As threats continue to rise and attackers implement increasingly clever methods for stealing data, you need a trusted security plan for your consumer-facing applications, especially if sensitive information, such as banking, payment, or healthcare data, is involved. Your customers trust you to protect their information which makes it critical to apply strong levels of security to your website and mobile apps.
But how do you implement this type of security so it’s cost-effective, easy to manage and use, and doesn’t negatively affect the customer experience? Symantec™ VIP (Validation and ID Protection) offers exactly that – strong authentication for all your apps on all devices that’s user-friendly, controls costs, and reduces IT complexity. This article describes five steps for building a strong layer of security into your business-to-consumer (B2C) web and mobile apps.
Step 1: Realize the Threats
Threats to your web and mobile applications are real and only relying on passwords is no longer sufficient. Hackers can easily uncover passwords, users forget them, and they often share their passwords with others. In fact, more than a third of U.S. consumers say they’ve given their online banking account passwords to someone else.[1]
Industries that store critical data are more likely to be targeted by cyber thieves so they need to take special precautions to ensure sensitive information is protected. The 2016 Symantec Internet Security Threat Report found that the finance, insurance, and real estate industries are the most highly targeted in spear-phishing attacks with an average of 4.1 attacks per organization (see Figure 1)[2]. In the face of challenges like these, you need secure and simple protection using two-factor authentication (2FA) technology such as Symantec VIP.

1 Figure: Top Industries Targeted in Spear-Phishing Attacks
Step 2: Secure the App
Start by securing the foundation − the app itself. Both web and mobile apps are vulnerable to a host of tactics that attackers employ to steal data including man-in-the-middle attack, account take over, password stolen, reverse engineering, malware, debugging, and more.
By integrating Symantec VIP’s back-end APIs and Credential Development Kit (CDK) into your web and mobile apps, you’ll have built-in security layers while still retaining your brand’s unique look and feel. Symantec VIP gives you the choice of broad authentication options – as easy as a one-tap push or a fingerprint – so you can select the option that works best for your organization and customers.
Step 3: Secure the Mobile Environment
The next step is getting visibility into the device environment and the threats surrounding your app. Symantec VIP invisibly collects anonymous data about threats on the devices where your app is running without compromising your customer’s privacy. Using Symantec VIP’s single console (see Figure 2), you can instantly understand how many of your apps are running on devices that are rooted, jailbroken, or exposed to malware. You can also change an app’s behavior, without redeploying it, by programming contingent actions beforehand and activating them later through a simple console interface.
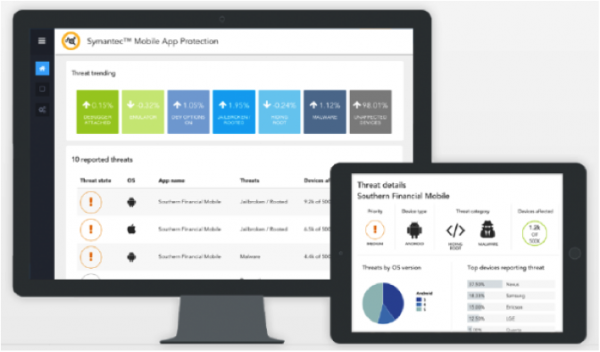
Figure 2: User Symantec VIP's Mobile Apps Risk Detection console to view threat data on devices that are running your mobile apps.
Step 4: Secure the Transaction
High-risk transactions, such as money transfers, stock exchanges, or password resets, can be compromised through account takeovers or man-in-the-middle attacks. These types of attacks are frequent in online activities and can compromise sensitive information and result in financial losses for both your customers and your organization.
It’s critical to secure transactions with Symantec VIP’s risk analysis, which can trigger two-factor authentication based on user, device, and location factors. For instance, if a banking customer lives in California but their mobile device is suddenly located in New York and used to withdraw money, risk analysis can note the change in location and activate two-factor authentication to request additional verification for the transaction.
Step 5: Secure the Data
The final step is protecting valuable information from loss and theft with encryption and data loss prevention. While outside breaches are significant threats, unintentional actions by insiders can also result in sensitive information being shared on unprotected devices and applications. Consider the recent example of an insider breach at the FDIC that resulted in sensitive information for 44,000 individuals being unintentionally copied to a thumb drive by a former employee. In this case, the data was quickly recovered, but other organizations might not be so lucky. This where Symantec Data Loss Prevention, can play a key role in detecting data that’s left (or is in danger of leaving) your organization and Symantec encryption can ensure sensitive data is protected no matter where it’s located.
Next Steps: Secure Your Apps from Threats
Don’t wait until an attack occurs: take the next step and secure your consumer web and mobile applications with Symantec VIP. Get trusted security that your customers will love and that you can be confident will protect your web and mobile apps from threats.
Try Symantec VIP for free in your environment
Learn more about Symantec VIP
[1] Symantec 2016 Internet Security and Threat Report.
[2] Ibid.