Several online media sources are reporting about an ongoing ransomware campaign targeting companies in Europe, which involves a new variant of ransomware called as BadRabbit.
BadRabbit !!!
How does it affect us?
A ransomware campaign targeting companies in Europe, which involves a new variant of ransomware.
Dubbed Bad Rabbit, the ransomware first started infecting systems on Tuesday 24 October, 2017.
After witnessing cyber attacks of WannaCry and Petya (aka ExPetr), a new deadly ransomware dubbed Bad Rabbit is on the prowl affecting government, corporate and media houses of Russia, Ukraine, Bulgaria, Germany and some eastern European regions.
Bad Rabbit does not employ any exploits to gain execution or elevation of privilege. The Ukrainian computer emergency agency CERT-UA has issued an alert incident and mentioned that Odessa airport and Kiev subway were also affected. It is unsure whether this alert is regarding Bad Rabbit, but they suspect that it may be the start of a new wave of cyberattacks.
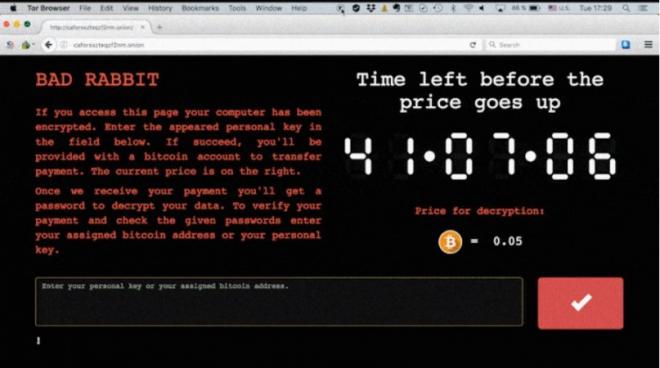
Affected victims are reporting that the Bad Rabbit creators are asking 0.05 Bitcoin (approx. $271/€231/Rs. 17,689) as ransom in return for encrypted PC data.
Symantec is currently investigating the collected samples and ensuring that proper coverage is in place.
Symantec Security Response is indeed aware of this threat (and other developments in the threat landscape.)
Ransom.BadRabbit
https://www.symantec.com/security_response/writeup.jsp?docid=2017-102503-0423-99
BadRabbit: New strain of ransomware hits Russia and Ukraine
https://www.symantec.com/connect/blogs/badrabbit-new-strain-ransomware-hits-russia-and-ukraine
The following articles contains additional good tips:
1) Hardening Your Environment Against Ransomware
https://www.symantec.com/connect/articles/hardening-your-environment-against-ransomware
2) Ransomware removal and protection with Symantec Endpoint Protection
https://support.symantec.com/en_US/article.HOWTO124710.html
The threat belongs to a ransomware family and will encrypt data files and ask users to pay a ransom.
According to initial reports, the malware seems to be a variant similar to Petya.
Security Response is also looking into the distribution mechanisms of this threat, as some reports indicate that this variant might be using the SMB exploit to spread.
It is recommend to block the domain 1dnscontrol[.]com at the corporate firewall.
As ever, ensure that backups against all manner of disasters are in place and that end users are educated in how to react to threats and to emergencies.
Indicators of Compromise (IoC):
URLs:
- 1dnscontrol[.]com/index.php - fake Flash download URI
- 1dnscontrol[.]com/flash_install.php - fake Flash download URI
- 185[.]149[.]120[.]3/scholargoogle/ - URI called out to from watering hole sites
- caforssztxqzf2nm.onion
Watering hole sites:
- Fontanka[.]ru - Referrer to 1dnscontrol[.]com
- Adblibri[.]ro - Referrer to 1dnscontrol[.]com
- Spbvoditel[.]ru - Referrer to 1dnscontrol[.]com
- Grupovo[.]bg - Referrer to 1dnscontrol[.]com
- sinematurk[.]com - Referrer to 1dnscontrol[.]com
- argumenti[.]ru - Referrer to 1dnscontrol[.]com
Hashes
- 630325cac09ac3fab908f903e3b00d0dadd5fdaa0875ed8496fcbb97a558d0da - fake flash installer
- 8ebc97e05c8e1073bda2efb6f4d00ad7e789260afa2c276f0c72740b838a0a93 - C:\Windows\dispci.exe associated with DiskCryptor
- 682ADCB55FE4649F7B22505A54A9DBC454B4090FC2BB84AF7DB5B0908F3B7806 - C:\Windows\cscc.dat (x32 diskcryptor drv) associated with DiskCryptor
- 0b2f863f4119dc88a22cc97c0a136c88a0127cb026751303b045f7322a8972f6 - associated with DiskCryptor
- 579FD8A0385482FB4C789561A30B09F25671E86422F40EF5CCA2036B28F99648 - C:\Windows\infpub.dat [malicious DLL with some similarities to Nyetya]
- 2f8c54f9fa8e47596a3beff0031f85360e56840c77f71c6a573ace6f46412035 - Mimikatz x86
- 301b905eb98d8d6bb559c04bbda26628a942b2c4107c07a02e8f753bdcfe347c - Mimikatz x64
Scheduled Tasks names
Spreading via SMB
Win32/Diskcoder.D has the ability to spread via SMB. As opposed to some public claims, it does notuse the EternalBlue vulnerability like the Win32/Diskcoder.C (Not-Petya) outbreak. First, it scans internal network for open SMB shares. It looks for the following shares:
- admin
- atsvc
- browser
- eventlog
- lsarpc
- netlogon
- ntsvcs
- spoolss
- samr
- srvsvc
- scerpc
- svcctl
- wkssvc
List of compromised sites:
- hxxp://argumentiru[.]com
- hxxp://www.fontanka[.]ru
- hxxp://grupovo[.]bg
- hxxp://www.sinematurk[.]com
- hxxp://www.aica.co[.]jp
- hxxp://spbvoditel[.]ru
- hxxp://argumenti[.]ru
- hxxp://www.mediaport[.]ua
- hxxp://blog.fontanka[.]ru
- hxxp://an-crimea[.]ru
- hxxp://www.t.ks[.]ua
- hxxp://most-dnepr[.]info
- hxxp://osvitaportal.com[.]ua
- hxxp://www.otbrana[.]com
- hxxp://calendar.fontanka[.]ru
- hxxp://www.grupovo[.]bg
- hxxp://www.pensionhotel[.]cz
- hxxp://www.online812[.]ru
- hxxp://www.imer[.]ro
- hxxp://novayagazeta.spb[.]ru
- hxxp://i24.com[.]ua
- hxxp://bg.pensionhotel[.]com
- hxxp://ankerch-crimea[.]ru
Mitigation/Countermeasures
- Block the execution of files c:\windows\infpub.dat and c:\Windows\cscc.dat.
- Secure use of WMI by authorizing WMI users and setting permissions / Disable or limit remote WMI and file sharing.
- Configure access controls, including file, directory, and network share permissions with the principle of least privilege in mind.
- Block remote execution through PSEXEC.
- Enable Anti-ransomware folder protection feature added in Windows 10 v1709 https://blogs.technet.microsoft.com/mmpc/2017/10/23/stopping-ransomware-where-it-counts-protecting-your-data-with-controlled-folder-access/
- Consider deploying Microsoft LAPS [Local Administrator Password Solution] which ensures that each domain-joined host in an organisation has unique Local Administrator credentials, preventing ransomware from using the extracted credentials to spread laterally https://technet.microsoft.com/en-us/mt227395.aspx
- Limit lateral communication with necessary host-based firewall rules.
- Disable SMBv1 and block all versions of SMB at the network boundary by blocking TCP port 445 with related protocols on UDP ports 137-138 and TCP port 139; this applies to all boundary devices.
- Check for unusual scheduled tasks
- Restrict execution of powershell /WSCRIPT in enterprise environment Ensure installation and use of the latest version (currently v5.0) of PowerShell, with enhanced logging enabled. script block logging, and transcription enabled. Send the associated logs to a centralized log repository for monitoring and analysis.
- Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
- Establish a Sender Policy Framework (SPF),Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) for your domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes
- Consider installing Enhanced Mitigation Experience Toolkit, or similar host-level anti-exploitation tools.
- Follow safe practices when browsing the web. Ensure the web browsers are secured enough with appropriate content controls. Consider Click to enable features.
- Network segmentation and segregation into security zones - help protect sensitive information and critical services. Separate administrative network from business processes with physical controls and Virtual Local Area Networks.
- Disable remote Desktop Connections, employ least-privileged accounts.
- Always Update software from the relevant vendor sites.
- Enforce application whitelisting on all endpoint workstations. This will prevent droppers or unauthorized software from gaining execution on endpoints.
What are the details of Symantec's protection?
Symantec has the following protection in place to protect customers against these attacks:
Antivirus
SONAR behavior detection technology
Advanced Machine Learning
Network Protection Products
- Malware Analysis Appliance detects activity associated with BadRabbit
- Customers with Webpulse-enabled products are protected against activity associated with BadRabbit
Data Center Security Products
- Data Center Security Server anti-malware protects customers
- Data Center Security Server Advanced protects against the drive-by-download and Mimikatz