
Last week, Symantec became aware of online reports of new crypto ransomware known as ‘Locker’ (Trojan.Cryptolocker.V), which supposedly laid dormant on infected computers until May 25 at midnight, local time. Once activated, the crypto ransomware proceeded to encrypt files on the compromised computer and hold them to ransom. Symantec and Norton customers are unlikely to have been affected by this new threat, as detections were already in place for the samples reportedly used in this attack.
In a bizarre twist, the alleged author of the malware, going by the name of ‘Poka Brightminds,’ posted an apology on Pastebin on May 30 for unleashing the threat. According to the statement, the malware author never meant to release the Locker malware and in a gesture of repentance, provided access to a database containing the decryption keys along with a declaration that the automatic decryption of files would start on the June 2 at midnight, local time. Now, according to reports on Bleepingcomputer.com, some infected computers’ files are being automatically decrypted, just as the author had promised.
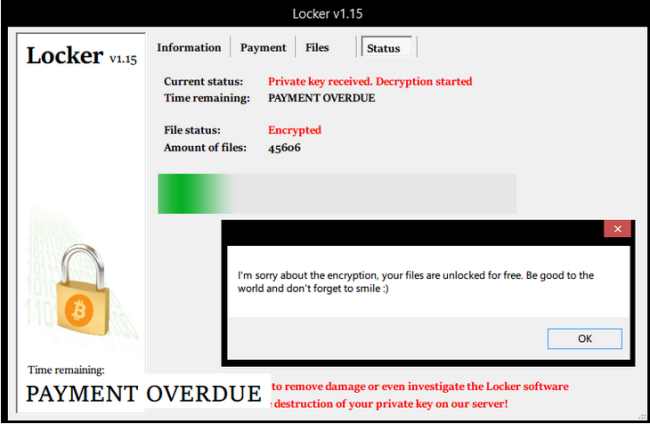
Figure. Locker’s decryption screen message (Source: Bleepingcomputer.com)
Earnings
The database provided by the malware author also contained 62,703 entries related to Bitcoin addresses. Each Bitcoin address was linked to a decryption key and was supposed to be used for the payment of the ransom. Several Bitcoin addresses that were known to have been used in Locker’s ransom demands were confirmed to be in the provided database. After checking the publicly available transactions for each Bitcoin address in the database, we were able to determine that the malware author made US$169 through 22 ransom payments.
Table. Locker’s author received 22 ransom payments amounting to $169
Why repent?
The malware author must have put a considerable amount of time and work into writing the crypto ransomware, setting up the command-and-control infrastructure, and distributing the malware—so why the sudden change of heart? While we do not know for sure why the author tried to make amends, we can offer some hypothetical reasons:
- Someone caught the malware author and threatened to reveal their identity or report them to the authorities.
- Given the reported low earnings of this crypto ransomware, the malware author realized that the risk versus the penalties of getting caught was not worth it.
- The command-and-control infrastructure for the crypto ransomware was compromised and the malware author lost control of the threat.
- The malware author actually regretted their actions. Crypto ransomware malware authors have been known in the past to have a conscience, as we highlighted in an earlier blog: ‘OMG a Ransomcrypt Trojan with a Conscience!’
Damage done
Although the crypto ransomware author now looks to have repented and is trying to make amends, they still broke the law and caused their victims countless worries, time, and money trying to rectify the damage. Also, the victims who have already made efforts to clean up their computer may not be in a position for the malware author to unlock their encrypted files anymore, causing further problems. While the malware author claims that they are sorry for the trouble, I don’t believe that the victims will accept this apology.
Symantec and Norton customers are protected against this threat through our Trojan.Cryptolocker.V detection. Please visit our Ransomware: How to stay safe blog for more information on how to stay safe from the dangers of crypto ransomware.