| Note: The following blog post was migrated from the Elastica/Blue Coat website. It was first published on 3/30/2016. |
Overview:
In this blog post, we discuss the latest ransomware known as Petya. We are not presenting the technical analysis of this ransomware but are focusing on how cybercriminals abuse the function of the Dropbox cloud app to deliver Petya to end-users.
Cybercriminals are increasingly financially motivated, as evidenced by advancements in malware design [1] that serve the purpose of exfiltrating money from end-users by infecting their systems. Ransomware is a class of such malware that renders end-user systems unusable by performing nefarious operations such as encrypting hard disks or locking applications. The basic purpose is to blackmail end users into paying a ransom in exchange for regaining control of their locked data or system. Recent successful blackmail attempts on major hospitals, including Hollywood Presbyterian Medical Center in Los Angeles and several hospitals in Kentucky and Canada, highlight the growing threat.
In the last few years, the world has encountered multiple variants of ransomware such as Winlocker [2], Cryptolocker [3], Cryptowall [4], iLocky [5] and, most recently, Petya [6]. Winlocker simply locks the user’s system whereas Cryptolocker, Cryptowall, iLocky, and Petya encrypt system files or complete hard drives through encrypting the Master Boot Record (MBR), making the documents and data completely inaccessible to the end-users. Once the system is infected, the ransomware displays an end-user message on how to pay the extortion amount using anonymous communication channels such as ToR (Onion routing), etc. The fundamental message is simple and clear ‘Give us the money and get your system back”.
Dropbox Abused to Deliver Petya
Cybercriminals are not exploiting any vulnerabilities in Dropbox to deliver Petya; rather they abuse a commonly used function of Dropbox to deliver Petya ransomware. Last year, we presented a talk at ToorCon security conference in San Diego on the “Dynamics of Cloud Storage Abuse and Exploitation” [7] in which we discussed different techniques that attackers can use to bypass existing security mechanisms in cloud storage apps. In the context of Petya’s delivery via Dropbox, we want to highlight techniques and tactics that made the delivery of Petya successful. Let’s take a look:
- Hosting Malware: There is always an unsettled discussion around detecting malicious files hosted on cloud storage apps. In the cloud, advanced malware often goes undetected. Even if basic malware scanning is provided by a cloud storage provider, it is quite easy for the attackers to bypass deployed malware detection by using advanced obfuscation and compression. A well-structured and obfuscated malware can be easily deployed on the cloud storage app. Dropbox [8] puts the onus on the end-users to properly handle malicious files that make their way into Dropbox. This means hosting malicious files on cloud storage apps is not hard and attackers can find different ways to make that happen.
- Delivering Malware: Generally hosted files are shared through links (URLs) that point to specific files on cloud apps. Users then typically need authentication credentials to download these files. But cloud storage apps also provide the functionality to broadly share the files with everyone on the Internet without authentication. For example, a file stored in a cloud app can be shared through a URL to determine whether the user has to explicitly trigger the download by interacting with the cloud app or the file can be automatically downloaded once the URL is opened in the browser. Most users don't realize that this design makes a substantial difference when malicious files are distributed by attackers to the targeted end-users. In the first case, users can make the determination of whether they need to download the file from the cloud storage app or not, but in the second case they do not have a choice or the interaction is minimal. This functionality of cloud storage apps is abused by attackers. However, the attackers can choose any sharing mechanism they think is suitable to distribute their ransomware.
Consider the example of Dropbox, which implements a binary check to determine whether the file is allowed to be downloaded automatically or not. When a URL such as “https://www.dropbox.com/s/[File token]/[Filename]?dl=0” is clicked by the user, the response is observed in the browser, as shown in Figure 1. The user can either provide the credentials or choose to view the file and download it later. The most important part is that user has to interact with the Dropbox app (GUI operations) in this case.
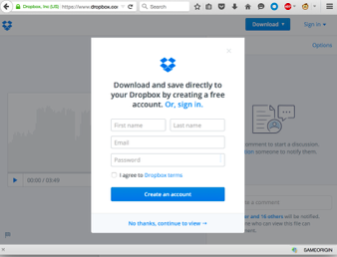
Figure 1: Dropbox App response when “dl=0”
However, if the URL is changed to “https://www.dropbox.com/s/[File token]/[Filename]?dl=1”, The Dropbox downloads the file directly once the URL is clicked and opened in the browser. The user will not be allowed to perform any explicit interaction with the Dropbox GUI; rather the file is directly served by the server in the browser. We want to highlight that different browsers act differently when a shared link is opened. For example- Figure 2 shows how Mozilla serves the file whereas Figure 3 shows that Google Chrome directly downloads the file. Safari exhibits the same behavior as Google Chrome.
.png)
Figure 2: Direct file downloading from Dropbox using Mozilla Browser when “dl=1”
.png)
Figure 3: Direct file downloading from Dropbox using Google Chrome when “dl=1”
The “dl” HTTP parameter is used to provide the download option for how the user wants to share the file. “dl=0” is used to trigger an indirect download whereas “dl=1” is used to trigger a direct download. Most of the malware including Petya is distributed using “dl=0” download options in known instances as it depends on the choice of the attackers.
The attackers can abuse this functionality by forcing users to directly download ransomware automatically with minimum interaction via a URL referring to the malicious file (ransomware) hosted on the Dropbox cloud storage app. The Phishing email can be embedded with the Dropbox URL having a “dl=1” (Direct Download functionality) option so that the ransomware gets automatically downloaded when the user clicks it. On the other side, if the user syncs the file through a client after downloading, it automatically distributes the ransomware to a large set of users. Figure 4 shows how the Phishing email can be constructed to target enterprise users and can set the Dropbox URL with the “dl=1” option for the direct file download.
.png)
Figure 4: Demo Example of Phishing Email used to Spread Malware through Dropbox
This case study simply highlights how existing design capabilities of cloud storage apps can be abused by attackers to deliver malware.
Countermeasures
One of the main concerns is how the ransomware attacks via the cloud can be prevented. The following are some typical countermeasures:
- Gaining granular visibility into the cloud application traffic as well as network traffic. Elastica’s CloudSOC provides complete visibility into cloud application traffic and how users interact with these apps.
- Scanning files sitting in Dropbox via APIs and files shared via Dropbox URLs. Blue Coat advanced malware analysis engine, along with CloudSOC, provides the capability to scan all files in cloud applications and shared via links.
- Detecting if an abnormal number of files are being encrypted.
- In general, ProxySG and advanced malware analysis integration with Elastica’s CloudSOC provides enterprise users with complete visibility and policy enforcement features. Ransomware attacks can be either subverted or impact can be reduced as enterprises attain visibility into both cloudApp and non-CloudApp channels.
References
[1] A. K. Sood, S. Zeadally and R. J. Enbody, "An Empirical Study of HTTP-based Financial Botnets," in IEEE Transactions on Dependable and Secure Computing, vol. 13, no. 2, pp. 236-251, March-April 1 2016.
[2] Dissecting Winlocker – ransomware goes centralized, https://www.virusbulletin.com/virusbulletin/2012/11/dissecting-winlocker-ransomware-goes-centralized
[3] CryptoLocker, Kegotip, Medfos Malware Triple-Threat - See more at: https://www.bluecoat.com/security-blog/2013-10-22/cryptolocker-kegotip-medfos-malware-triple-threat
[4] Cryptowall Demands Cryptocurrency, Abuses Tor, https://www.bluecoat.com/security-blog/2014-06-20/cryptowall-demands-cryptocurrency-abuses-tor
[5] New ‘Locky’ Ransomware Virus Spreading At Alarming Rate: Can The Malware Be Removed And Files Decrypted?
http://www.idigitaltimes.com/new-locky-ransomware-virus-spreading-alarming-rate-can-malware-be-removed-and-files-512956
[6] ‘Petya’ Ransomware Locks Your Computer Screen Then Encrypts Files: How To Remove The File Encrypting Malware, http://www.idigitaltimes.com/petya-ransomware-locks-your-computer-screen-then-encrypts-files-how-remove-file-521931
[7] Dynamics of Cloud Storage Abuse and Exploitation – One More for the Road, http://sandiego.toorcon.net/conference/#10
[8] How does Dropbox handle viruses or malware?, https://www.dropbox.com/help/8406