Summary
Environment
PS : r12.5 and above
Instructions
To default CA SSO generated user attributes can be accessed using the SmUserContext.getProp(java.lang.String propName) API call as below.
In the example below, we are accessing the default CA SSO response attribute : SM_USERIPADDRESS
public String
invoke(ActiveExpressionContext context,
String param)
throws Exception
{
if (context == null)
{
throw new IllegalArgumentException("ActiveResponseSample invoked without context");
}
UserContext theUserContext = context.getUserContext();
if (theUserContext == null)
{
context.setErrorText("No User Context.");
return null;
}
return theUserContext.getProp("SM_USERIPADDRESS");
}
Step 1: Create an active response as shown below :
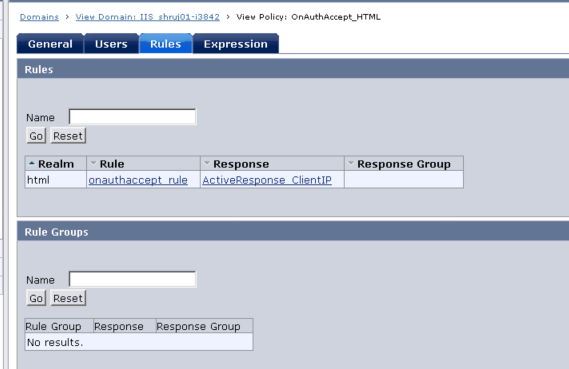
Step 2 : Configure the Active Response with either OnAuthAccept or OnAccessAccept rule.
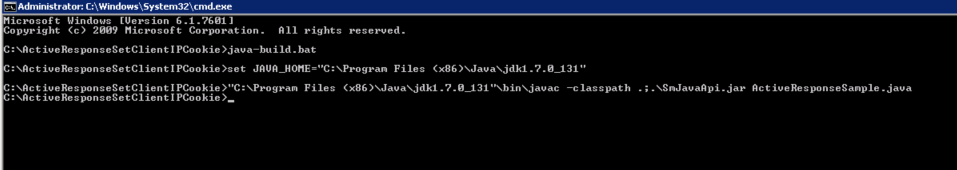
Step 3 : Compile the attached sample ActiveResponseSample.java class by running java-build.bat (windows) /java-build.sh (unix).
Note: Prior to running you will need to update the path to the JDK install directory in the JAVA_HOME variable by editing the java-build.bat (windows) /java-build.sh (unix) files.

Step 4. Once compiled, copy the ActiveResponseSample.class and copy it to the <Policy server>/config/properties directory.
Note: This "properties" directory is by default in the classpath of Policy server so you don't need to modify JVMOptions.txt.
If you choose to deploy the class in any other directory, then you will need to add the path to that directory as a classpath in the JVMOptions.txt file.

Test:
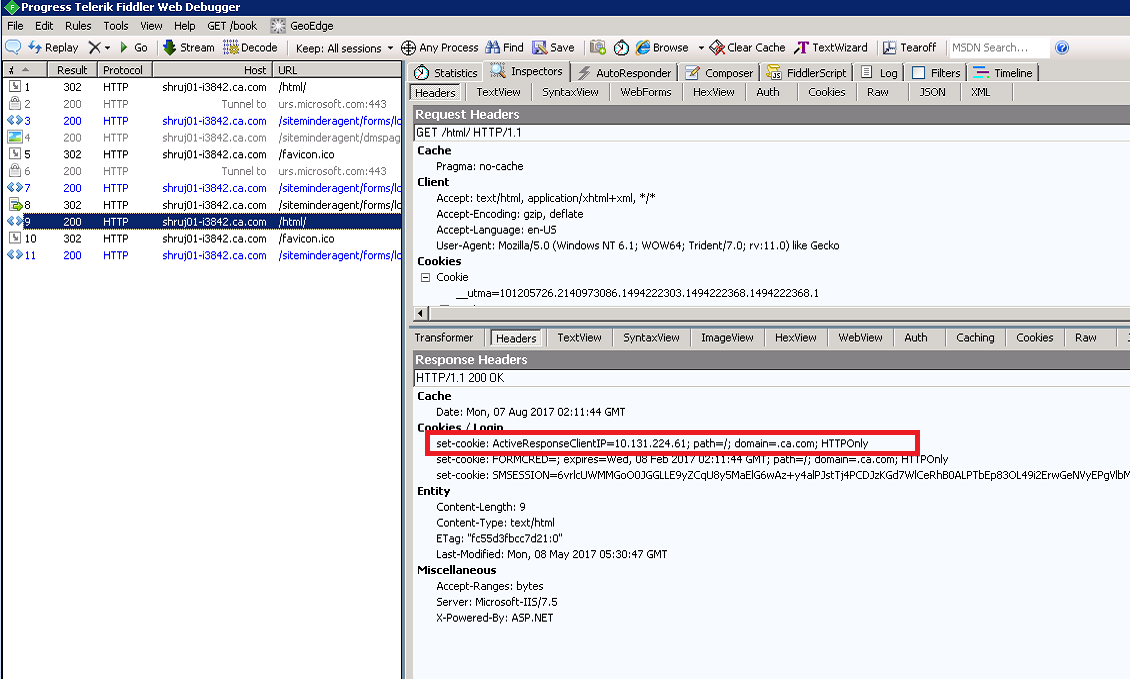
Policy server Trace Log :
[08/07/2017][01:30:07][2908][1564][][SmAuthUser.cpp:700][ServerTrace][][][][][][][][][][][][][][ActiveResponseSample: ActiveResponseSample:: returning ClientIP= ['10.129.160.255']][01:30:07.792][][][][][][][][][][][][][][][][][][][][][][][][][][][][][][][ActiveResponseSample:: returning ClientIP= ['10.129.160.255']][][][][][][][][][][][][][]
Additional Information