
Symantec has recently seen a spam campaign involving fake wire transfer request emails. While this technique is not new, and has had some coverage in the press this year, we have seen an increase in this type of spam recently.
The purpose of this type of email is very simple—to get the recipient to process a payment for non-existent goods or services by way of a wire or credit transfer. The scammers send an email to a target recipient, usually pretending to be from the CEO or a senior executive of an organization. The scammers will usually send the fake wire transfer emails to employees working in the finance department of a company, as those employees will have the ability to action payment requests.
Another tactic the scammers use is registering domains very similar to the target domain. For example, if a scammer was targeting a user at exampledomain.com, they might register the domain exampledoma1n.com or exaampledomain.com. So for example, you might receive an email sent to you at yourname@exampledomain.com from CEO@exaampledomain.com. The reason for this is that when a recipient replies to the email, the scammer hopes that they might not notice the slight difference in the domain and think it’s from a trusted sender.
During our analysis, we noticed that the scammers are sending the emails out on the same day that they are registering the domains. This is likely in the hope that they can extract payment before the domain is reported and suspended.
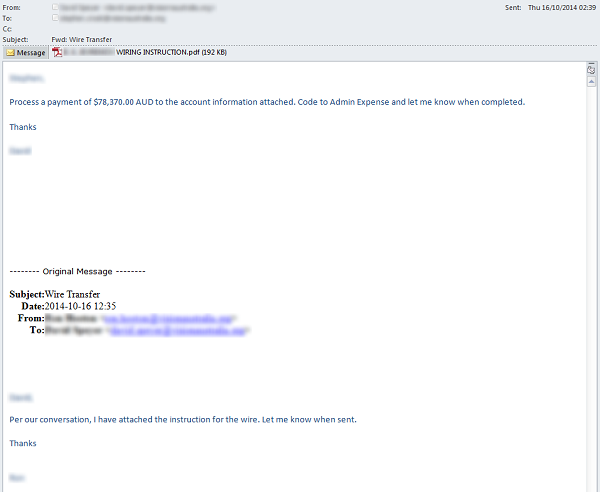
Figure 1. Fake payment request supposedly from a senior executive
Many of the fake wire transfer emails contain a PDF document (see Figure 1) with the credit transfer instructions.
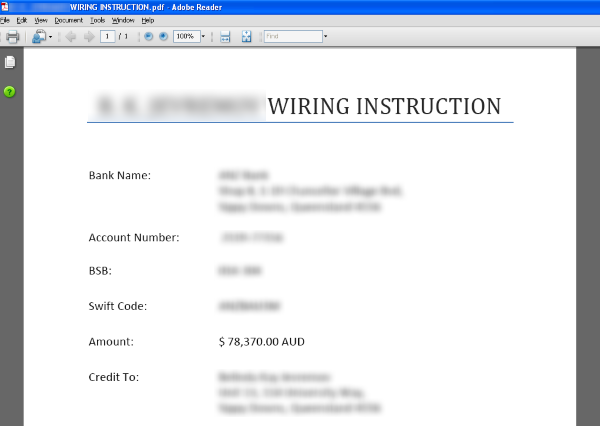
Figure 2. PDF document containing credit transfer instructions
However, we have also seen examples of these scam emails being sent with no attachments and just one line of text (see Figure 3). This version of the scam requires the email recipient to reply to the message; the scammers will then forward on the payment details.

Figure 3. Fake payment request
We have also seen variants where the scammers spoof the “From” address to make it look as though the email is coming from a company executive, even though the true sender’s address is different. The “Reply-To” address, usually a webmail address, can be seen when the user clicks reply.

Figure 4. Email header with spoofed “From” address and webmail “Reply-To” address
If you receive a wire transfer request that seems out of the ordinary, always check that the sender is who they say they are. Ask yourself: is it normal procedure for your CEO to decide that you’re the best (or only) person to help in that situation?
Check the email headers to see where the email has originated from.
If you receive an email with a thread that you’ve supposedly been sent before, check with the person who has supposedly sent the email. Reply to the sender but obtain their email address using your company’s address book in your email client.
If you have any suspicions about an email requesting a wire transfer, investigate it further before proceeding with the request.