|
This is the second article in a three-part series that will examine privacy concerns as they relate to security. The first installment in the series examined hardware-based privacy issues and solutions. This article will discuss software-based issues and solutions. As we shall see, some software is designed to safeguard privacy, while other software seems designed to compromise it.
Personal Firewalls
In the previous article in this series, we covered hardware firewall-routers. Firewalls are an important part of a privacy protection strategy because they prevent intruders from gaining access to valuable information that is stored on a computer. Now let's look at firewalls that run on individual computers. Known as personal, or PC, firewalls, these are different from hardware firewall-routers in several ways. The best PC firewalls track incoming and outgoing traffic, and allow users to set up rules governing what programs on the computer will be allowed to establish connections to the Internet. Best of all, many PC firewalls are free, although even if they are available commercially, prices tend to be reasonable.
There are many different personal firewalls available, for both Windows and Mac OS. Some of the better known ones are:
Before deciding to use any of them, users should research their options. There are several resources available to guide firewall shoppers, including: Home PC Firewall Guide, The GuardianAngel.com Firewall Comparison Chart, and Firewall.net.
Windows XP's Internet Connection Firewall
A brief note of caution for Windows XP users. Now that Microsoft has started bundling its "Internet Connection Firewall" into XP, these users might think that they don't need to look at any of these personal firewalls . However, ICF is not a particularly secure solution, as it only watches inbound connections and ignores outbound traffic. If a bad guy is attempting to scan a computer for vulnerabilities, it should be all right; however, a trojan may be installed - either unintentionally by the legitimate user, or intentionally by a malicious hacker - on that system. If the trojan attempts to phone home, ICF won't notify the user at all. Therefore, it is a good idea to simply turn off Microsoft's firewall and use one of the third-party personal firewalls listed above.
Common Characteristics of PC Firewalls
Certain things are common to nearly all PC firewalls. The fundamental task of all firewalls is to monitor all network traffic entering and leaving the protected computer. If suspicious traffic tries to enter the computer, it will be blocked and the user will be notified, as the following screenshot of ZoneAlarm illustrates:

Figure 1: ZoneAlarm warning that an unauthorized entry was attempted
On the other hand, when a program on the computer tries to send traffic out to the Internet, the user will be asked if he or she wishes to allow it, as demonstrated by Sygate:

Figure 2: Sygate asking if you wish to approve an outgoing connection
All PC firewalls allow the user to deny or approve the outgoing connection, and to make those settings permanent. Notice how Sygate gives details about the program attempting to make the connection, detail that can help the user track down anything suspicious. In fact, further down in Sygate's window a packet dump is displayed:

Figure 3: Sygate's packet dump of an outgoing connection
PC firewalls typically allow the user to set rules governing network traffic. These rules can be set using a simple slider, for basic settings, or the user can specify granular parameters. Below is an example of a simple slider, courtesy of ZoneAlarm, and more advanced choices, taken from Sygate:

Figure 4: ZoneAlarm's basic security settings

Figure 5: Sygate's advanced application configuration
A good PC firewall keeps logs about incoming and outgoing traffic, and allows users to examine those logs to look for patterns that can help them batten down the hatches if needed. Here's an example, as done by Tiny:

Figure 6: Tiny's log file
Linux Personal Firewalls
Linux users have an effective firewall built into their computers. While installing Red Hat, users are asked how they want to configure the firewall. They can configure the firewall further with Lokkit, which is shown below with both the simple and the more specific interface:

Figure 7: Lokkit's basic interface

Figure 8: Lokkit's advanced interface
Be warned, however, that Lokkit is a pretty simple tool. If you need something more complicated on your Linux machine, you might want to look into ipchains and iptables. But no matter what you choose to use, the important thing is that you have a software firewall on your system. Without one, you are inviting potential disaster.
Personal Proxy Software
Even if users have firewalls installed, their privacy is not necessarily secured. While firewalls can keep nosy hackers out of users' systems, the Web-surfing habits of the user can be used to harvest a bounty of personal information. In addition to personal firewalls, users also need to install personal proxy software.
Proxy software examines all the packets coming in to the user's Web browser. As a new Web page is requested, the proxy examines the Web page's HTML, scripts, and graphics. At the same time, it checks the user's preferences so that it knows what he or she wants to view and what should be discarded. For instance, if the user tells the proxy that they don't want to view banner ads, the proxy will filter those ads out.
Some of the most common personal proxies are WebWasher (Windows, Linux, and Mac OS), Junkbusters (Windows and Linux), Guidescope (Windows, Linux, and Solaris), and AdSubtract (Windows). Each of these programs works differently. Some block ads based on the URL, path, or file name, and some base their filtering on dimensions (dimensions are easier to set up, but URLs are more precise). Some proxies have a Web-based interface for configuration, and some require the user to edit text files. Some of these tools provide extensive logging, and others provide just a summary of statistics (see below for an example of WebWasher's statistics). Some software provides advanced debugging tools that can really help the user figure out why something isn't working, and other software provides minimal debugging abilities. Finally, cost is a factor. While most of the proxy software I've mentioned is free, some charge a minimal fee.

Figure 8: WebWasher's statistics
The results of a personal proxy can be seen almost immediately. In particular, Web pages will load more quickly. But a proxy also protects the users privacy in the following ways:
By controlling the use of cookies. A cookie is a small text file that a Web sites store on visitors' hard drives. Cookies store data about the user. They are intended to help the Web site remember information about the user, so that customized information can be presented to them the next time they visit. However, in some cases the data collected by data may be used for less legitimate purposes, such as creating profiles of users for targeted marketing. In some cases, companies sell this personal information for profit without the explicit knowledge or consent of the user.
Whether a cookie is good or bad may be a matter of perspective. For instance, I like getting cookies from The New York Times or Slashdot - they allow me to instantly log-in to www.nytimes.com and get personalized content at Slashdot. However, I don't like that DoubleClick, the giant Internet advertising company, is able to track me on all the sites on which it has placed banner ads. Proxies allow you to customize your cookie settings for each Web site, as I've done with The New York Times and Slashdot. Here is how WebWasher handles such settings:
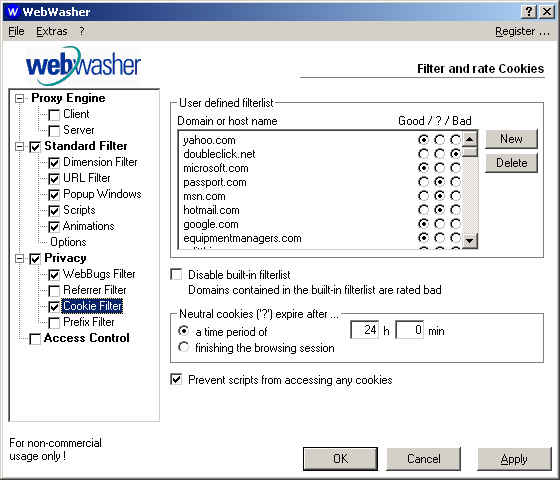
Figure 9: WebWasher's cookie filters
By filtering out advertising. Advertising can compromise privacy because it allows the companies placing the ads to track users' movements across many Web sites. As a person visits each site, the banner ads silently gather information tracking users' trails. By blocking ads, they make it much harder for third parties to compile a record of their interests.
With a proxy, users don't ever need to see another banner ad. However, before filtering out all ads, users might want to consider that many Web sites depend on ads for revenue, so they shoud consider whether or not you want to filter out all ads. Some of the smarter proxies can filter out ads on most Web sites, while allowing ads on sites the user wishes to support.
By blocking pop-up and pop-under windows. This is a blessing now that advertisers have been carpetbombing the Web with pop-under ads. Now I never see them (note that users can also block these ads if they're using the Mozilla Web browser: go to Edit > Preferences > Advanced > Scripts & Windows, and uncheck the first four checkboxes. For users of the Konqueror Web browser - open Setting > Configure Konqueror > Konqueror Browser > JavaScript, and set your "JavaScript web popups policy" accordingly).
This can be a problem, however, on some sites such as Yahoo Mail, which uses a pop-up window for adding attachments to your e-mail, and Windows Update, which opens a popup window while it's checking your computer. Users will need to configure the proxy to ignore those Web sites that use pop-up windows they need.
By hiding the previous Web page visited. Every time Internet users go from one Web page to another, the browser informs the new page of the previous page visited. This is required on some sites, especially search engines. By knowing where people have come from, a Web site can further target those other sites that consistently send it traffic. However, this information may also be used to compile profiles of users' browsing habits, data that can then be used for targetted marketing. Because of this, some people find referer information to be too revealing. Proxy software can help them hide their tracks.
By squishing "Web bugs". Web bugs - also known as "clear GIFs", "1-by-1 GIFs", and "invisible GIFs" - are tiny graphics placed inside Web pages or e-mail messages in order to track information about the user. Many companies, like WebTrends Live, use Web bugs for their log analysis programs. However, some companies use Web bugs to track whether or not user have read an email or even forwarded it. Proxy software can remove Web bugs so that companies can no longer track the user without his or her knowledge.
A personal proxy can really help protect your privacy. After the proxy has been installed, you may want to make sure it's working. WebWasher has a test page available. Or, Steve Gibson's GRC Web site has a fascinating Web page that can be used to test a proxy's effectiveness. Just go to these pages and follow the instructions.
Spyware
Once they've got a PC firewall and personal proxy installed, users will have much greater control over their privacy. However, their computers may already be running software that is revealing sensitive information about them ... and users may not even be aware that this software is running on their machine!
Software that works without the user's knowledge, or that obfuscates what it is doing, is known as "spyware", or "sneakware". Most of the time spyware gets onto a computer by piggybacking along with a program that was intentionally installed. For instance, Audio Galaxy is a popular filesharing program. In January of this year it was revealed that Audio Galaxy also installed the "VX2" program onto users' computers. VX2 tracks the Web sites that users visit and reports that information back to the company, which adds it to a database tracking each user. Worse yet, VX2 collects information from the on-line forms that users fill out. VX2 promises that it won't collect anything sensitive - like credit card numbers or passwords - but the only contact information available for the company is a Hotmail address and a PO box in Las Vegas. Does that make you feel safe? (Removal instructions for VX2 can be found at Counterexploitation)
On April 1, CNET reported that Kazaa, an incredibly popular filesharing program, had bundled software from Brilliant Digital Entertainment for several months. In fact, users could not install Kazaa without agreeing to also install Brilliant's software.
Brilliant revealed in a federal securities filing that its software was designed to link all the computers who had installed it into a new network called Altnet. Computers on this network would receive advertising, music, and other content from Brilliant's partners. In addition, Brilliant would make use of members' computers in order to run programs in a distributed computing system.
Kazaa and Brilliant argued that all the details were made available to users before they installed the programs, in a "terms of service" contract that users are required to read and agree to. This contract, however, is 2,644 words, and analysis has shown that it is written in an extremely confusing, complex manner. Most people simply click "I Agree" and don't read the terms.
(The controversy continues. Brilliant's CEO has tried to justify his company's actions. CNET published instructions detailing how to uninstall Brilliant's software. And in the latest turn, a new program called "Kazaa Lite" that provides access to Kazaa's filesharing network without having to install Brilliant's software has been developed by a Russian programmer known as "Yuri".)
There are Web sites that can help in the fight against spyware: Spychecker, Thiefware, and the colorfully-named Scumware are just a few.
Ad-Aware
Most spyware problems occur on Windows, but it is also an issue on Macs. However, Windows is the main battleground, and it's not surprising; after all, Windows is on at least 85% of the world's personal computers, so it's the main target for the unscrupulous providers of spyware. Fortunately, there's free software available for Windows that will check for spyware, and remove any that it finds: Ad-aware.

Figure 11: Ad-aware's main screen
After Ad-aware finishes scanning the computer, it lists any spyware it finds. Users can check the boxes next to the spyware they would like to remove, click "Continue", and they're done.

Figure twelve: Ad-aware's list of detected spyware
One note of caution: some programs may cease functioning if their spyware is removed. In this case, users simply need to click the "Backup" button in Ad-aware before removing the spyware. If the software no longer works after the removal of the spyware, it can easily be restored. Of course, a better long-term solution might be to look for different software that doesn't act as spyware.
Users who download and install a lot of software should run Ad-aware every couple of weeks. Otherwise, every month or so would probably be fine.
Update the OS and Software
New spyware comes out all the time, so Ad-aware constantly updates its database. If you want Ad-aware to be as effective as possible, download new versions regularly from Lavasoft.
This is true for pretty much all software. If you want to secure your privacy, you need to keep your software up to date. First, new vulnerabilities are discovered in software constantly, and they could compromise your privacy. Second, software like ZoneAlarm and Ad-aware is constantly being improved, and you need to keep up with those improvements.
Updating Macs
For users who are running Macs, Apple makes updating its system software easy. Users running OS X simply need to open System Preferences in the Apple menu and select "Software Update". They can then connect to Apple's servers, check to see if there are any updates, and then make their choices. Minutes later, the process is finished.

Figure 13: Apple's software Update
Windows Update
Microsoft's Windows Update has been available ever since Windows 98. To use it, users just need to open Internet Explorer (they must use IE - Windows Update requires technologies built into IE, so it won't work with Netscape), go to the "Tools" menu, and choose "Windows Update". After the page finishes loading, they can choose "Product Updates", make their choices, click "Download", and Windows Update will download and install everything. It's pretty painless. Unfortunately, Microsoft doesn't give users a lot of information about exactly what it's doing to their system, but Windows Update is still required for Microsoft operating systems. Users need to read the updates and ensure that they actually need them before downloading.

Figure 14: Microsoft's Windows Update
Linux and Red Carpet
People who use Linux have a wealth of options available to them. One of the best reasons to install Ximian GNOME, which runs on a variety of Linux distributions, is Red Carpet. Red Carpet is like Windows Update, but it gives the user far more information. For each item that can be downloaded, Red Carpet displays the currently installed version number, the requested version number, a summary, a full description, required files, and provided files. It will also resolve dependencies, and inform the user if there are any key updates needed for security purposes.

Figure 15: Ximian's Red Carpet, showing details about Junkbuster
Red Carpet is not the only option for Linux users, but it is the slickest. Other well-known possibilities include the Red Hat Network and Debian's apt-get (now ported to work with Red Hat). All are worth investigating, as all will help users keep their system protected against software vulnerabilities.
Updating User Knowledge
Keeping software up-to-date is vital, but it's even more important that users keep their knowledge up-to-date. New software threats are surfacing all the time, and it is vital that privacy-concerned users keep abreast of such developments. Privacy Web sites such as the Electronic Frontier Foundation, the Electronic Privacy Information Center (EPIC) and Privacy.org article are invaluable, as are the news sites mentioned in this article. Unfortunately, securing your privacy can feel like a full-time job; fortunately, all of us working together can help make a difference.
Scott Granneman is a senior consultant for Bryan Consulting Inc. in St. Louis. He specializes in Internet Services and developing Web applications for corporate, educational, and institutional clients.
|