This is a very broad question to answer , comparison is endless topic. Like any other technology one can make it as simple as it can be or design the more complex solution. NSX-v is certainly great since it is the native SDN platform for vSphere customers and it make more sense to leverage the same with vSphere use cases . There are two main options for ACI based design.
● Option 1. Running NSX-V security and virtual services with a Cisco ACI integrated overlay: In this model, Cisco ACI provides overlay capability and distributed networking, while NSX is used for distributed firewalling and other services, such as load balancing, provided by NSX Edge Services Gateway (ESG).
● Option 2. -Running NSX overlay as an application: In this deployment model, the NSX overlay is used to provide connectivity between vSphere virtual machines, and the Cisco APIC manages the underlying networking, as it does for vMotion, IP Storage, or Fault Tolerance.
You may also go through https://communities.vmware.com/servlet/JiveServlet/previewBody/30849-102-1-41565/Deploying%20NSX%20with%20Cisco%20ACI%20…
Main features of ACI are
● Application-centric network policies
● Data-model-based declarative provisioning
● Application and topology monitoring and troubleshooting
● Third-party integration
◦ Layer 4 through Layer 7 (L4-L7) services
◦ VMware vCenter and vRealize
◦ Microsoft Hyper-V, System Center Virtual Machine Manager (SCVMM), and AzurePack
◦ Open Virtual Switch (OVS) and OpenStack
◦ Kubernetes
● Image management (spine and leaf)
● Cisco ACI inventory and configuration
● Implementation on a distributed framework across a cluster of appliances
● Health scores for critical managed objects (tenants, application profiles, switches, etc.)
● Fault, event, and performance management
KEY BENEFITS of NSX-v
• Micro-segmentation and granular security
delivered to the individual workload
• Reduced network provisioning time from
days to seconds and improved operational
efciency through automation
• Workload mobility independent of
physical network topology within and
across data centers
• Enhanced security and advanced networking
services through an ecosystem of leading
third-party vendors
- . Distributed stateful firewalling, embedded in the hypervisor kernel for up to 20 Gbps of firewall capacity per hypervisor host. Support for Active Directory and activity monitoring. Additionally, NSX Data Center can also provide north-south firewall capability via NSX Edge™.
- NSX Gateway Support for VXLAN to VLAN bridging for seamless
connection to physical workloads. This capability is both
native to NSX Data Center and delivered by top-of-rack
switches from an ecosystem partner.
- NSX Data Center API RESTful API for integration into any cloud management
platform or custom automation
- Operations Native operations capabilities such as central CLI, traceflow,
SPAN, and IPFIX to troubleshoot and proactively monitor
the infrastructure. Integration with tools such as VMware
vRealize® Operations™ and vRealize Log Insight™ for
advanced analytics and troubleshooting.
- Application Rule Manager and Endpoint Monitoring enable
end to end network trafc flow visualization up to Layer 7,
allowing application teams to identify both intra and inter
data center end points, and respond by creating the
appropriate security rules.
- Context-Aware Micro-segmentation
NSX Data Center enables the creation of dynamic security
groups and associated policies to be based on factors
beyond just IP address and MAC, including VMware vCenter®
objects and tags, operating system type, and Layer 7
application information to enable micro-segmentation
based on the context of the application.
- Identity based policy using login information from VMs,
Active Directory, and Mobile Device Management integration
allows for security based on the user including session level
security in remote and virtual desktop environments.
- Cloud Management Native integration with vRealize Automation™ and OpenStack.Third-Party Partner Integration
Support for management, control plane, and data planeintegration with third-party partners in a wide variety of
categories such as next-generation firewall, IDS/IPS,agentless antivirus, application delivery controllers, switching,operations and visibility, advanced security, and more.
Multi-site Networking and Security
- Extend networking and security across data center boundaries irrespective of underlying physical topology—enabling capabilities such as disaster recovery and activeactive
data centers
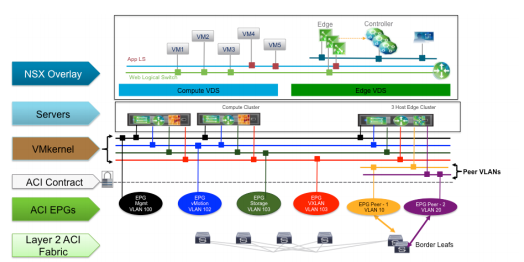
Below picture depicts option-2 kind of deployment were we are leveraging DLR,Edges and segmentation for NSX workloads and having EPG created for management VLANS managed by ACI Fabric. Technically speaking this is a better approach rather having a mix and match of both the platforms here and there.
VMware Knowledge Base (No third party switch integration supported with vSphere)
As far the recommendations are concerned , if your use case is to ease physical fabric day to day operations under a single SDN approach. ACI is a way to go but certainly need ACI supported Switches/Routers . As far as NSX-v there is no hardware compatibility matrix which makes choice easier as long as there is a IP connectivity :smileyhappy: (Exception is hardware gateway Use cases) and doesn't matter underlay is SDN or not.