Team,
The Identity Suite vApp is very popular, and more so for quickly set up/execution of Governance Campaigns.
While we wish to leverage the Identity Management solution as the primary source & closed-loop channel for the Identity Governance solution, there are customers that have not deployed nor require the full closed-loop process as part of their maturity model.
From the vApp help guide review of support deployments, we see a configuration listing IG and IP with a database.
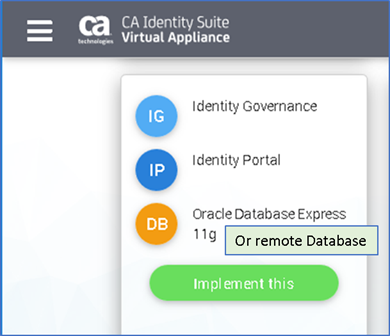
Challenge: The Identity Suite vApp assumes that a remote IAMCS connector will be managed by the Identity Management solution.
- This assumption works well for many customers that wish to future proof their expected use of Identity Management for Role Engineering & Closed-Loop auto-deprovisioning of access; with integration with Identity Governance.
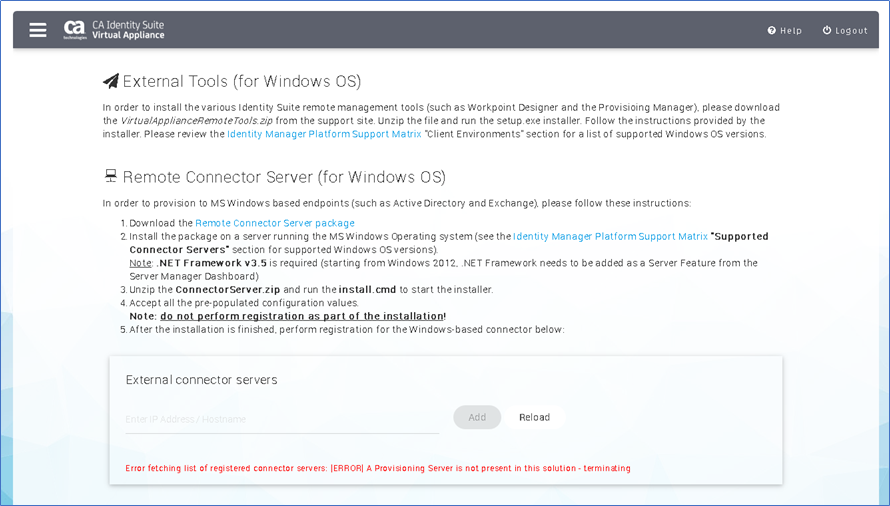
- The configuration page for a remote IAMCS is setup to download a pre-built configuration IAMCS connector (via a link) from the vApp, and a 'registration page' link to complete the setup.
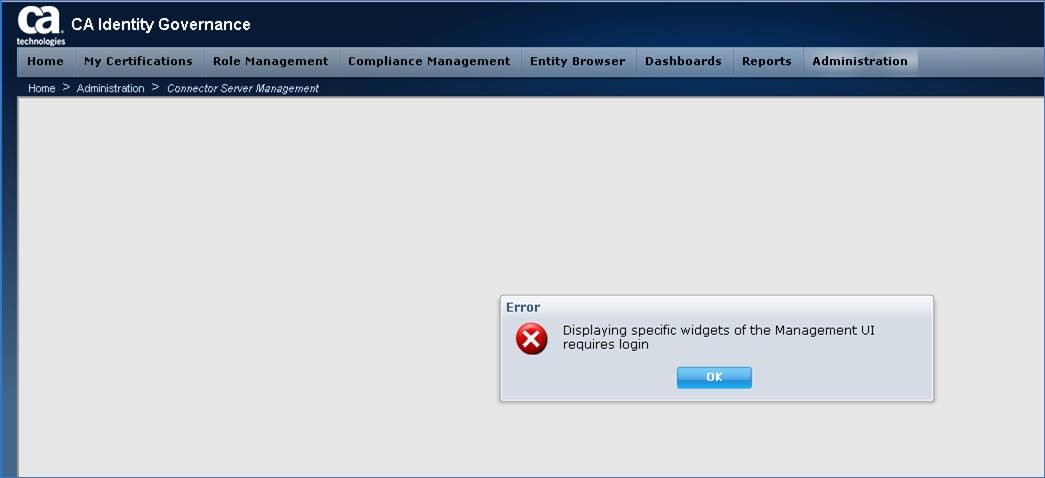
Error message (below) will appear if a local IAMCS connector server has not been deployed, or before updating IG to use a remote IAMCS connector server.
Proposal: Out line the steps to use an IP + IG "non-production or production" deployment using the Identity Suite vApp with an external database and remote IAMCS (and CCS) connector server.
For this exercise, we will update IG configuration to use an embedded vApp IAMCS connector and redirect it to a remote IAMCS connector.
Pre-Steps:
a) Minimal Architecture:
1-vApp Identity Suite Server (to deploy IP and IG) [8-16 GB RAM,4-8 vCPU],
1-MS Windows Server Standard 2012 R2/2016 [To allow full use of the CCS connector server to MS-AD or other CCS endpoints]
1-Database Server [May use embedded Oracle XE for sandbox, but Prod deployment require external DB, ensure XA configurations are updated on MS-SQL server, if using MS-SQL]
b) Follow the steps in the vApp Remote Connector server from step 1-4. Or may use an existing IAMCS connector server or deploy a new IAMCS from installation discs/iso.
c) Ensure OS Firewalls allow IAMCS Ports to/from TCP 20080/20410 (non-TLS) or 20443/20411 (TLS) or both
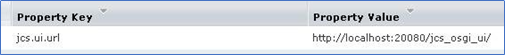
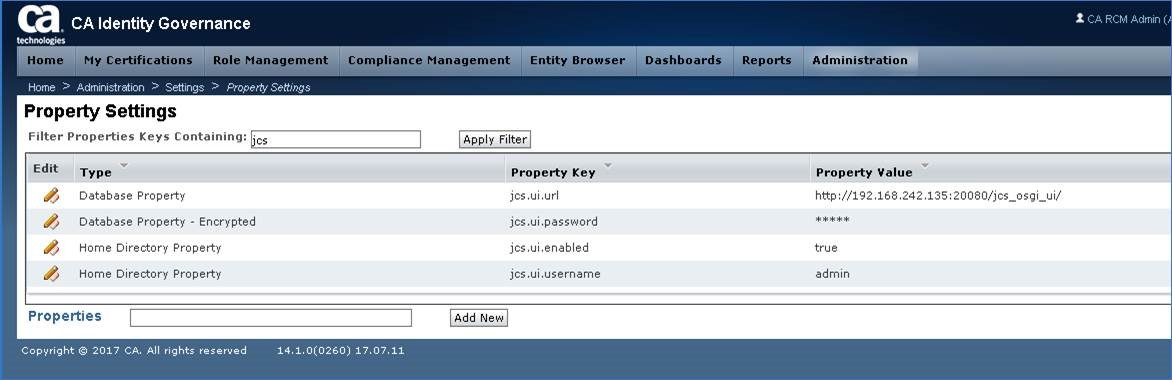
Step 1: Update IG Property Settings; change default of localhost IAMCS URL to remote server URL
IG Management Console/Administration/Settings/Property Settings
Search for key work: jcs
Four (4) fields will display. We will update two (2) of them: URL & Password.
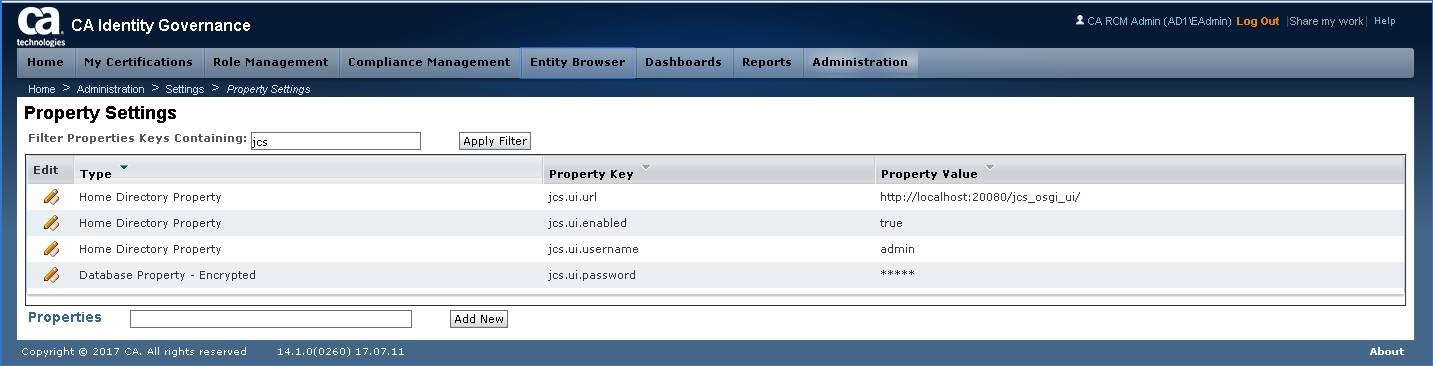
Step 2: Select jcs.ui.url. Note that default entry for TYPE shows "Home Directory Properties" but updates will display "Database Property"
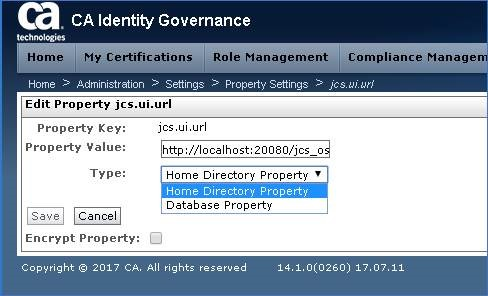
Step 3a: Validate that remote IAMCS ports are not blocked for TCP 20080
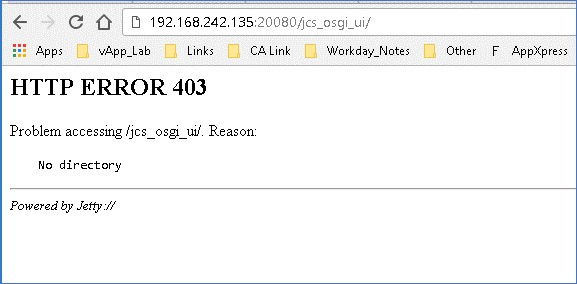
Step 3b: Same for TCP 20443
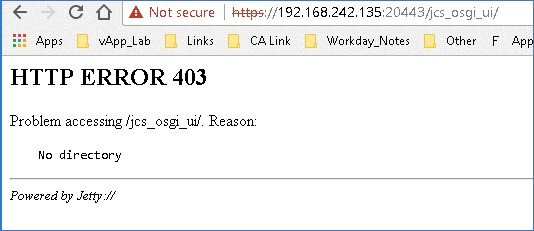
Step 4: Validate the credentials to the IAMCS service [default login id: admin password: install_password]
URL http://iamcs_hostname:20080/main or https://iamcs_hostname:20443/main
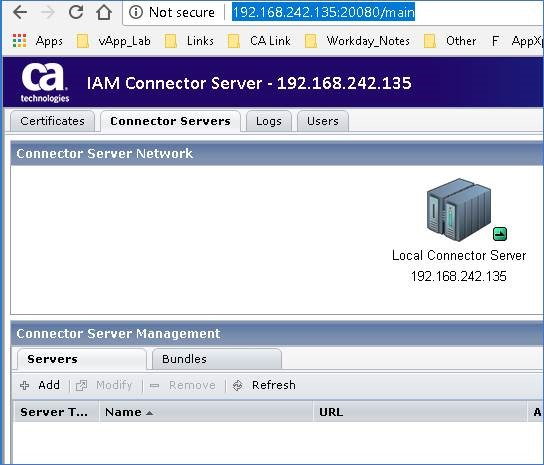
Step 5: Enter the new remote IAMCS URL (use either 20080 or 20443)
URL: http://iamcs_hostname:20080/jcs_osgi_ui
[Note: If using TCP 20443 and the remote IAMCS is using a non-install replacement CA/Server certificate, it will be necessary to add the public CA cert to the vApp]
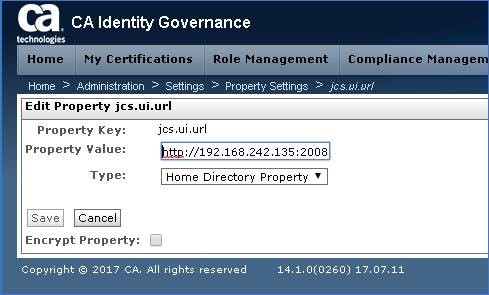
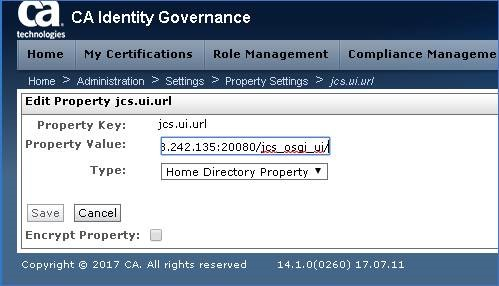
Step 6: Switch the TYPE to "Database Property" and click Save
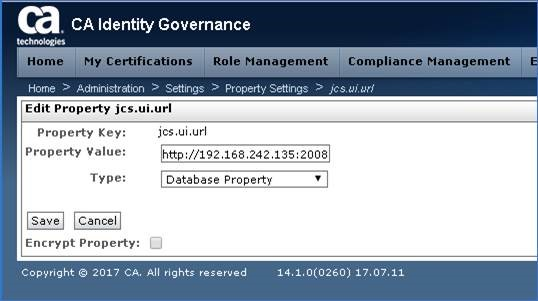
Step 7: Observed the updated property in the IG screen
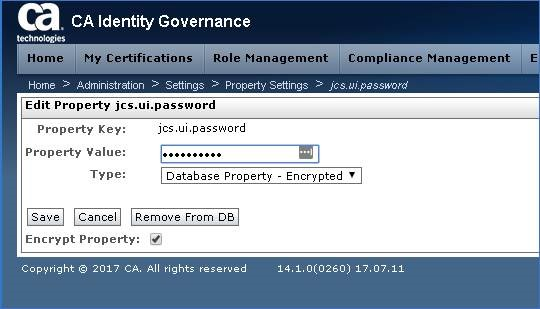
Step 8: Select jcs.ui.password & update the IAMCS service IDs password & Click Save
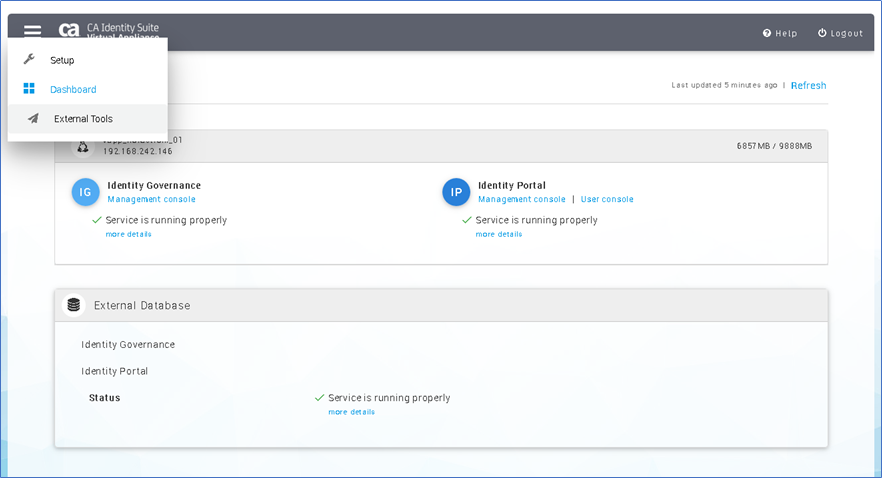
Step 9: Navigate to the IG Connector Server Management (under Administration) Screen
- The screen should no longer display any error message, and the drop-down boxes will now display.
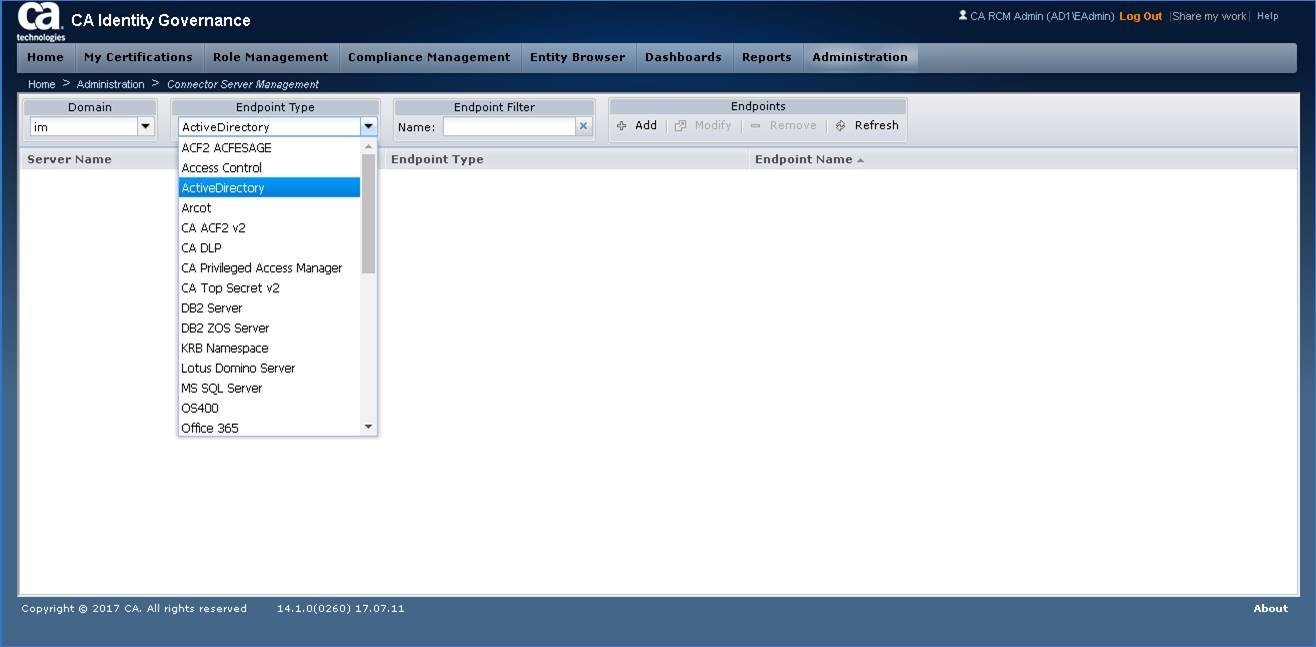
SUCCESS
Validation Process:
If you already have an endpoint, define it here and vet that the remote IAMCS connector server is able to display if for IG use.
Below is an example to use IG objectstore DB as a quick test to demonstrate this configuration is validate, that we will remove afterwards. This example uses MS-SQL Express 2014.
Step 10: Validate that IG db login credentials are correct. May use Database GUI tools to confirm.
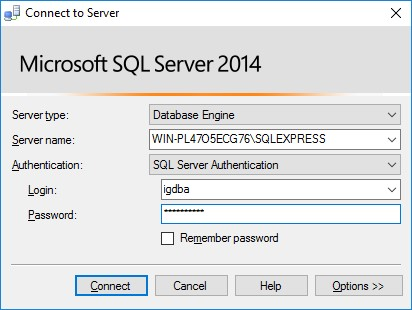
Step 11: Ensure that the login credentials have access to view a database
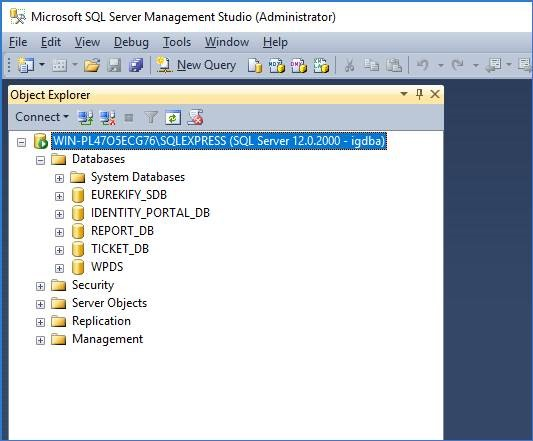
Step 12: Within IG Connector Server Management, add the endpoint with the hostname/URL and credentials.
Below example is with a database thin JDBC URL format & the db login credentials.
- JDBC URL format. May be confirmed prior with a 3rd party tool, e.g. DbVisualizer.
- Example:
- jdbc:mssqlserver://HOSTNAME:PORT;DatabaseName=DATABASE_NAME
- jdbc:oracle:thin:@HOSTNAME:PORT:DATABASE_NAME
- Failover Example:
- jdbc:sqlserver://NT_DOMAIN\HOSTNAME:PORT;selectMethod=cursor;DatabaseName=DATABASE_NAME;failoverPartner=NT_DOMAIN\HOSTNAME:PORT
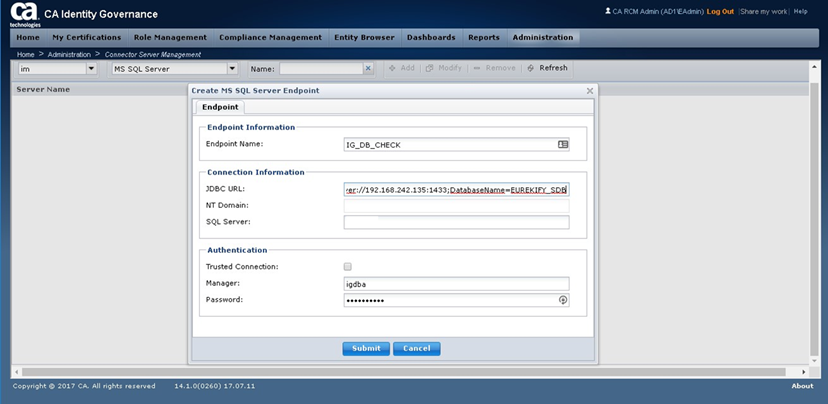
Step 13: Validate the new endpoint displays in the IG screen
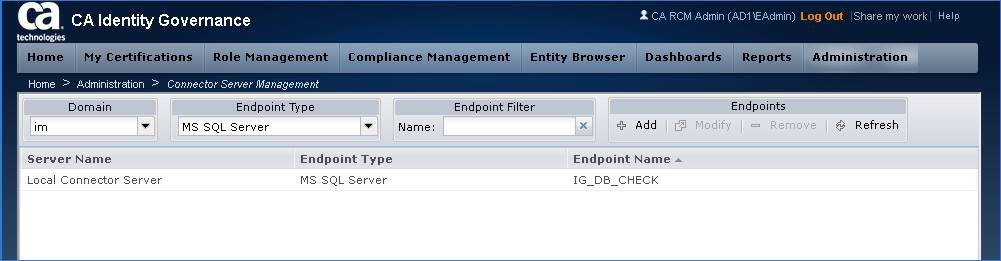
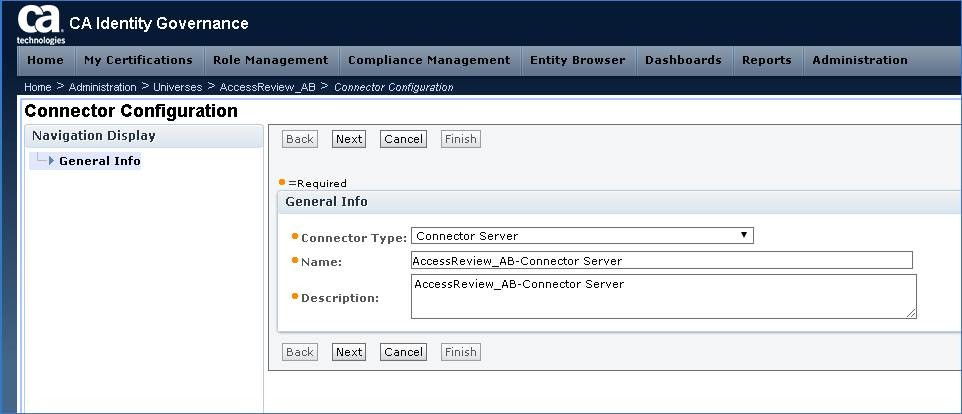
Step 14: Navigate to a new or existing IG Universe, & select Connector Configuration Button.
When new screen opens for Connector Configuration, use the drop-down box, to select "Connector Server"
Then select NEXT.
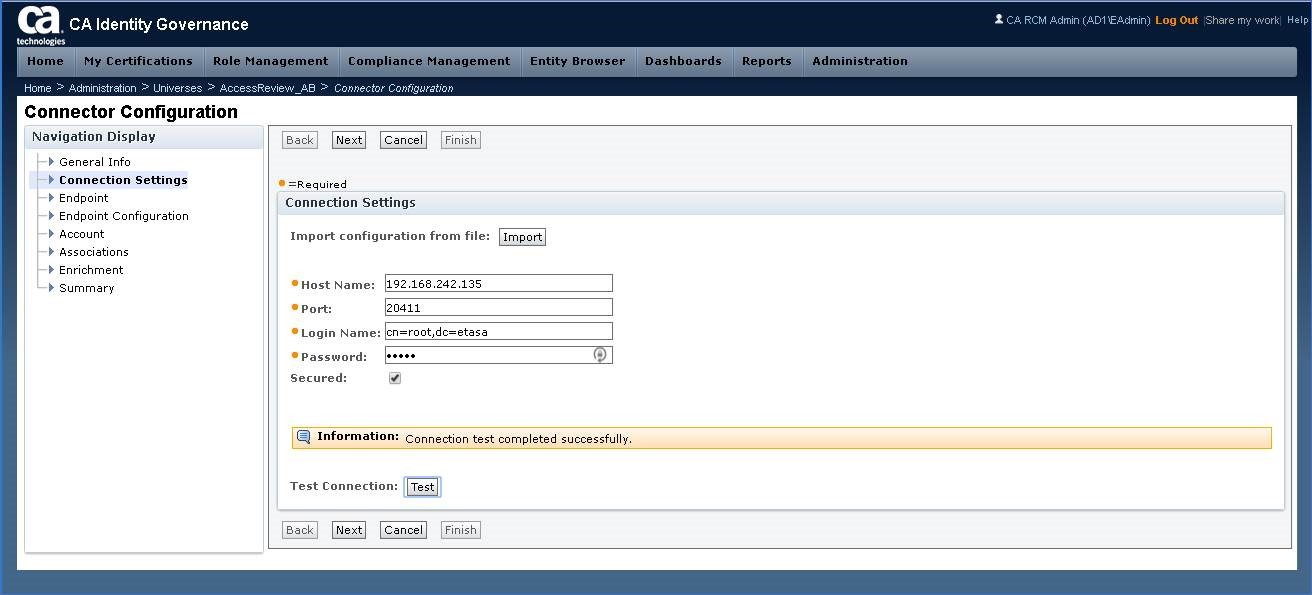
Step 15: Update the endpoint connector Settings for hostname/credentials & use the TEST button.
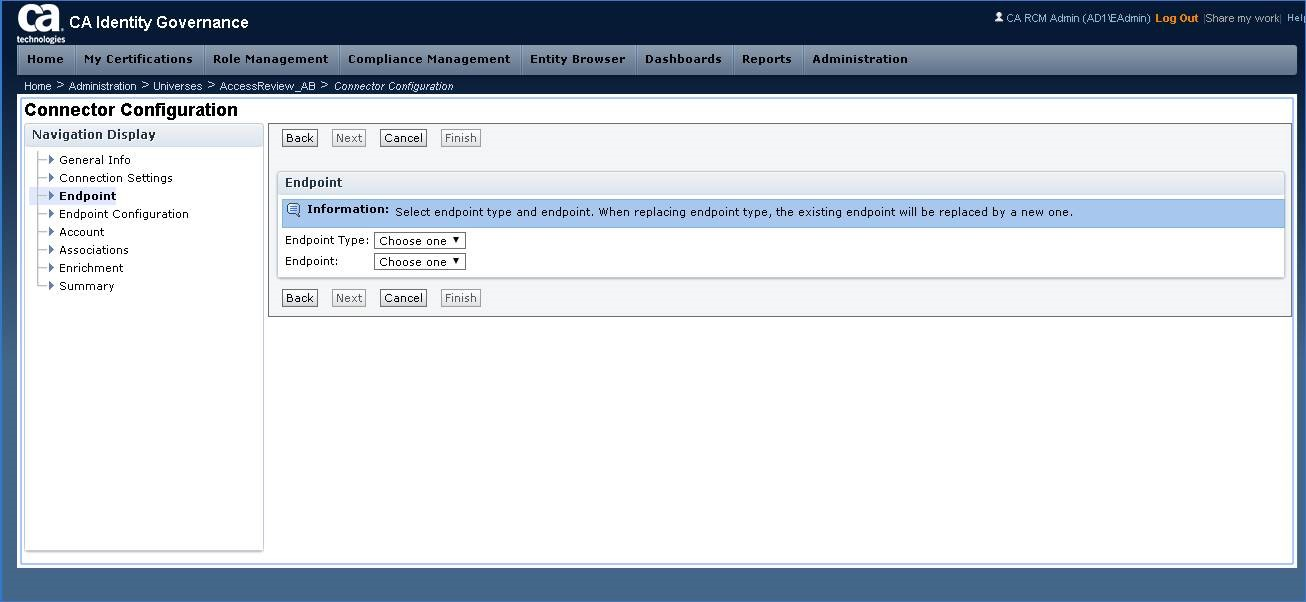
Step 16: Continue through the rest of the Connector Configuration setup screens. See below for example
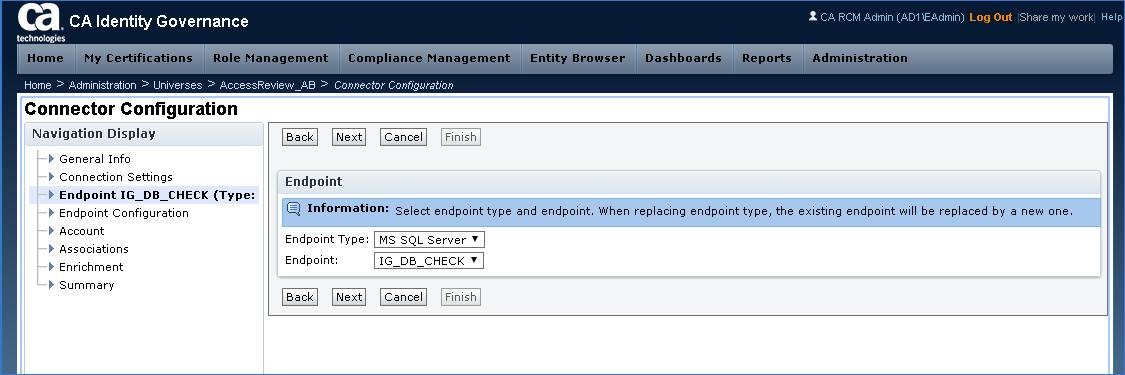
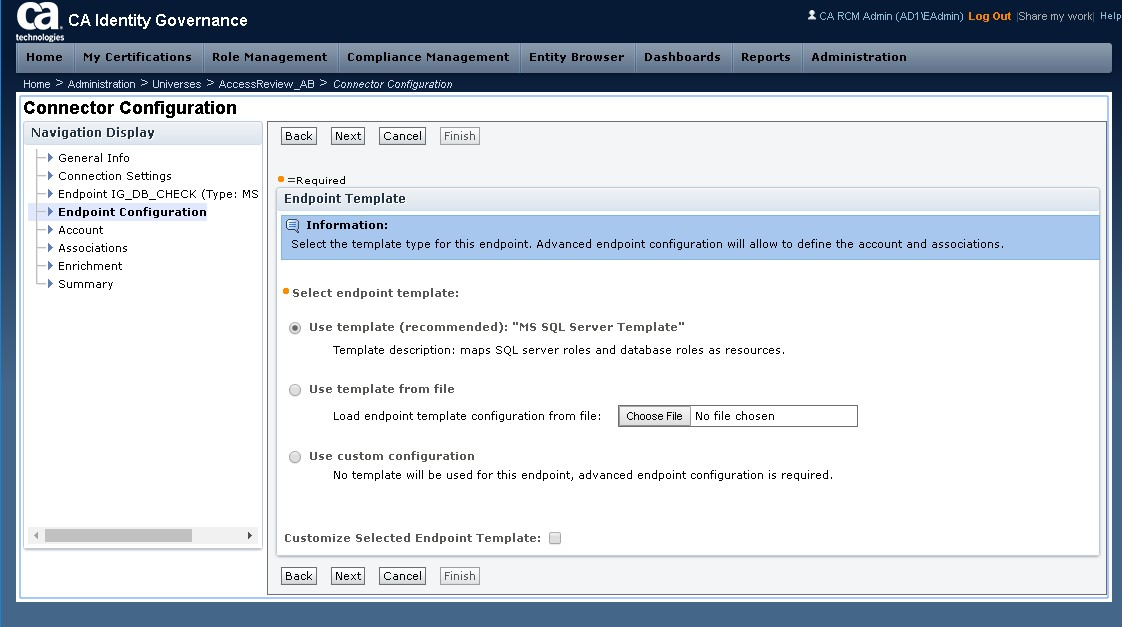
Step 17: Review settings, then click FINISH button.
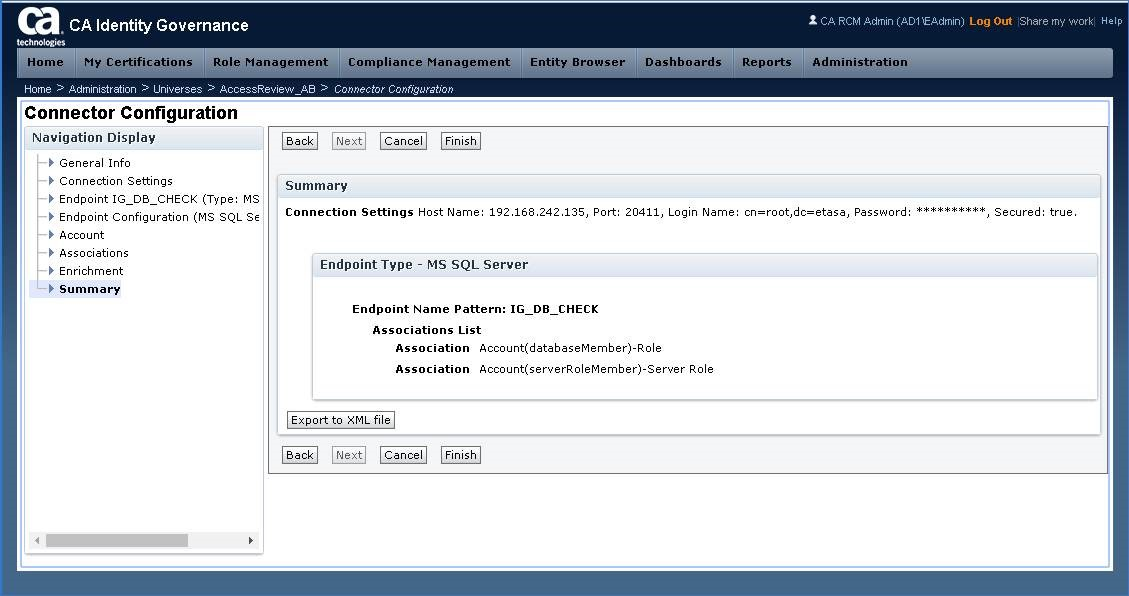
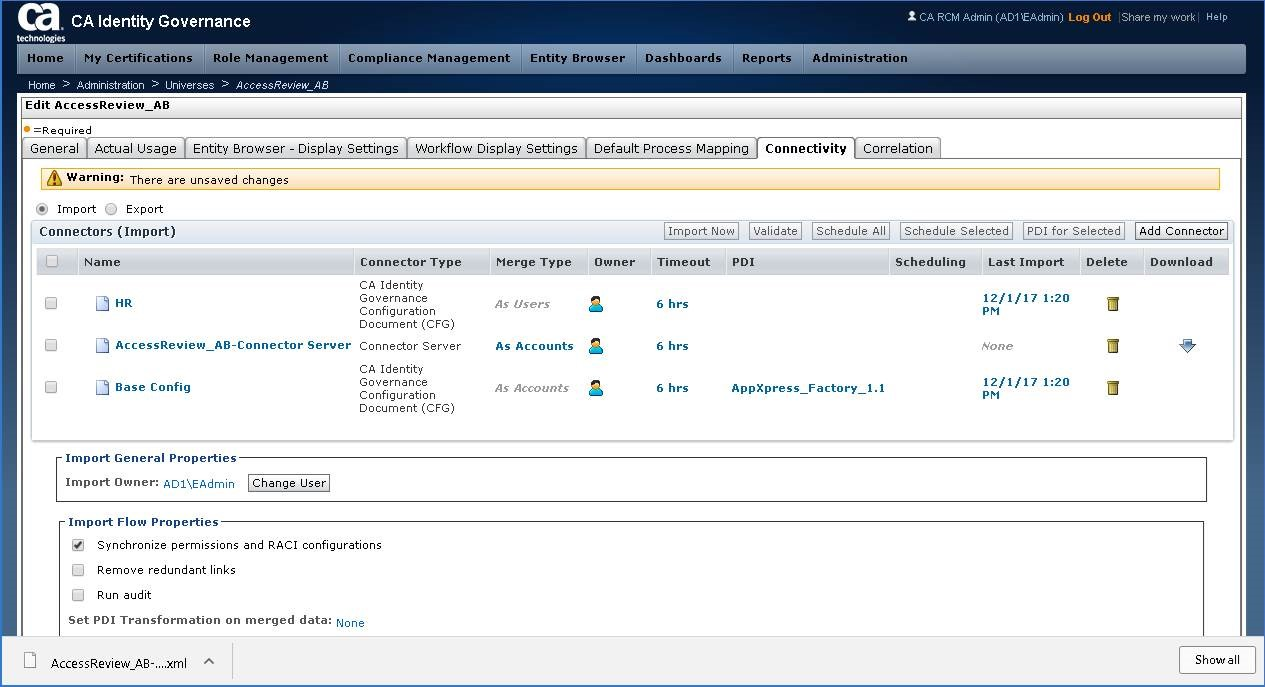
Step 18: Validate Universe has a new Connector.
Example below: AccessReview_aB-Connector Server, Connector Type = Connector Server
Other connectors were defined using IG CFG (shown as contrast)
Clean-Up Activity:
Step 19: If endpoint used for validation was the IG objectstore, please remove it.
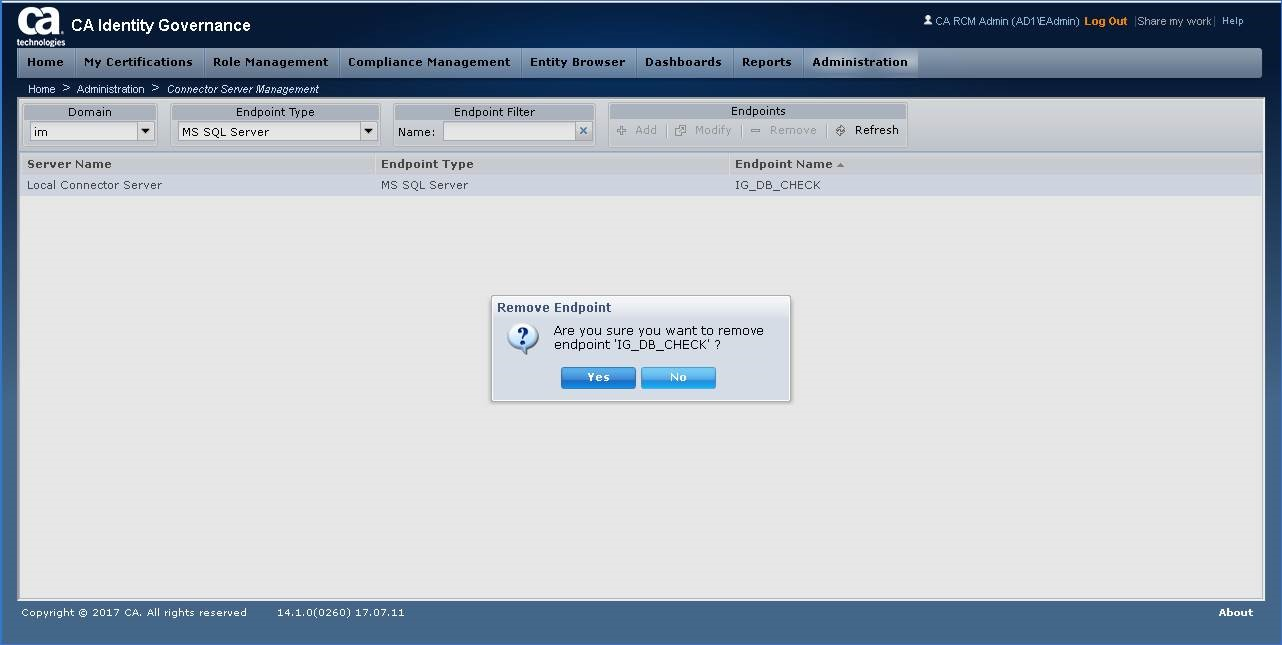
Additional Notes/Error Messages:
If the IG db login ID is missing permissions for XA configuration, you may see this message.
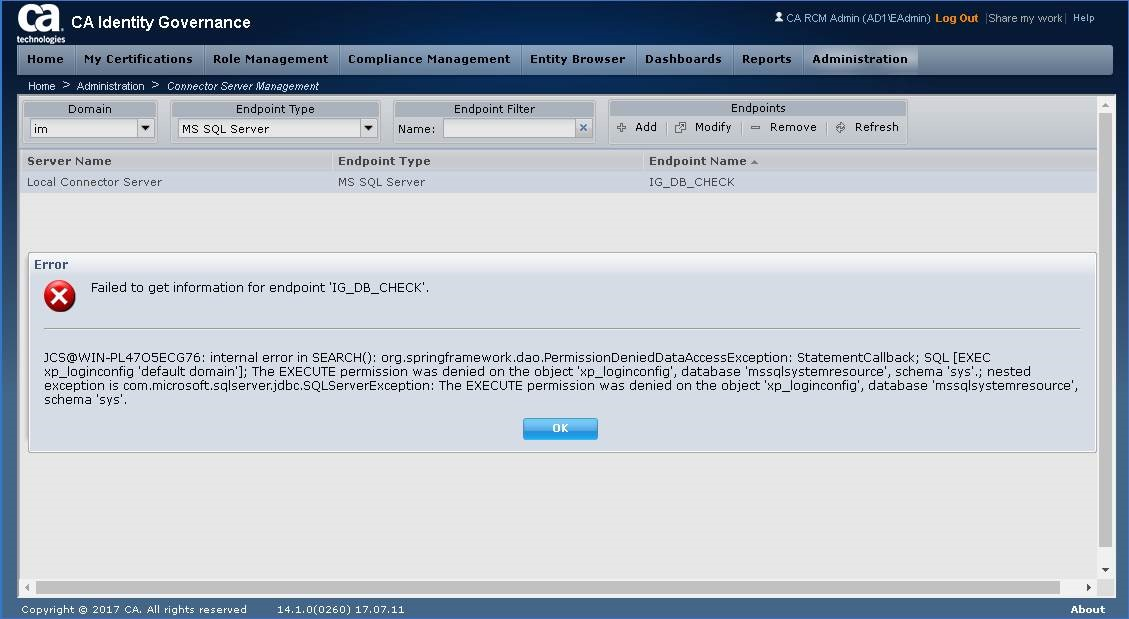
Adjust your MS-SQL database/server configuration as noted in wiki/readme.
See this link for additional information.
Identity Suite vApp - IP & IG Deployment Model with external database (MS-SQL)
Let me know if this was useful.
Cheers,
Alan