Introduction
This is the nineteenth in my Security Series of Connect articles but the first to reference a sequel starring Billy Crystal, Jack Palance and Jon Lovitz. For more information on how to keep your enterprise environment secure using often-overlooked capabilities of Symantec Endpoint Protection (and the OS upon which it functions), see Mick's Greatest Hits: Index of Helpful Connect Security Articles. This article was last updated in December 2017.
Symantec Security Response and Technical Support are always advising end users, "Be suspicious and think before you click: Never view, open, or execute any email attachment unless you expect it and trust the sender." In What NOT to Click we saw how malicious Office attachments (Word, Excel and so on) would attempt to "social engineer" end users into enabling content and unleashing Macro mayhem on their organization. Office spam is not your attackers' only trick, though. This article illustrates what recent phishing PDFs look like so that you are not bamboozled into giving away your valuables to identity thieves.
Let me show you.... Part 2
All of the screenshots below are from .pdf documents sent out in recent phishing spam campaigns. Stampedes of these mails are whipped up every day by no-good varmints, in hopes that at least a few unsuspecting newcomers will be trampled. The mails have .pdf attachments which open in Acrobat Reader and present some sort of message, often imitating a trusted brand (Including "Norton Secured" logos), designed to hoodwink recipients into clicking on a link. Those links will (usually) open a phishing webpage or (sometimes) download a malicious file.
|
The proper ways to fight phishing are with AntiSpam email security tools and end user education.
(Thus this helpful illustrated article!)
These spammed .pdfs are not malicious code, so AntiVirus is not the right tool to stop them. Symantec classifies these .pdfs as Threat Artifacts.
These phishing .pdfs are no more valuable to virus-wranglers than lead bricks painted gold. Round up and submit any samples that slip through to your AntiSpam vendor. If that vendor is Symantec, instructions are either in:
Spam email missed (False Negative) in Symantec.cloud
http://www.symantec.com/docs/TECH222389
or
Manually submitting missed messages to the Symantec Security Response Center.
http://www.symantec.com/docs/TECH83081
|
Now, dear reader, I humbly ask your kind pardon in advance for all the Wild West terminology....
It's For Your Own Protection Part 2
Just like with malicious macro spam, phishing spam will often pretend that the end user's necessary actions are done in the cause of Security. "Secured PDF Online Document"!
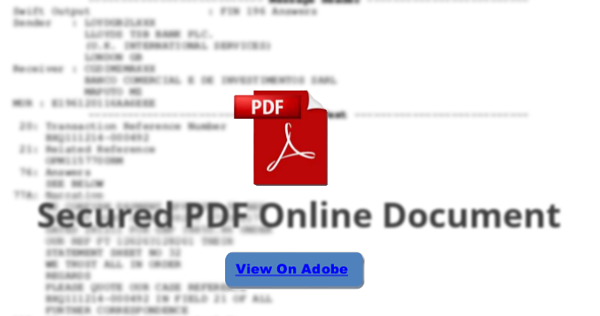
"View On Adobe" - as if that makes any sense. If it sounds like a stranger is trying to hornswoggle you, they probably are.
Here's another very secret and secure example: "This Document is Password Protected"
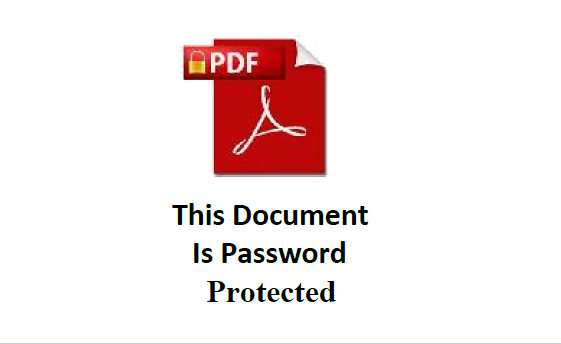
Yessir, I always trust anything that switches font in mid-sentence.
This next phishing lure seems to tell that network security measures are working! "Your system firewall rules have stored files online. Show received doc here."

Now, I am no firewall expert, but... trust me: storing files online ain't what Symantec's firewalls do. If in doubt about how your company's firewalls work, ask the IT security team. Guaranteed, that posse will be glad you did rather than blindly clicking.
Wait Mr. Victim, You're Missing Something Part 2
Oh no! "This pdf version is outdated. Click here to preview online"

No thanks! I'd rather not get bilked out of my riches by some villain.
Packed Full of Goodness! 2
Oh! Excitement! Someone is sending me a package! That's always mighty pleasant.

Too bad there is no www.dhl.cn site. And that page presented when clicking "View File" has a different country's TLD, and looks nothing like a legit DHL site....

Please don't send the scammers a present! Don't give 'em nothing.
Here's a similar phishing lure, but for a document....

Looks official! Why getting a document is dear like a letter from my auntie back East! Better click....
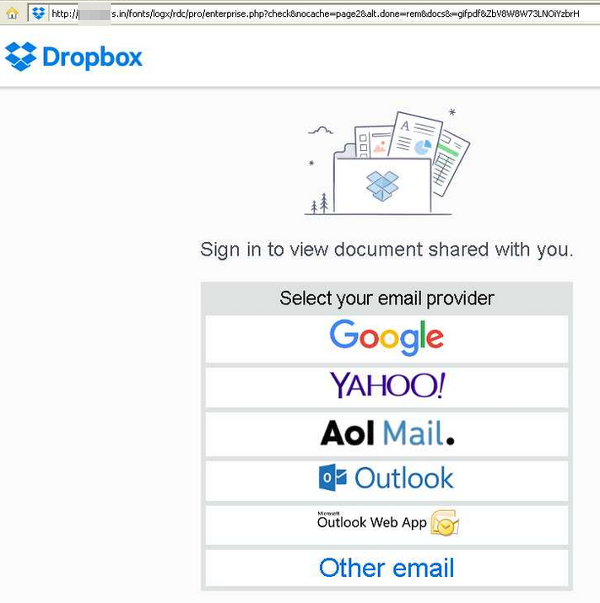
Wait a tick.... how come this URL is some site in India, by hooky, rather than the legitimate https://www.dropbox.com/ ? And how come it looks kinda flim-flam?
This here's from some bunko artist.
Wait, Is That A Real Stagecoach-?
Now a national chain in the US, Wells Fargo is a bank that dates back to the Gold Rush days of the Wild West. Here's a screenshot of some modern-day rustler trying to hijack a greenhorn's claim:

"Dear Valued Customer"? The capitalization, punctuation and spelling mistakes are big smoke signals that something's not right. Stranger yet is that I don't even have one of them WellsaFargo online profiles. Let's click anyway and see where this trail leads us....
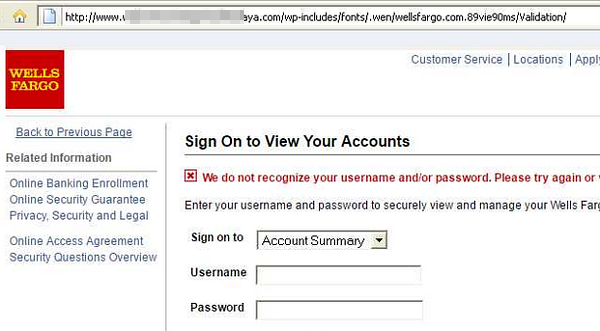
What in tarnation-? This website with the long random domain name is about as legitimate as snake oil.
Sometimes The Creative Juices Just Won't Flow 2: The Legend of Curly's Gold
Here are a couple "Coffee Boiler" phishing lures, plumb-lazy offerings by some skunk who would rather sit around the fire all day than do any work.
This one does not bother with any fancy graphics. "Click HERE to login and unlock file."

For who? Why-? I ain't some dumb dude, no sir.
This next example can't decide it if it is imitating Dropbox or Docusign.
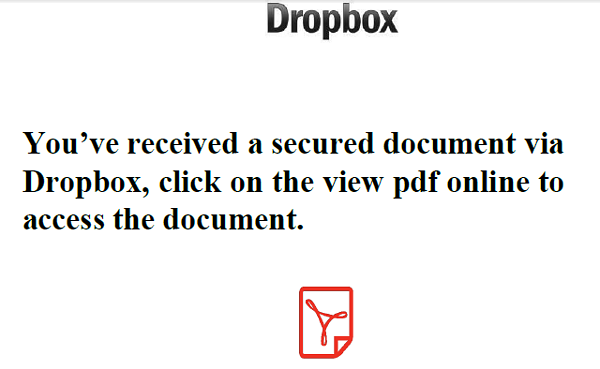
So font and punctuation are not their strong suit. And getting the logo turned the right way around. Maybe the sender of this important document will earn extra credibility bonus points on spelling-?

Nope.
So What Should We Do?
Remember: Curly looked a lot like his twin brother Duke. Phishing mails and webpages might seem at first glance to be the real McCoy, but ease on back in the saddle, pardner, and take a good, slow gander...
- Keep your eyes peeled for pigs in a poke. That is, low quality text, graphics, phrasing... these are sure give-aways.
- Pay close attention to the URLs. Go to the legit site rather than being led up whatever blind trail them outlaws planned.
- Submit the suspicious mail and its phishing attachment to your AntiSpam vendor. They will be able to determine if the attachment is safe or something that will dry gultch ya.
- Unless you are certain it is safe, leave it be! Ride off into the sunset, amigo!
Conclusion
Thanking you kindly for reading! And for cogitating before opening documents or clicking links.
Final word: "When in Doubt, don't click it!"
Please leave your weapons at the saloon door and your comments below.