Team,
I have found two (2) JAVA processes, that others have created, useful to debugging.
I have incorporated these into test scripts to validate proper configuration is setup.
1) A view of which SSL/TLS protocol is enabled with local Java deployment (aka java.security file)
Java Examples: Enabling SSL v3.0 in java 8
2) A view if the Java JCE was deployed on local deployment
A basic sanity test of the local AES key length. · GitHub
Building these little java programs can be done with the JDK's javac program; and added to your DevOps Scripts.
Example for SocketProtocols.java
A) Create a new file called SocketProtocols.java
import javax.net.ssl.*; public class SocketProtocols { public static void main(String[] args) throws Exception { SSLSocketFactory factory = (SSLSocketFactory) SSLSocketFactory.getDefault(); SSLSocket soc = (SSLSocket) factory.createSocket(); // Returns the names of the protocol versions which are // currently enabled for use on this connection. String[] protocols = soc.getEnabledProtocols(); System.out.println("Enabled protocols:"); for (String s : protocols) { System.out.println(s); } }}

B) Execute %JAVA_HOME%/bin/javac SocketProtocols.java
- Assumes this file is in the path
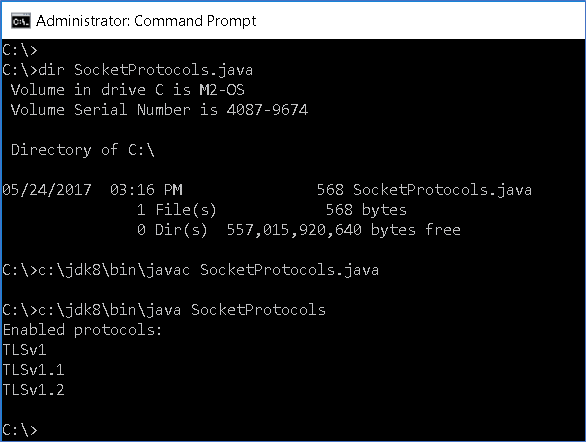
C) Execute the new Java program to see which protocols are enabled within your current version of Java.
- Older versions of Java (server/workstation) may have SSLv3 enabled.
- This test will help when trying to connect to older servers, that are still using SSLv3 or older protocols, that are not supported. False negative error message, that state "bind incorrect" may appear, if the protocol is too old. Avoid this "rabbit hole" for troubleshooting SSL/TSL challenges.
Example for CipherTest.java
A) Create a new file called CipherTest.java
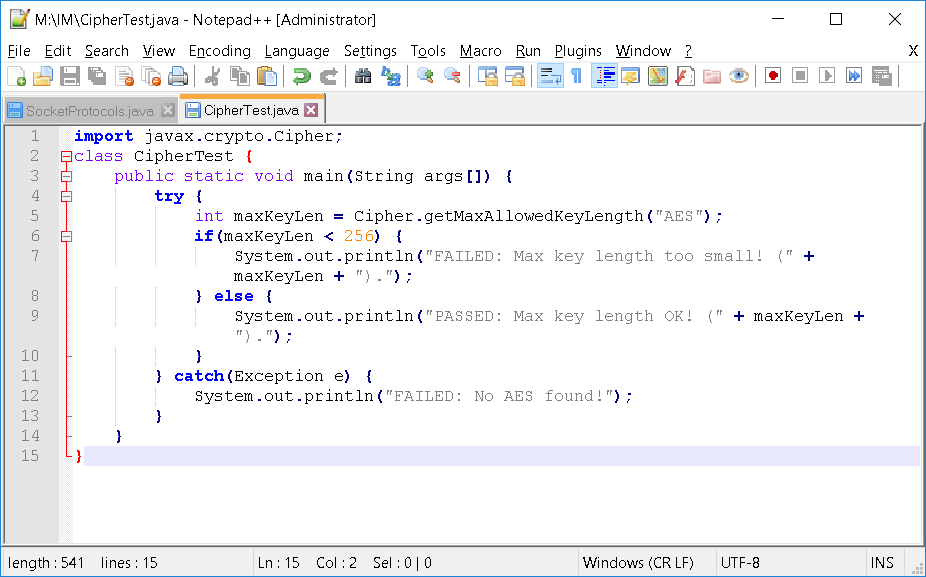
import javax.crypto.Cipher;
class CipherTest {
public static void main(String args[]) {
try {
int maxKeyLen = Cipher.getMaxAllowedKeyLength("AES");
if(maxKeyLen < 256) {
System.out.println("FAILED: Max key length too small! (" + maxKeyLen + ").");
} else {
System.out.println("PASSED: Max key length OK! (" + maxKeyLen + ").");
}
} catch(Exception e) {
System.out.println("FAILED: No AES found!");
}
}
}
B) Execute %JAVA_HOME%/bin/javac CipherTest.java
- Assumes this file is in the path
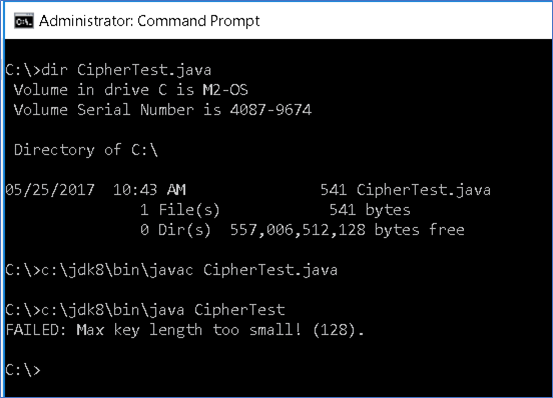
C) Execute the new Java program to see if the JCE has been deployed in within the current version of Java.
- If not, then a failure message will report this.
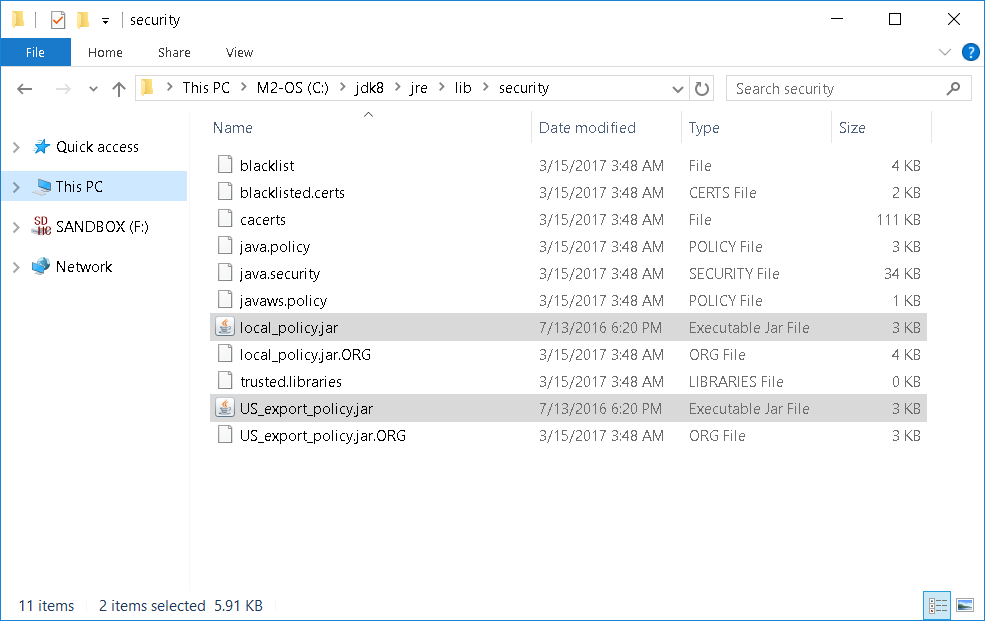
D) Deploy the Oracle Java JCE's two (2) JAR files, and then retest with this java script

What small java process have you added to your testing/validation processes?
Cheers,
A.