Summary:
In this guide we will see how to configure OAuth 2.0 Partnership Federation between CA SSO (OAuth Client) and Google (OAuth server)
Pre-requisites:
- CA SSO 12.52 and above
- CA SSO Federation web services with HTTPS access. The X.509 Certificate MUST have been signed by a trusted Certificate Authority such as VeriSign, Entrust etc. This is a requirement from the OAuth providers like Google, Facebook etc. ( I got it for free for my domain from startssl.com which comes with 1 year validity)
- Access to Google Cloud Platform account (https://cloud.google.com)
Instructions:
Configure OAuth Authorization in Google IDP
1. Login to Google cloud platform (https://cloud.google.com)
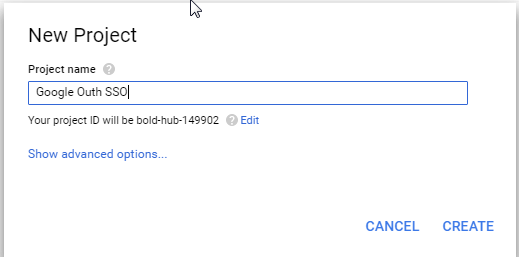
2. Create New Project --> "Google Oauth SSO"
3. From the top left drown menu , choose the new project that you just created
4. Double Click --> "Use Google APIs"
5. Click "Create Credentials" drop down menu and select "OAuth Client ID"
6. Before creating "OAuth Client ID" it is a requirement to set a Product Name to identify your Google App in the consent screen, so click "Configure Consent Screen"
7. Specify Product Name (as shown to users) , e.g "CA SSO" and click Save.
8. Now, choose the Application Type = "Web Application" and specify the value as below and click Create:
- Authorized Javascript Origins = <Your SP home page>
- Authorized Redirect URIs = <SP Base URL>/affwebservices/public/oauthtokenconsumer/google<OAuth ClientID>
Note :
- As we don't know the OAuth ClientID yet , give any placeholder character like XXXX
- The Authorized Redirect URI is same as the "Redirect Url" that will be configured for OAuth 2.0 Local Entity later
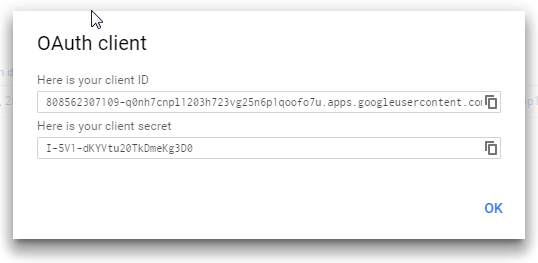
9. Once the OAuth ClientID is created it will be displayed along with the Client Secret.
These will be required while configuring entities and partnership in CA SSO so make a note of it.

10 . As we haven't provided the actual ClientID in the "Authorized Redirect URI" in step 8 above, so we need to go back and edit the newly created ClientID by clicking the edit button (pencil icon).
s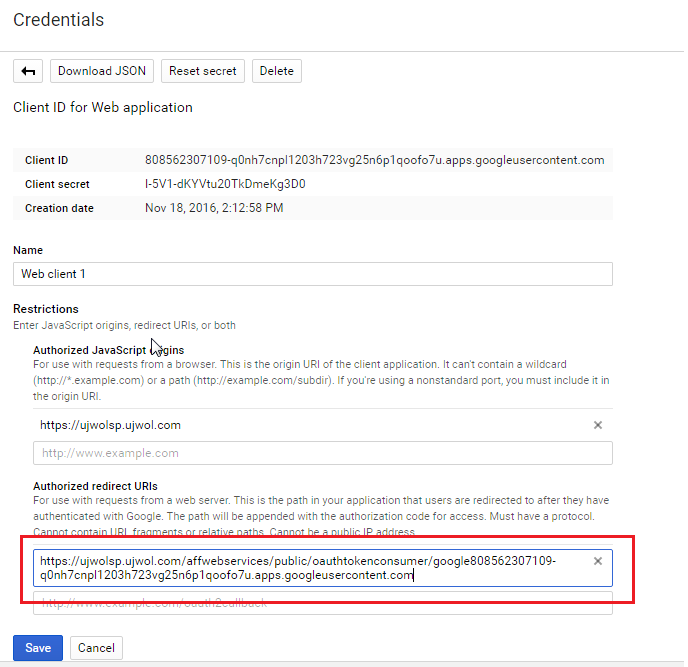
Configure OAuth client in CA SSO:
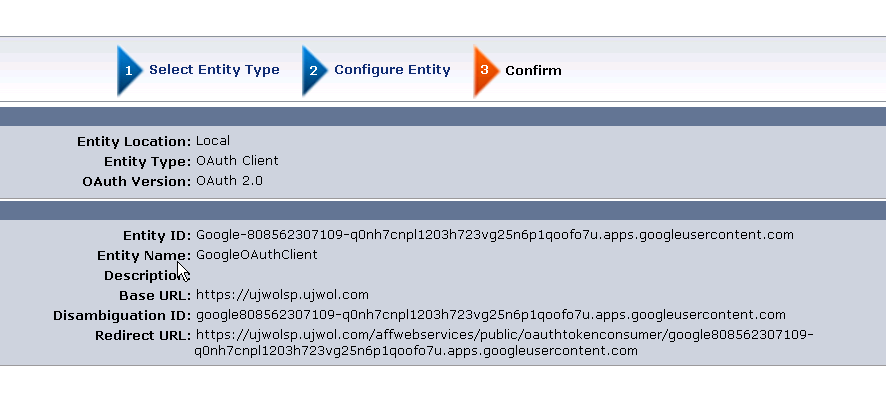
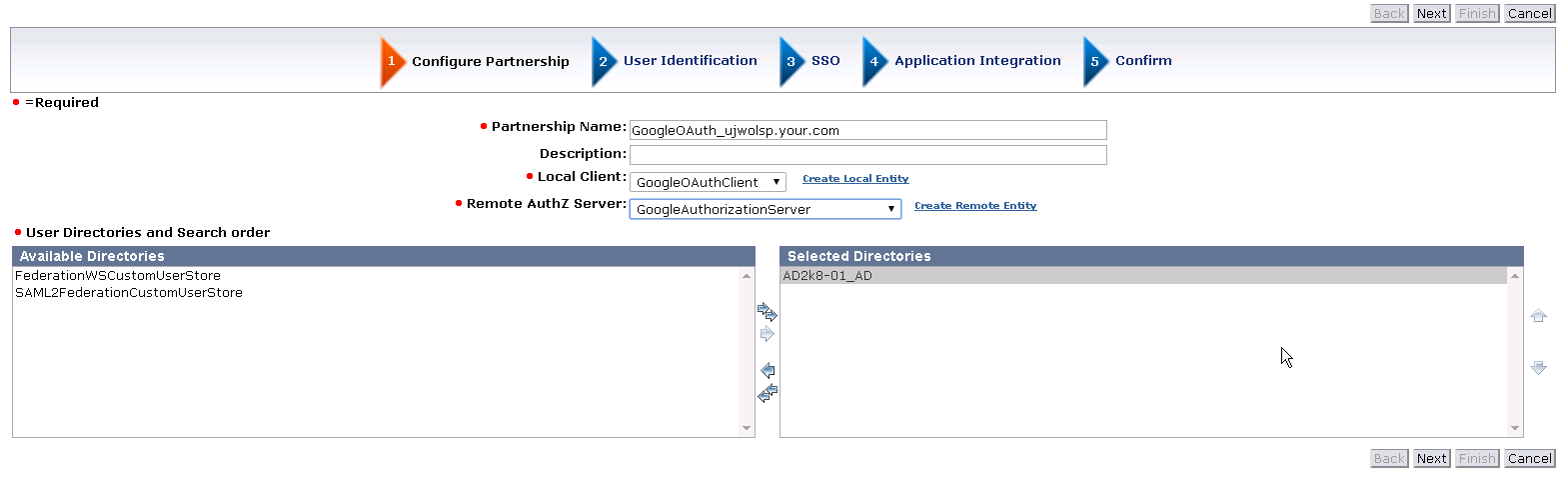
1. Login to Admin UI and Create Entities under Federation > Partnership Federation as below : 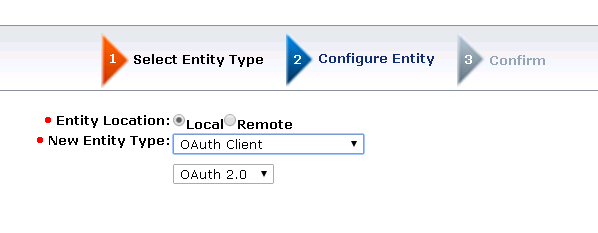

Note :
- Entity ID : Google-<OAuth Client ID> (note the hyphen - )
- Disambiguation ID : google<OAuth Client ID>
- Redirect URL : <SP Base URL>/affwebservices/public/oauthtokenconsumer/google<OAuth ClientID> (same value as Authorized Redirect URI in OAuth Client ID creation setup in Google Cloud )
2. Note, it is not needed to create OAuth 2.0 remote entity for Facebook as it is created OOTB
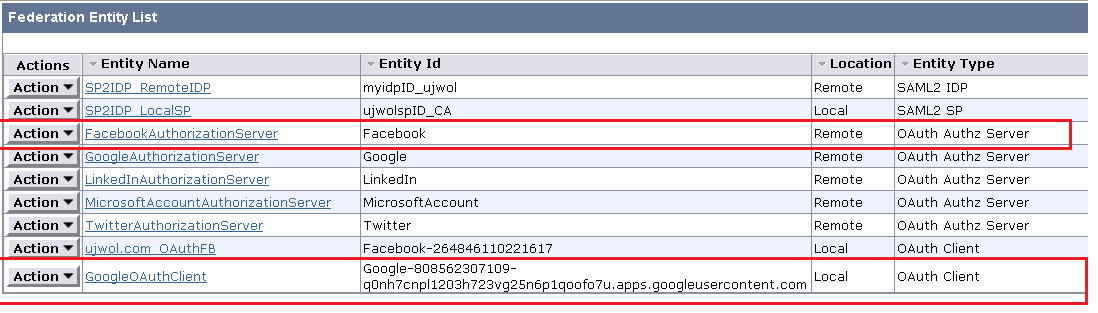
3. Next , proceed to create Partnership > OAuth Client -> OAuthz Server as below :


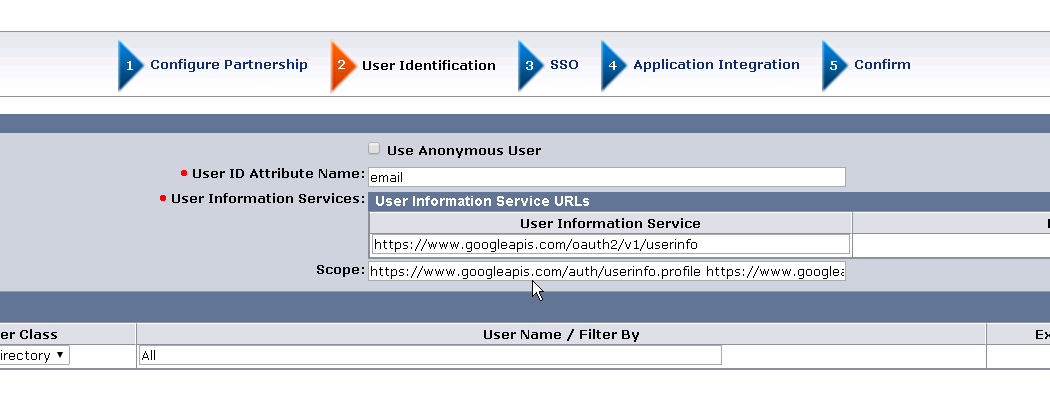
Configure User Identification Attribute:
- User ID Attribute Name – User identifying claim from the OAuth user (e.g. email)
- User Information Service URL – User information URLs that the system must use to retrieve user claims For Google it is : https://www.googleapis.com/oauth2/v1/userinfo
- Scope – Pre-filled as configured in the Remote Entity
- Federated Users– Select users that should be allowed to authorize (e.g. All Users in lcoal SP Directory)
Next,
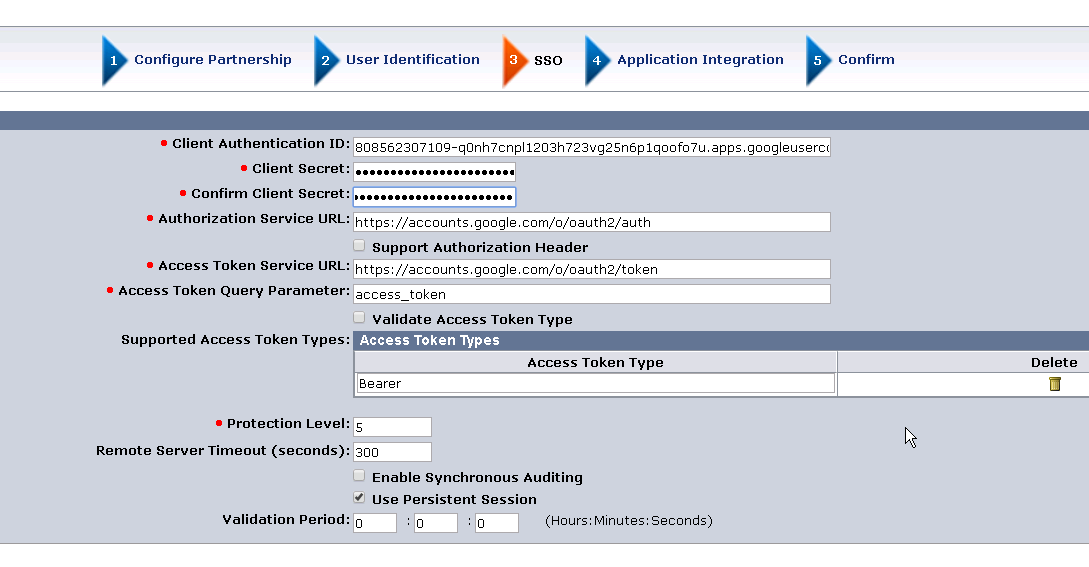
- Client Authentication ID : <OAuth Client ID>
- Client Secret : <Client Secret corresponding to the OAuth Client ID>
Leave the remaining fields to default.

Next,
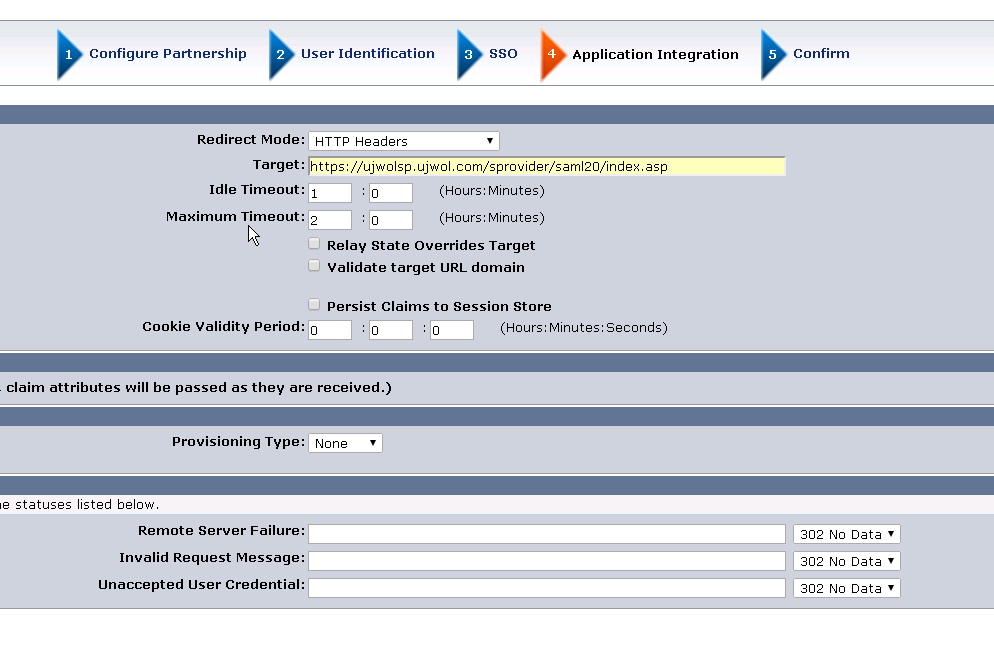
- Redirect Mode : HTTP Headers (or any other preferred mode)
- Target : Target SP URL after authorization.

Configure Domain/User Directory/Policy etc for SP Target URL:
- This step is not detailed here as its basic CA SSO configuration.
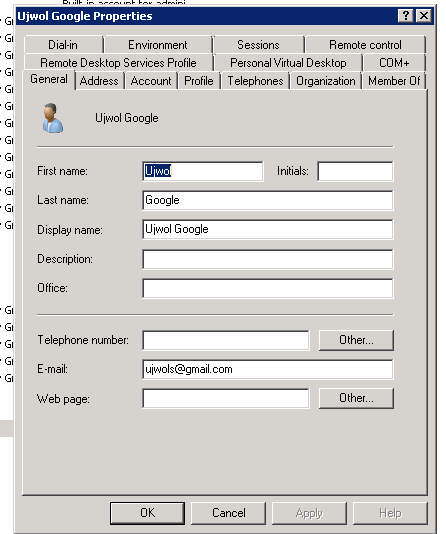
- You also need to ensure that your Federation User Directory have the User with the same attribute (email as per our current configuration )
Federated Social Login Testing (OAuth Client initiated):
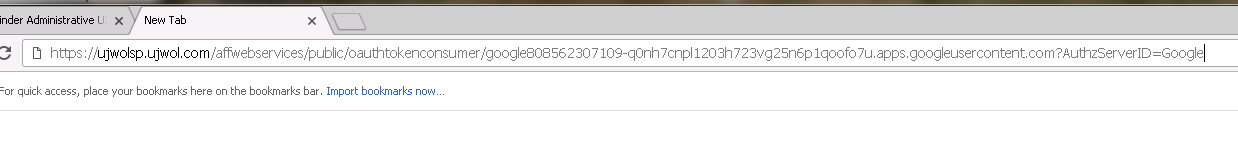
1. Access URL to imitate Oauth 2.0 federation :
https://<FWS_FQDN>/affwebservices/public/oauthtokenconsumer/<DisambiguationID>?AuthzServerID=Google
Where,
FWS_FQDN is the fully-qualified domain name for the host serving SiteMinder Federation Web Services
e.g
https://ujwolsp.ujwol.com/affwebservices/public/oauthtokenconsumer/google808562XXXXX?AuthzServerID=Google

2. If not already logged into Google account , prompted for login. Proceed to login.

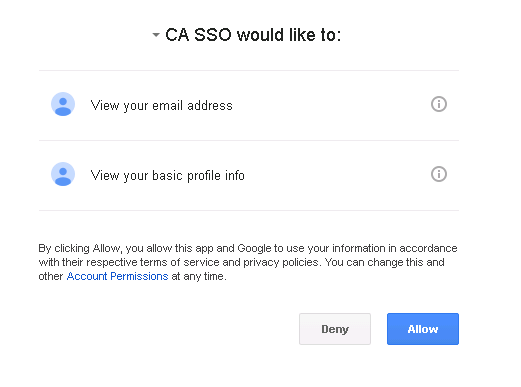
3. Allow the Google App to access profile information from Google (these info will be returned to SP )
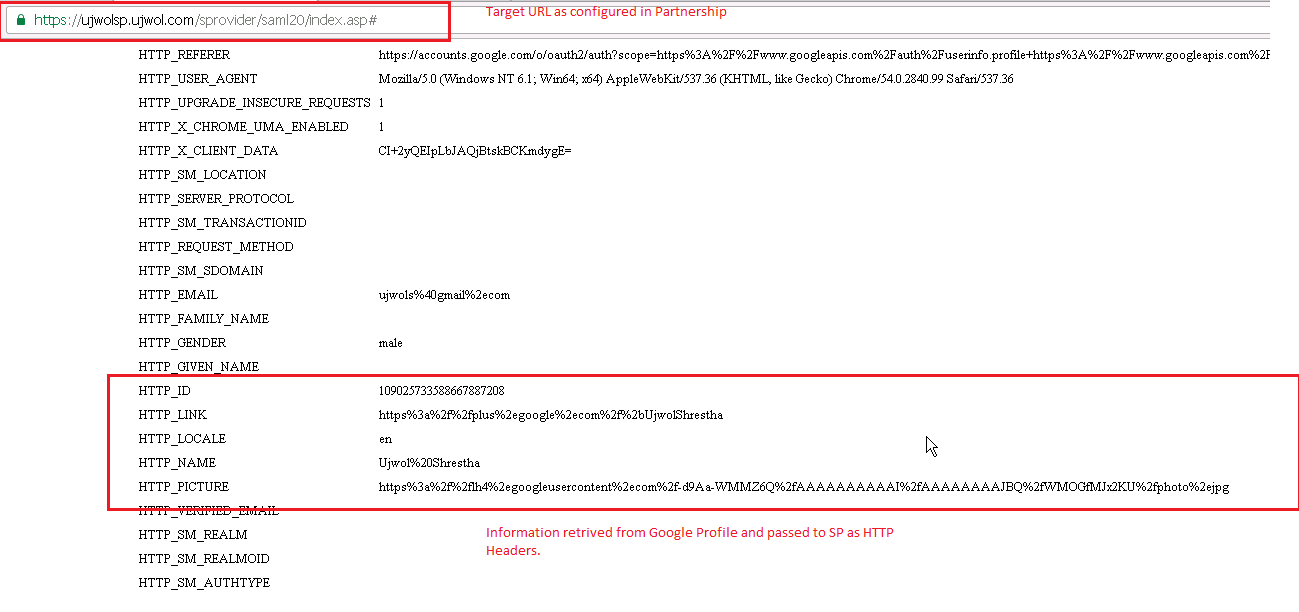
4. Redirect to the Target URL in SP
Additional Information:
CA SiteMinder Social Sign-On Runbook for Google IDP