The information in this article is provided for historical reference only. For all the current Best Practice information, see the following article:
153530 - Best Practices: Symantec Endpoint Encryption and Symantec Drive Encryption
The Recovery Process Steps Summary:
It is recommended that the following actions take place in the order listed for the best possible chance at recovering data.
1. Contact your internal help desk for assistance.
2. Contact Symantec Technical Support for assistance.
3. Run "Recover /a".
4. Run the SEE Hard Disk Access utility and back up any data.
5. Perform a Hard Drive consistency check.
6. Perform a hard drive backup using a "sector by sector" copy method.
7. Run "Recover /d" emergency decryption.
Contacting internal help desk (Step 1)
Contact your internal help desk for assistance
Contacting Symantec (Step 2)
Contact Symantec Technical Support for assistance.
Run "Recover /a" (Step 3)
The recommended first step, after contacting your internal company help desk and the Symantec technical support team, will be to attempt to repair the SEE Hard Disk Operating System (RTOS) if it has been damaged. The use of the recover utility with the /a parameter will not harm the drive or any data it contains.
The command to run this utility is: "recover /a"
WARNING: Do not run the recover program with the "/d" or "/b" parameters until instructed to do so, or there could be the risk of data loss.
Endpoint Encryption Hard Disk Access Utility (Step 4)
Symantec recommends running the Hard Disk Access Utility and attempting to back up the data to a secondary location for safe keeping.
- Boot the system with SEE-FD-Access-7.X.X.iso
(The SEE-FD Access Utility is available on request from Symantec Support)


- MS DOS commands like copy and xcopy can then be used to backup data to a network share (by mapping a drive using
the NET USE command) or to a USB storage device. This allows data to be backed up and retrieved in case a user experiences
a failure within Windows.

Hard Drive Consistency Check (Step 5)
Using the hard drive manufacturer's recommended method, perform a low-level consistency check to verify that the hard drive hardware is operating normally. This is to eliminate the possibility that a mechanical failure is the root cause of the problem. This will usually require a separate boot disk with the manufacturer's utility on it.
Hard Drive Backup (Step 6)
At this point, a backup of the hard drive should be taken for protection against possible data corruption. Further attempts at recovering data will involve writing to the drive and will increase the risk of data loss. Symantec recommends that Symantec Ghost be used to create a "sector-by-sector" copy of the hard drive.
Symantec Technical Support can provide instructions on performing a sector-by-sector backup of the hard drive.
Run "Recover /d" (Step 7 - Emergency decryption)
The emergency decryption process is used to decrypt a hard drive in the event that normal decryption methods are unsuccessful. The emergency decryption utility is a very powerful tool that will decrypt the entire hard drive when authorized by a Hard Disk administrator. There are some very important points to keep in mind when using this utility:
- Never stop the emergency decryption process while in progress!
- Do not run the "recover /d" command more than once, even if it did not appear to work.
- Be patient! The program may appear to be working slowly or not at all at certain points, but the program is most likely still running.
Warning!
- Do not run either of Recover /D OR /B more than once – it will cause file corruption on the hard drive (making any data unrecoverable).
- If Recover /D starts, but does not complete, do not run /B. Recover /B is a variation of /D, not a next step.
Recover /B also performs an identical emergency decryption of a system, but it can do so when the Workstation Encryption Key is not available on the disk by using a backup file extracted from the server.





- This is the Admin credentials for SEE package not system Admin credentials.




- The system is now ready to boot up in normal mode.
References
Best Practices for Data Recovery using Symantec Endpoint Encryption - Full Disk (SEE-FD)
http://service1.symantec.com/support/ent-security.nsf/docid/2008022909242448
Original Message:
Sent: 11-23-2021 05:47 AM
From: Scott Button
Subject: Endpoint Encryption - No recovery method configured on your account
Hi,
I am not sure if I have the right product page for this post. APologies if it is not.
I have a laptop on SEE 11.3.0. Laptop works fine; I can log in succesfully, I can check in to the server and register new users to the disk.
However when I try to press f4 it tells me this:
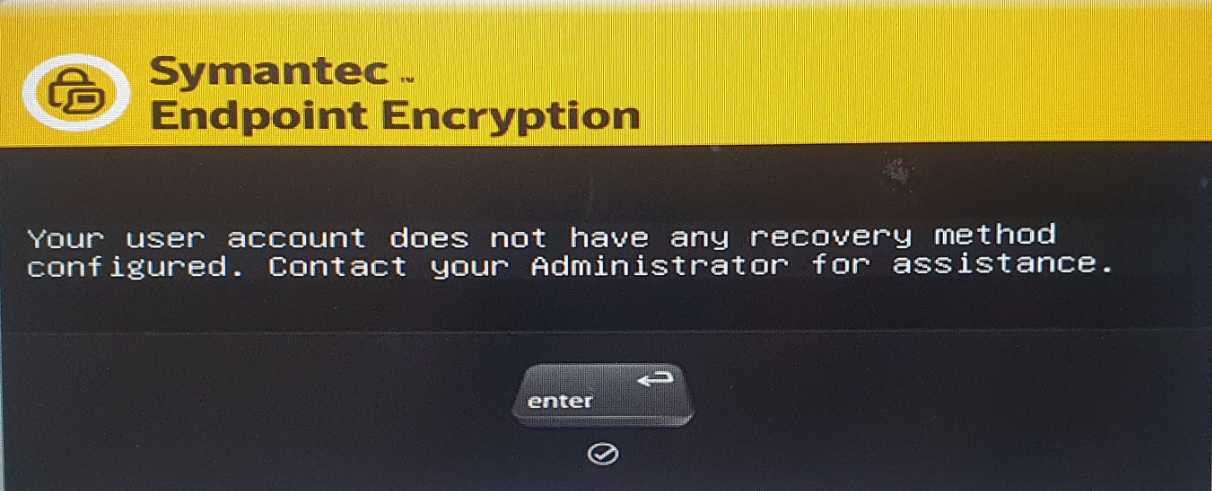
I cant for the life of me work out how to add these also which account is it referring to as this is before I actually try to log onto the system.
I have been googling the s**t out of this and haven't found anything helpful so have resorted to a forum post.
I hope there is someone who can help me with this issue. How do I add a recovery method ?
When I try a help desk recovery on this laptop it tells me this:
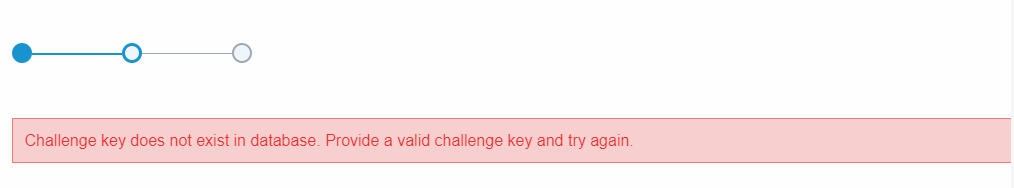
My colleagues all say I should just decrypt and re-encrypt, however this seems a bit extreme like using a shotgun to swat a fly.
Looking for a solution with a bit more finesse hopefully.
If not I'll go decrypting again.
Thank you