I did open a case with Broadcom support, but ended up figuring this out on my own shortly afterwards. At first I was running into an issue where it would fail if I try to input the request data using JSON format, but works fine in XML format, but later found out that this is a bug with Access Gateway r12.8.6 and later. Broadcom Support sent me a patch class file which now allows me to submit a request with the data in JSON format.
The problem now is that it now accepts the request data in JSON format, but the response is only in XML format. I am not sure if this is still part of that bug or not. Can you let me know which version of policy server and AG you used in your POC/DEMO to get it to provide a response in JSON format?
Original Message:
Sent: Jul 05, 2023 12:22 PM
From: Bong-Kyun Rhim
Subject: How to pass the federated SAML SSO user's data to web application
Hi Duc Tran
Would you open a case and upload your access gateway web service logs?
It looks like the configuration issue and Broadcom support team needs to check your log files.
Kind regards
B.K.
Original Message:
Sent: Jun 30, 2023 07:25 PM
From: Duc Tran
Subject: How to pass the federated SAML SSO user's data to web application
Hi @Bong-Kyun Rhim ,
Thank you so much for providing this write-up. We are finally ready to start on this effort and I am now trying to setup a POC, but I am running into some errors (401 Access Denied), and I am hoping that you would have a few minutes to review this and provide me with a little bit of help.
Here is what I have done so far:
1) Enable the AG Web Services via the SPS admin UI - - > https://ws.accessgatewayhost.company.com
2) Create a new SM app Domain for the new web service virtual host:
a) create a realm to protect the resource https://ws.accessgatewayhost.company.com/authazws/
b) create a rule and response as you explained in your write-up to pass the SAML attributes as response headers via session variables.
After completing this setup, I then open a web browser to initiate an inbound SAML SSO to SiteMinder/Access Gateway, and after successful SAML authentication, I extracted the SMSESSION cookie from the web browser and then use it as the "sessionToken" value within Postman and POST it to https://ws.accessgatewayhost.company.com/authazws/
Below is the content of the body of Postman:
{ "action": "POST","sessionToken": "this-value-in-here-is-the-SMSESSION-cookie"}
The Postman response is always a "401 Access Denied". When I use the web browser to browse directly to https://ws.accessgatewayhost.company.com/authazws/ I then get prompted to authenticate via basic auth as configured in the realm and after authentication, I get a 404 response, but I do get an SMSESSION cookie.
In your write-up as well as in the tutorial video "Authentication and Authorzation Web Service", I noticed that you configured the realm to protect "/authazws/app1/ws/test.html", but where is the content for that path? In the Access Gateway I found that /authazws/ content is in this path: <AG_install_path>/Tomcat/webapps/CA_AuthAZ/ but in this directory I don't see the rest of the path "/authz/app1/ws/".
I don't know if Broadcom Support would be able to help with this, so I would very much appreciate any help that you could provide.
Thank you!
Original Message:
Sent: Apr 13, 2023 06:57 PM
From: Bong-Kyun Rhim
Subject: How to pass the federated SAML SSO user's data to web application
After saving SAML Assertion data into the session store, its data can be extracted via web service authorization call.
Namely, the web application can read the SAML IDP Assertion data using the web service call to access gateway with smsession cookie.
Here are the steps.
1. Install Access Gateway or use the existing access gateway to enable web service authentication and authorization.
https://techdocs.broadcom.com/us/en/symantec-security-software/identity-security/siteminder/12-8/configuring/access-gateway-configuration/configuring-the-authentication-and-authorization-web-services.html
2. Create a rule and response to read the data from the session store.
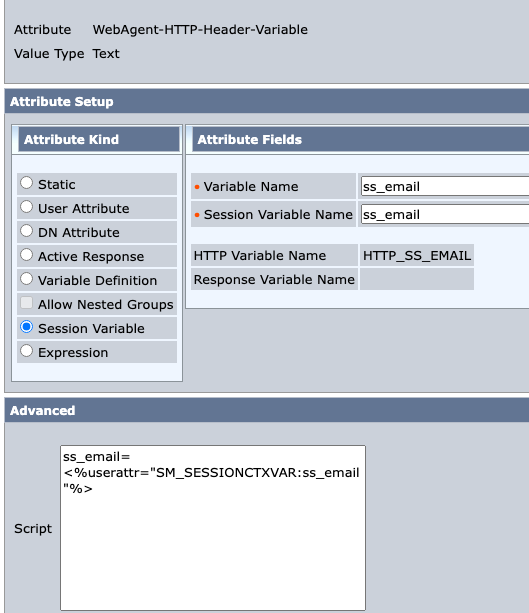
3. Using web service call with smsession, it returns json data from the session store.
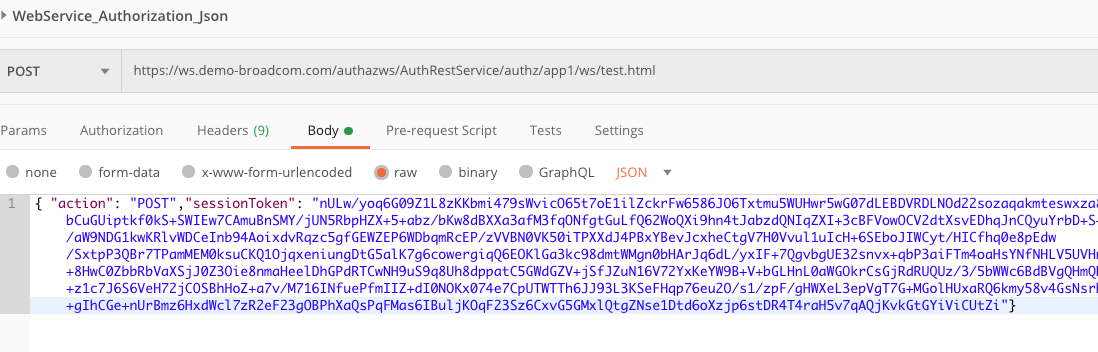
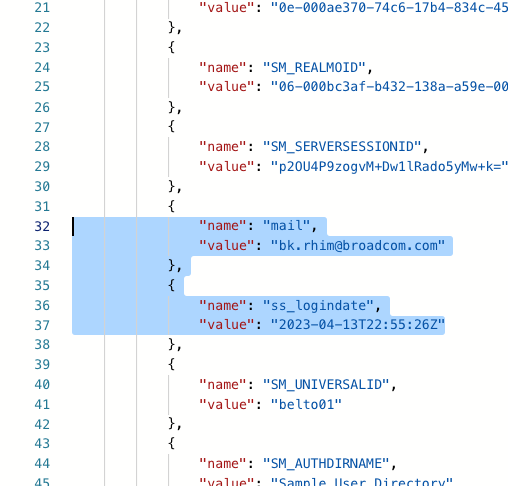
Please open a case if you need further information.
B.K.
Original Message:
Sent: Mar 24, 2023 12:26 PM
From: Duc Tran
Subject: How to pass the federated SAML SSO user's data to web application
Hello SiteMinder Community,
We have an open Broadcom support incident on this, but we are are hoping to get additional help from the SiteMinder community experts on this if possible.
We have a web portal which currently authenticate the users against our Symantec Directory Server user store and then allow the user to access the web application. The other method for the user to authenticate and access the application is via SAML SSO from their SAML IDP, and this is the method that we are trying to redesign.
With the SAML SSO flow, the SAML assertion is posted to SM Access Gateway and the SAML attributes data are then stored in the SM session store. The web agent would then generate HTTP request headers with the user's SAML data that is stored in the session store and then redirect the browser to the application. Due to security concerns from InfoSec, we are asked to stop using HTTP request headers to pass the user's data to the web application.
We are now pursuing other methods of passing the user's data in the inbound SAML assertion to our web application and hoping that either Broadcom support or folks from the community could provide some advice.
Thanks!