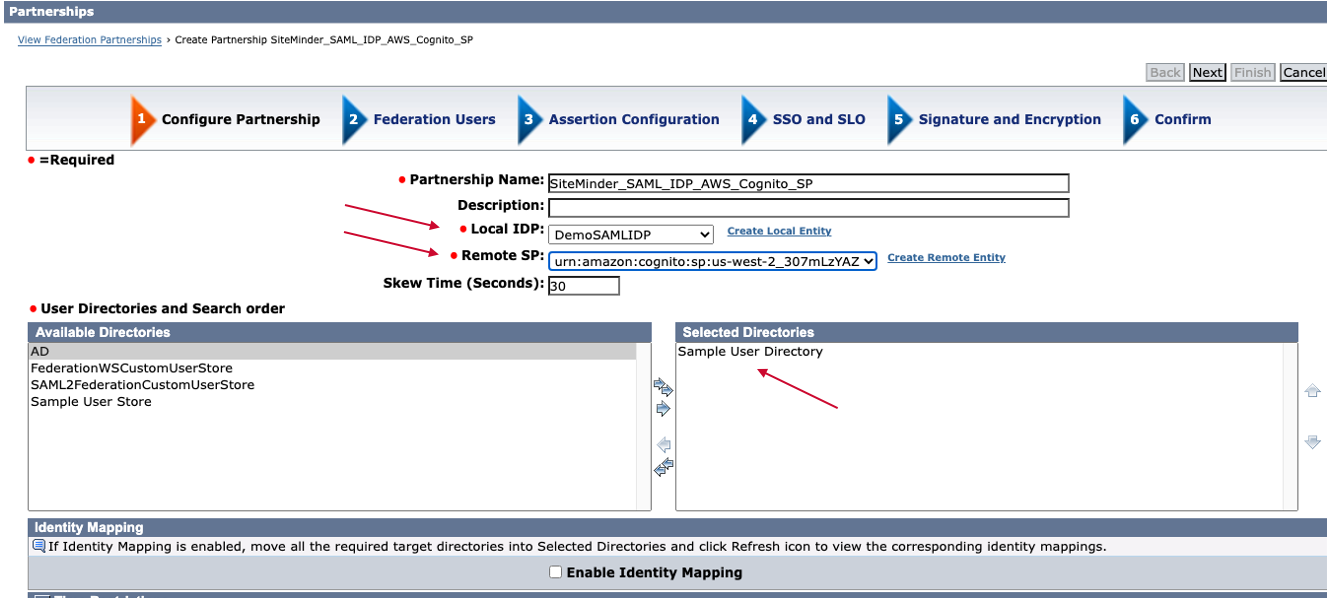
Click "Next" button.
Step. E2. Federation Users
Select All User in Directory
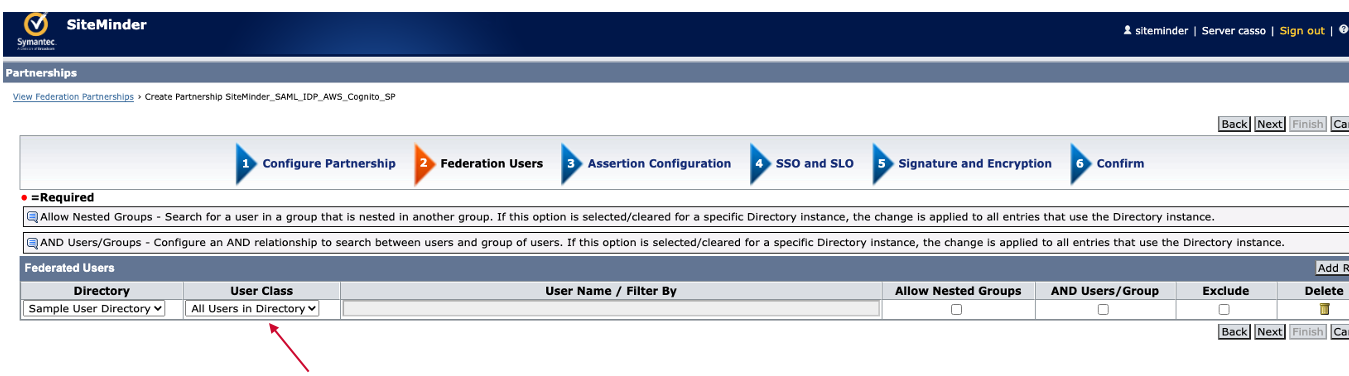
Click "Next" button.
Step. E3. Assertion Configuration
Name ID Format: Email Address
Name ID Type: User Attribute
Value: mail (it is a user directory attribute name that has user's email address)
Assertion Configuration Attribute (SAML Assertion Attribute Name)
Assertion Attribute: emailaddress
Value: mail

Click "Next" button.
Step. E4. SSO and SLO
Authentication Mode: Local
Authentication URL: https://<access gateway fqdn>/affwebservices/redirectjsp/redirect.jsp
Minimum Authentication Level: 5
Authentication Requestion Biding: HTTP-Redirect
SSO Binding: HTTP-Post
Remote Assertion Consumer Service URLs: https://<AWS Congito domain>/saml2/idpresponse
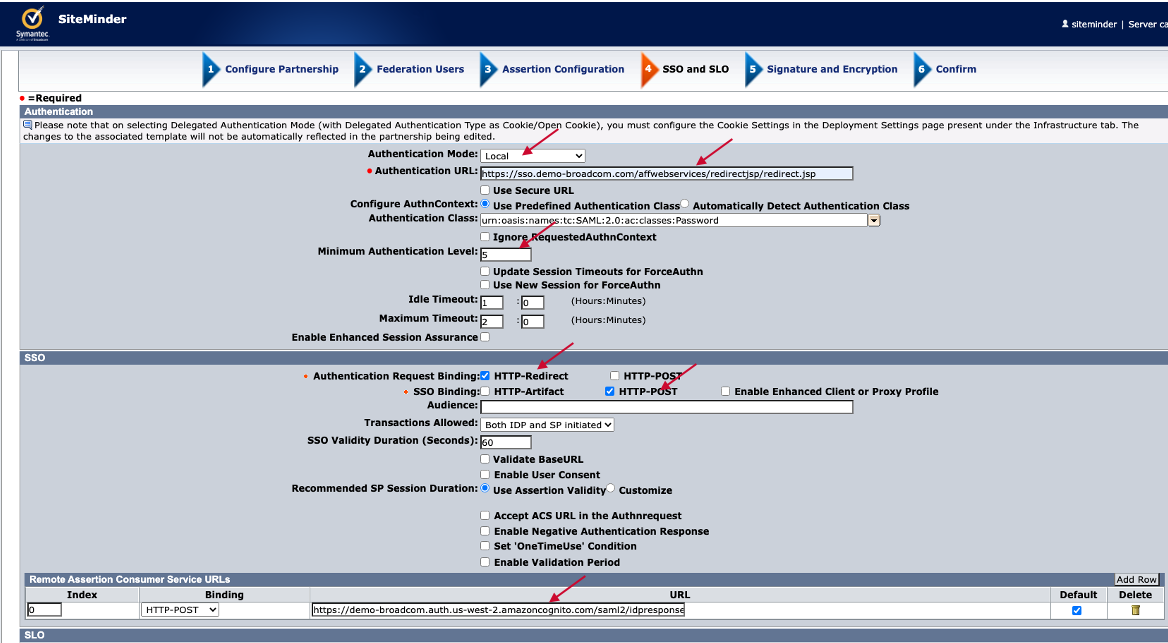
Click "Next" button.
Step. E5. Signature and Encryption
Signing Private Key Alias: Certificate name in Step. B1
Signing Algorithm: RSAwithSHA256

"Next" button.
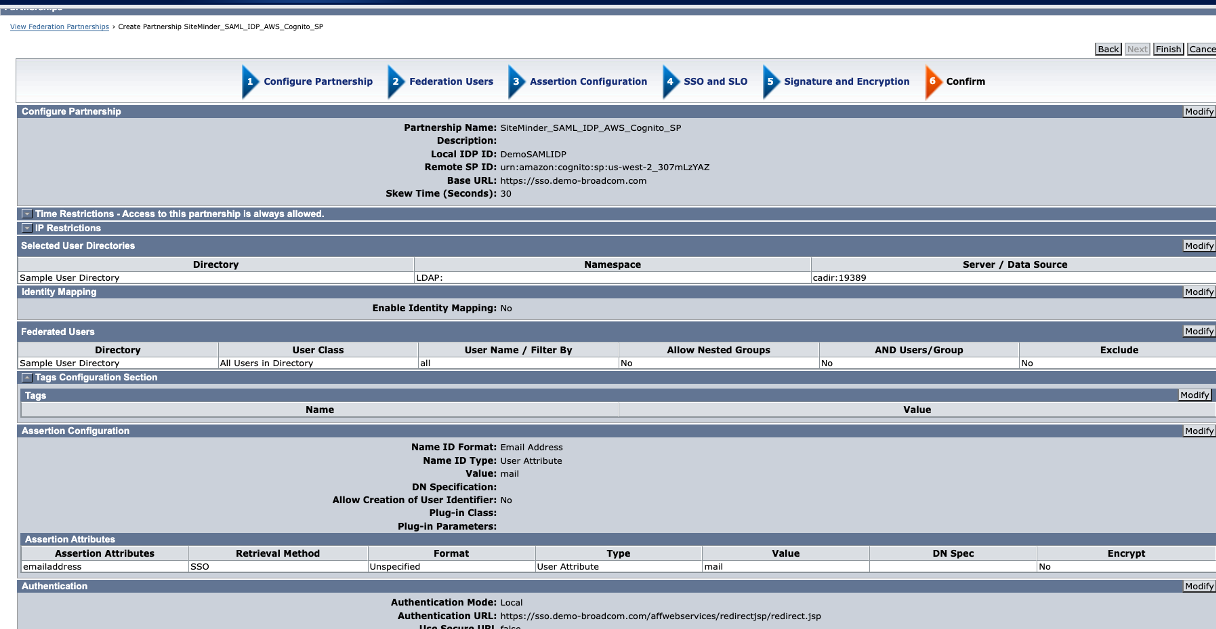
Step. E6. Confirm
Review the configuration and click "Finish" button.
Step. E7. Activate Federation Partnership
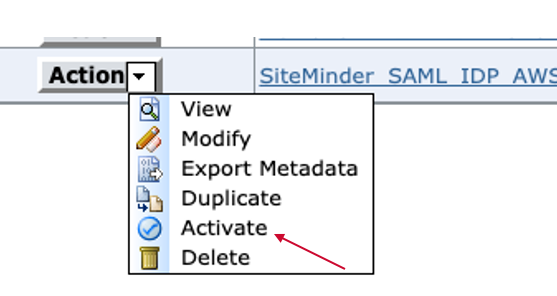
Step. F. Protect Authentication URL
In Step. E4, the authentication URL (https://<access gateway fqdn>/affwebservices/redirectjsp/redirect.jsp) should be protected to redirect to the login page.
Step. F1. Create Domain and Assign the user directory
Create Domain and Assign the user directory in SiteMinder Admin UI. The user directory should be the same in Step. E2.

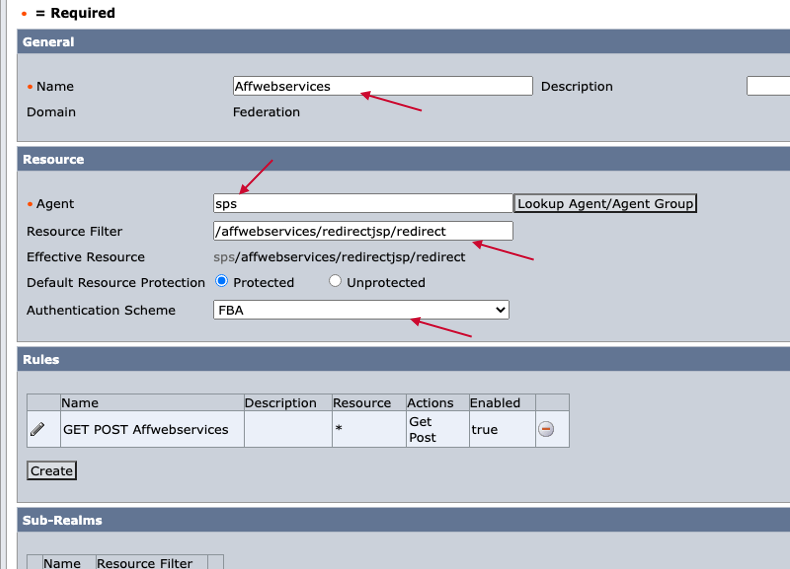
Step. F2. Create Realm under Domain
Name: Any Name
Agent: Access Gateway Agent name
Resource Filter: /affwebservices/redirectjsp/redirect
Authentication Scheme: Any Available Authentication scheme (protection level should be above 5)

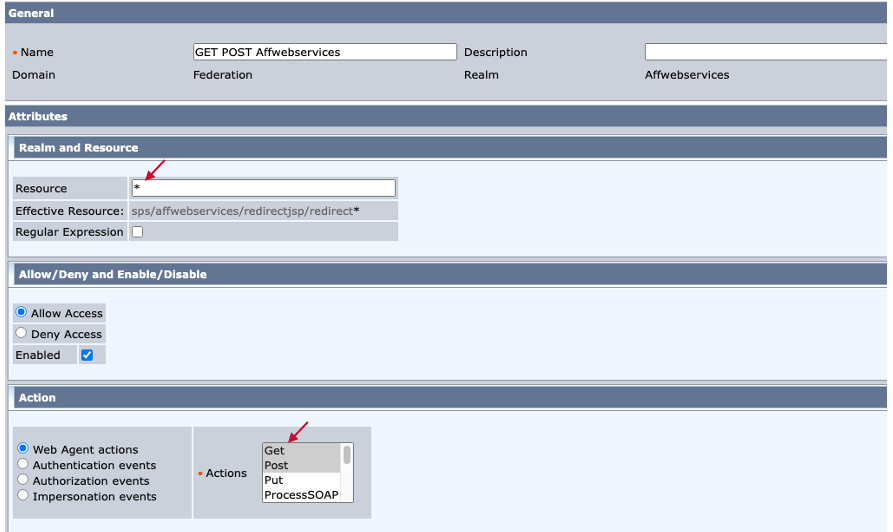
Step. F3. Create Rule under the Realm
Name: Any Name
Resource: *
Web Agent actions: GET, POST
Step. F4. Create Policy
Name: Any Name
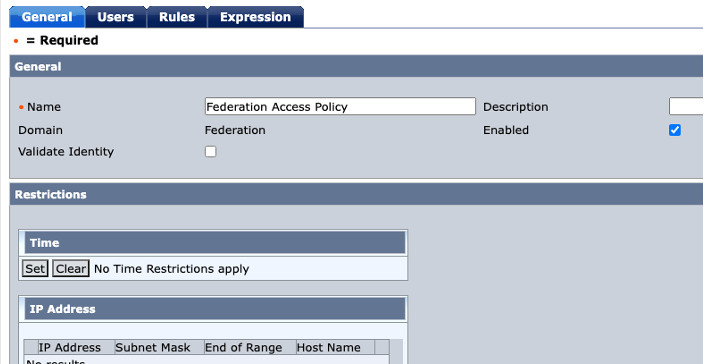
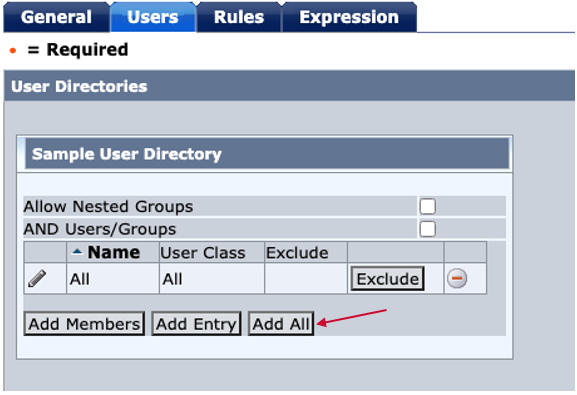
Click "Users" tab.
Click "Add All". It means that every user in the user directory can access the protected web page. Please change the user directory scope if required.
Click "Rules" tab.
Click "Add Rule" button and select the Rule, which is created in Step. F2.
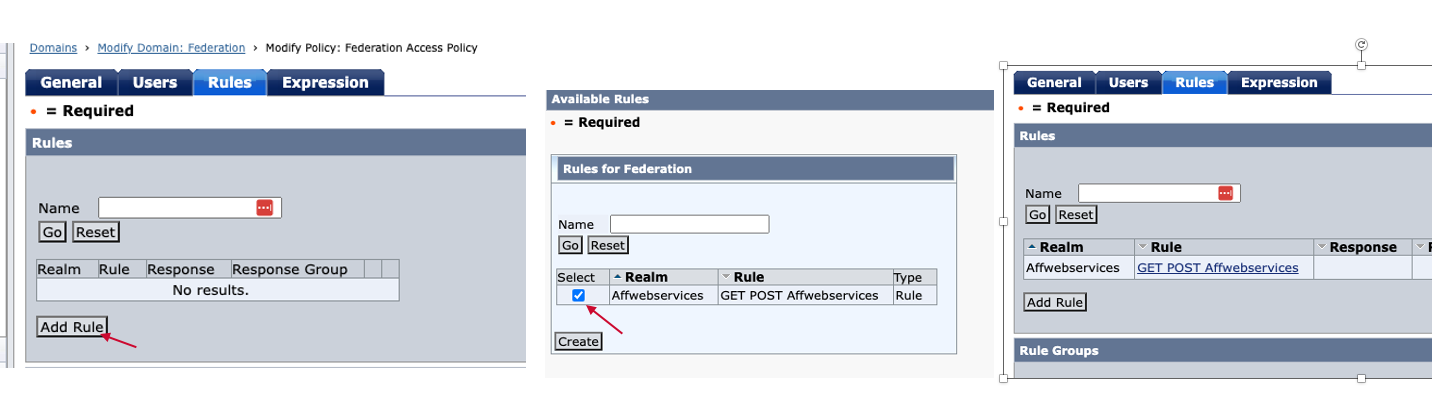
Once it is done, please "OK" button and "Submit" button to save the policy.
AWS Cognito SAML ONLY supports SP initiated Single Sign On. To do SP initiated SSO, please create a link or bookmark the page.
https://your_Amazon_Cognito_userpool_domain/authorize?response_type=code&identity_provider=your-SAML-IdP-name&client_id=your-client-id&redirect_uri=https://your_application_redirect_url
In this guide,
your_Amazon_Cognito_userpool_domain: demo-broadcom.auth.us-west-2.amazoncognito.com
identity_provider: SiteMinderSAMLIDP
client_id: 5hh6ajvu1o372caffu62jr56a
redirect_uri: https://wildrydes-firstname-lastname-bk.s3.us-west-2.amazonaws.com/index.html
When it initiates page in the browser, it is redirected to SiteMinder login page.

After login, SiteMinder generates SAML assertion, and the user can access AWS Cognito. With successful integration, there is cod=xxxx at the end of URI. It is authorization code.
In the Cognito User Pool, the user is created after successful SAML SSO.
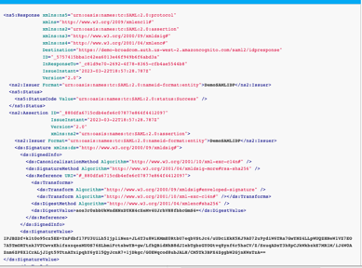
Using the SAML plug-in or SAML tracer in the browser, you can check SAML Assertions data.
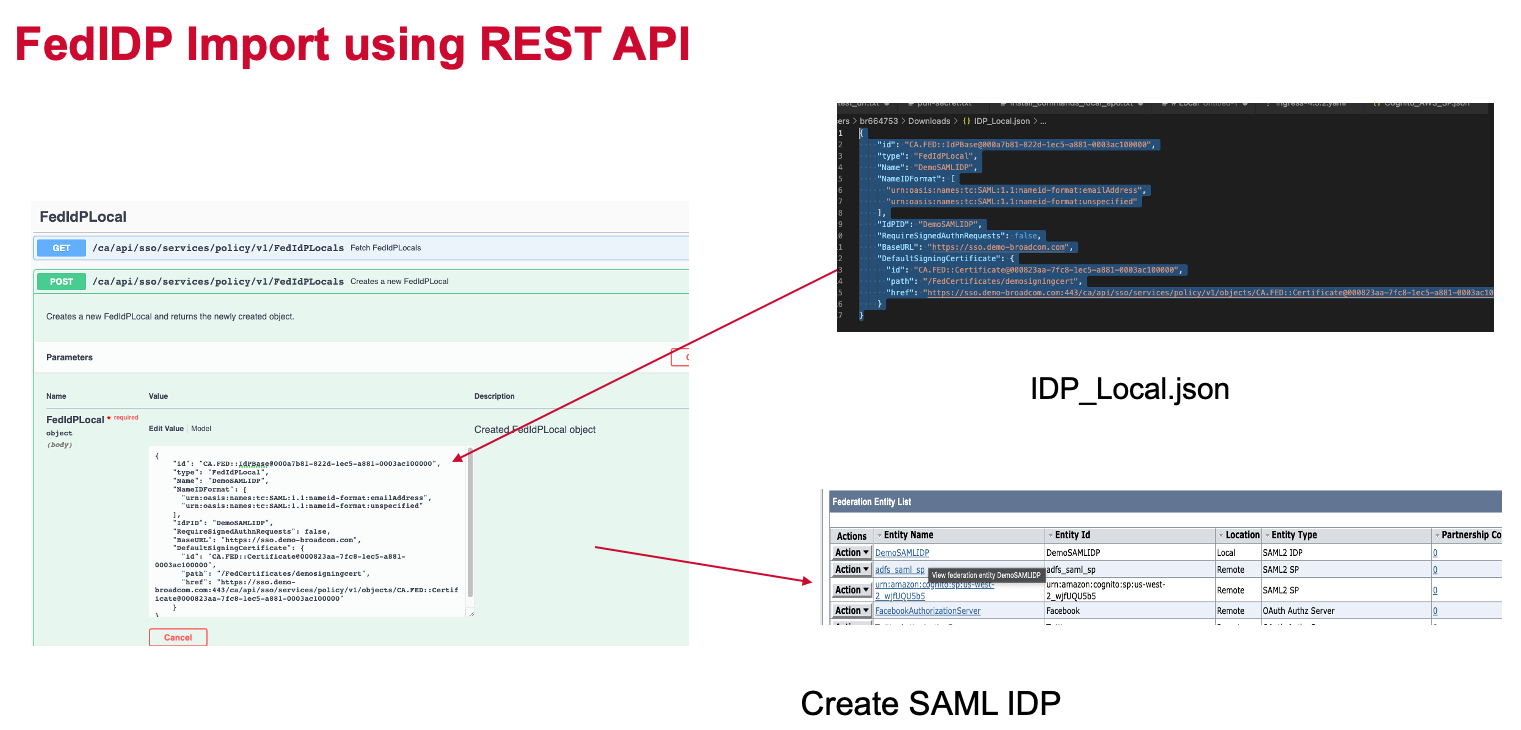
Configuration Files
SiteMinder supports REST API for Admin operation. It allows to import and expert federation related object. After import SAML SP and change the parameters based on your environment.
Congito_AWS_SP.json

As a reference, IDP json (IDP_Local.json) is attached. When you already set up SiteMinder IDP, please ignore this step.
When you import SAML partnership, please import it from FedSPPartnership REST API.
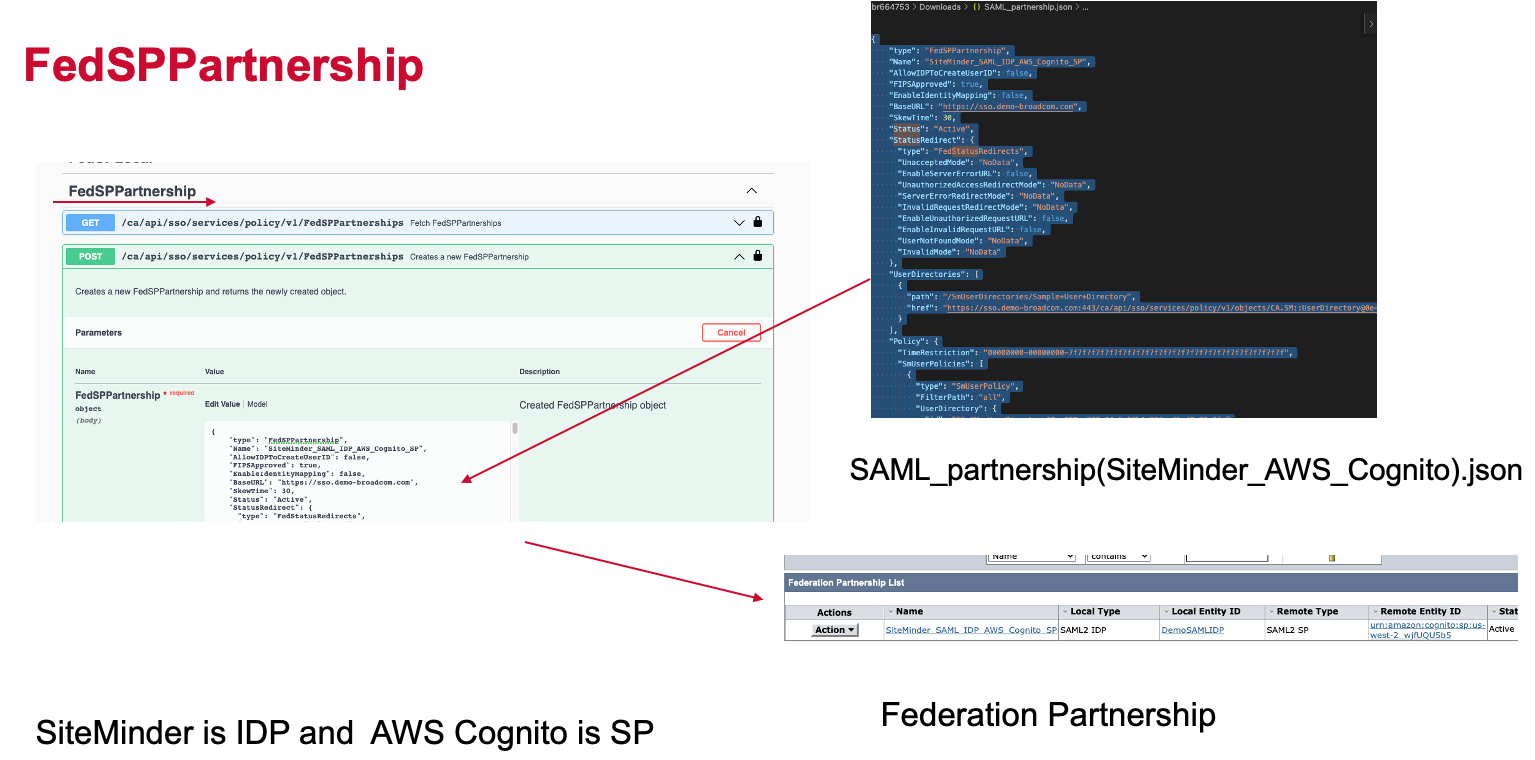
Please access the partnership and change the Federation partnership information based on the environment.
SiteMinder Identity Provider configuration
https://techdocs.broadcom.com/us/en/symantec-security-software/identity-security/siteminder/12-8/configuring/legacy-federation/configure-a-saml-2-0-identity-provider.html
AWS Cognito user pools
https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-user-identity-pools.html
AWS Cognito SAML Guide
https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-user-pools-saml-idp.html