Because of increasing number of CryptoLocker-like infections, attacks and fast malware mutations the need to enforce the user application policy in our SEP managed systems became urgent.
Presently, the only secure way against these new, unknown viruses is, to disallow any application to run from User Profile directories, like Local and LocalLow with the help of the Application and Device Control feature. We should keep in mind while constructing our rules, that new generations of these Ransom-ware applications install themselves into many directories apart from Local(Low)/Temp. This is a very strict policy, exceptions are required to ensure user experience.
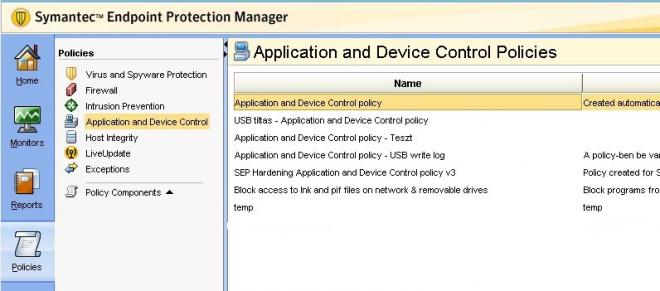
These settings can be achieved in SEP Manager → Policies as follows:


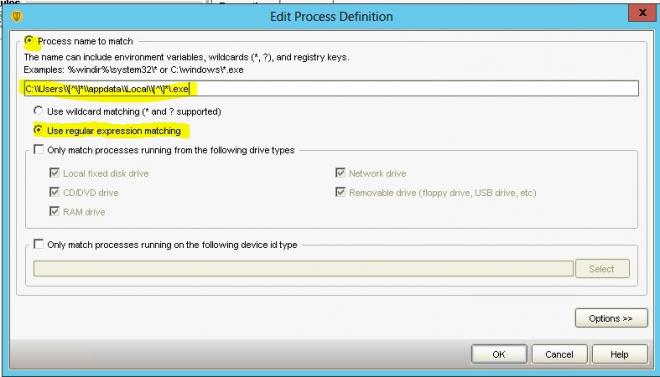
In the blocklist and exception list we can use “regular expressions” to describe rules. With regular expressions we can use wildcards in any part of the paths we supply, simplifying the selection of allowed/blocked directories.
More about this at:
https://support.symantec.com/en_US/article.HOWTO82512.html
The way to add a new block/allow rule:
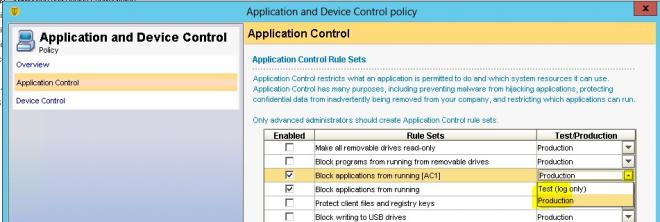
After adding our settings we can specify actions to take on the “Actions” tab. We set up blocking, logging and notifications in mail:

It’s important to run our settings in Testing mode first, and only enable Production mode after tuning our exception lists to prevent undesired behavior.
The rules:
Application and Device Control Policy
Block:
C:\\Users\\[^\]*\\appdata\\[^\]*\\[^\]*\.exe
C:\\Users\\[^\]*\\appdata\\Local\\[^\]*\.exe
C:\\Users\\[^\]*\\appdata\\LocalLow\\[^\]*\.exe
C:\\Users\\[^\]*\\appdata\\Local\\Temp\\[^\]*\.exe
C:\\Users\\[^\]*\\appdata\\LocalLow\\Temp\\[^\]*\.exe
C:\\Users\\[^\]*\\appdata\\Local\\Temp\\[^\]*\\[^\]*\.exe
C:\\Users\\[^\]*\\appdata\\LocalLow\\Temp\\[^\]*\\[^\]*\.exe
Exceptions (example):
C:\\Users\\Administrator\\appdata\\Local\\[^\]*\.exe
C:\\Users\\Administrator\\appdata\\LocalLow\\[^\]*\.exe
C:\\Users\\Administrator\\appdata\\Local\\Temp\\[^\]*\.exe
C:\\Users\\Administrator\\appdata\\LocalLow\\Temp\\[^\]*\.exe
C:\\Users\\Administrator\\appdata\\Local\\Temp\\[^\]*\\[^\]*\.exe
C:\\Users\\Administrator\\appdata\\LocalLow\\Temp\\[^\]*\\[^\]*\.exe
More exceptions (example):
C:\\Users\\[^\]*\\appdata\\Local\\Mozilla Firefox\\firefox\.exe
C:\\Users\\[^\]*\\appdata\\Local\\IE Tab\\[^\]*\\ietabhelper\.exe
C:\\Users\\[^\]*\\appdata\\Local\\Temp\\Foxit Reader Updater\.exe
C:\\Users\\[^\]*\\appdata\\Local\\Google\\Google Talk Plugin\\googletalkplugin\.exe
C:\\Users\\[^\]*\\appdata\\Local\\Google\\Update\\GoogleUpdate\.exe
Create a "Notification condition" under Monitors/Notifications:
