Posted by Ujwol Shrestha - Principal Support Engineer in CA Security on Feb 28, 2016
Problem Summary
Impersonation provides a method for a privileged user to:
- Assume the role of another user without ending the session of the privileged user.
- Temporarily assume the identity of another user.
Impersonation does not require users to disclose passwords for one user to impersonate another.
In this article we will discuss in detail how to configure impersonation in CA Single Sign-On r12.5x.
Configuration Overview
This section discusses the overall configuration process to configure Impersonation feature in CA Single Sign-On r12.5x
1. SiteMinder Policy Configuration.
a. Create Impersonation Authentication Scheme
b. Create Impersonator Domain with two realms:
Realm 1 : impersonator
Authentication Scheme : HTML (Or any other authentication scheme)
Protects : /impersonator/
Rule 1 : GetPost-Impersonator
Resource = *
Action = Get, POST
Realm 3 : startImpersonation
Authentication Scheme : Impersonation
Protects : /startimpersonation/
Rule 1 : GetPost-startImpersonation
Resource = *
Action = Get, POST
Rule 2 : ImpersonateStart
Resource = *
Action = ImpersonateStart
Rule 3 : ImpersonateStartUser
Resource = *
Action = ImpersonateStartUser
Realm 3 : impersonatee
Authentication Scheme : HTML (Or any other authentication scheme)
Protects : /impersonatee/
Rule 1 : GetPost-Impersonatee
Resource = *
Action = Get, POST
Rule 2 : ImpersonateStart
Resource = *
Action = ImpersonateStart
Rule 3 : ImpersonateStartUser
Resource = *
Action = ImpersonateStartUser
c. Create Policies for Impersonation:
Policy 1 : Impersonators
Users : Help-Desk
Rule 1 : GetPost-Impersonator from impersonator realm
Rule 2 : ImpersonateStart from impersonatee realm
Rule 3 : ImpersonateStart from startImpersonation realm
Policy 2 : StartImpersonation
Users : Customers
Rule 1 : GetPost-startImpersonation from startImpersonation realm
Rule 2 : ImpersonateStartUser from startImpersonation realm
Policy 3 : Impersonatees
Users : Customers
Rule 1 : GetPost-Impersonatee from impersonatee realm
Rule 2 : ImpersonateStartUser from impersonatee realm
d. Protect startimp.fcc by setting the OverrideIgnoreExtFilter ACO parameter to startimp.fcc as below :
OverrideIgnoreExtFilter=/impersonator/startimp.fcc
e. Disable FCCOMPATMode by setting FCCCompatMode ACO parameter to No :
FCCCompatMode = No
2. Create files required for Impersonation
- Create FCC file to start Impersonation - startimp.fcc
Place this file under /impersonator/ directory
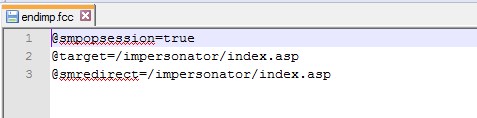
- Create FCC file to end Impersonation - endimp.fcc
Place this file under /impersonatee/ directory
Testing
- Access /impersonator/index.asp and login with Help Desk Administrator (Impersonator) Credential.
- Click link - "Start Impersonation". This opens Url : /impersonator/startimp.fcc
- Impersonator is now prompted to enter the user ID of the person to be impersonated (impersonatee). Enter the Impersonatee User ID and click button - "Impersonate"
- Impersonation now completes and the impersonator is redirected to the success.asp page from startimpersonation realm as impersonatee user.
- From here on, the impersonator can access resource from impersonatee realm by clicking button
- To end impersonation, click link -" End Impersonation". This will open Url : /impersonatee/endimp.fcc.
- Impersonation now ends and the user is redirected to the target configured in endimp.fcc which is /impersonator/index.asp.
Screenshots - Configuration
Fig 0 : Impersonation Authentication Scheme

Fig 1 : Impersonation Domain
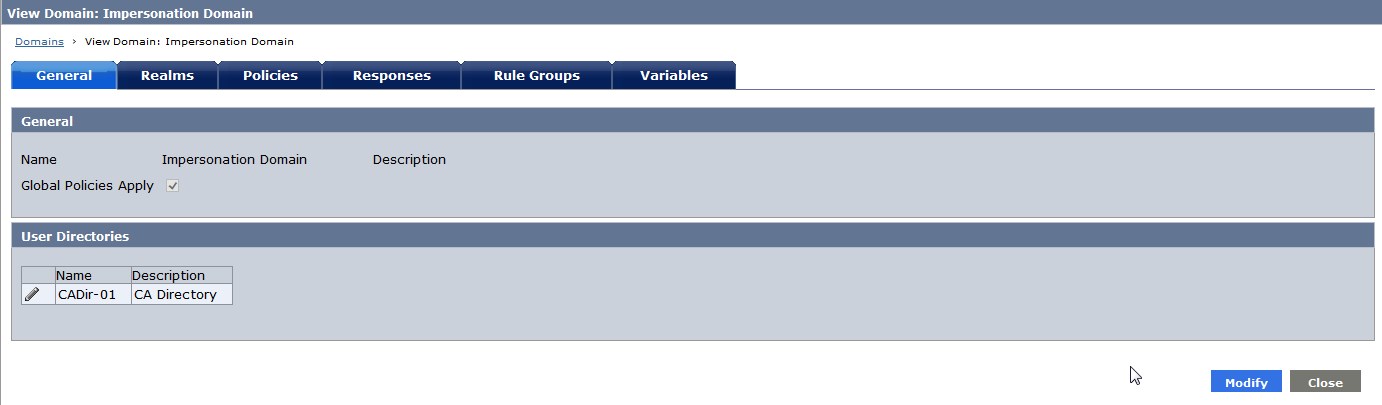
Fig 2 : Realms

Fig 3 : Impersonator Realm

Fig 4 : GetPost-Impersonator Rule
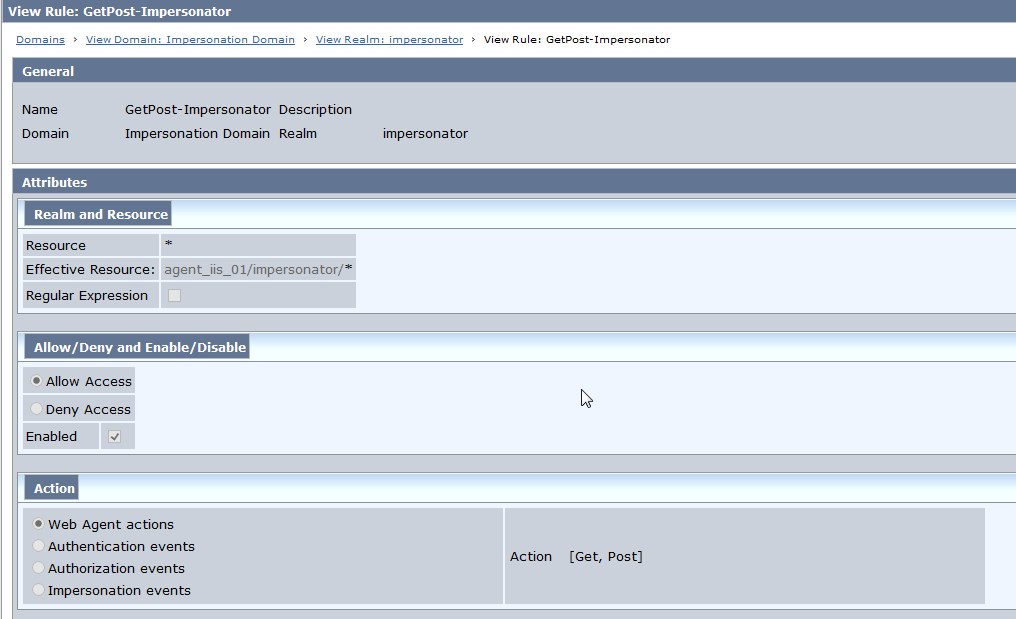
Fig 5 : Impersonatee Realm

Fig 6 : GetPost-Impersonatee Rule
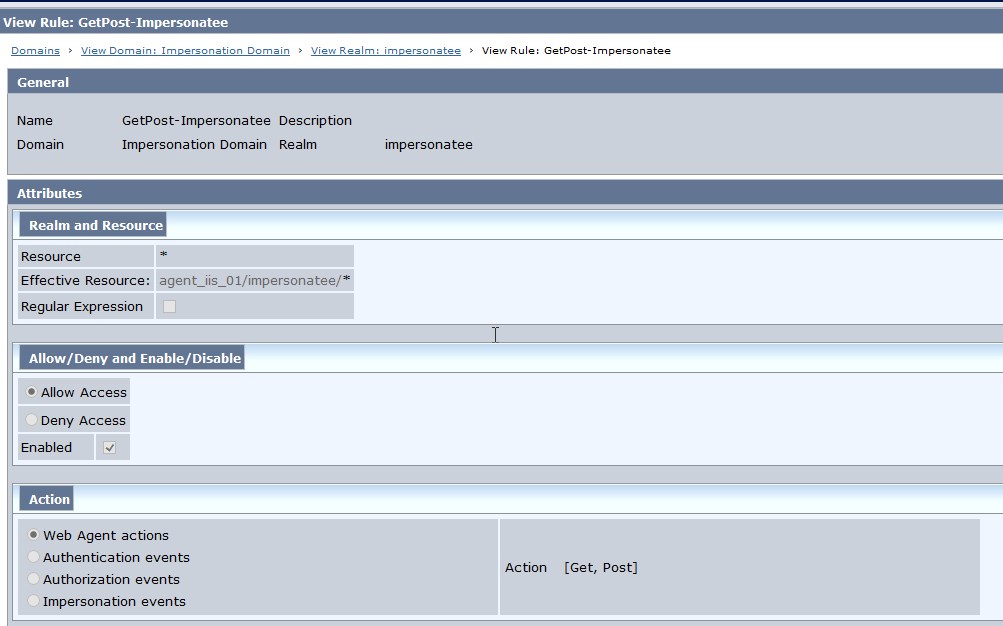
Fig 7 : ImpersonationStartUser Rule
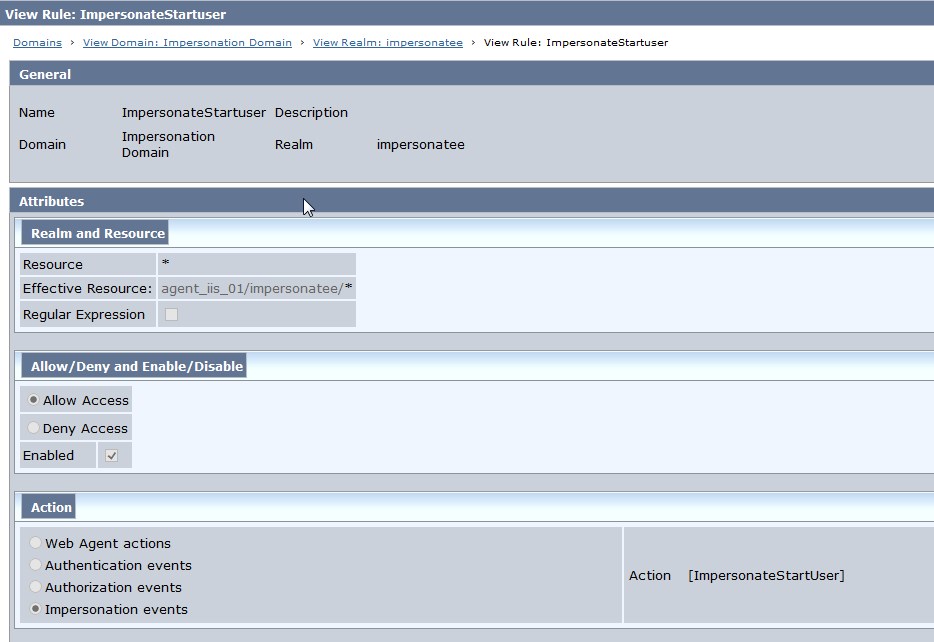
Fig 8 : ImpersonationStart Rule
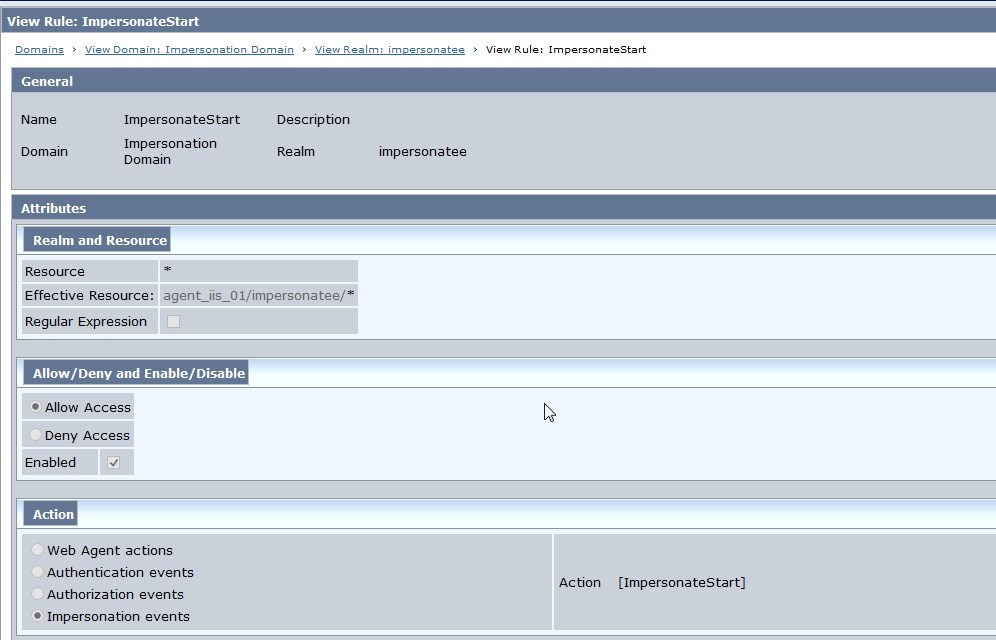
Fig 9 : startImpersonation Realm
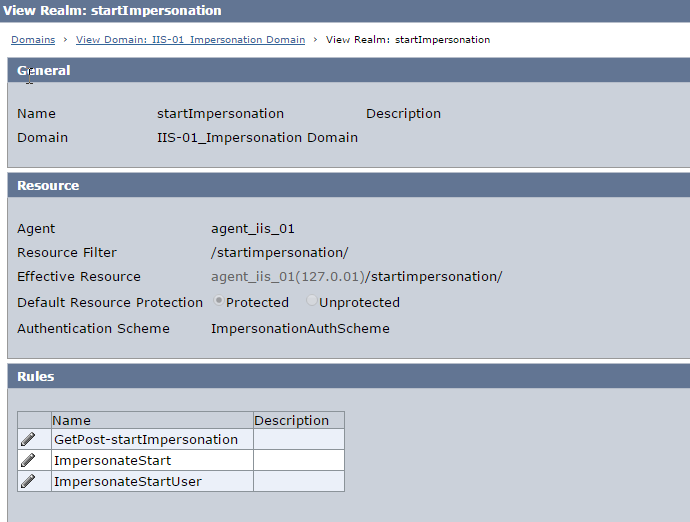
Fig 10 : GetPost-startImpersonation Realm

Fig 11 : ImpersonateStart -startImpersonation Realm
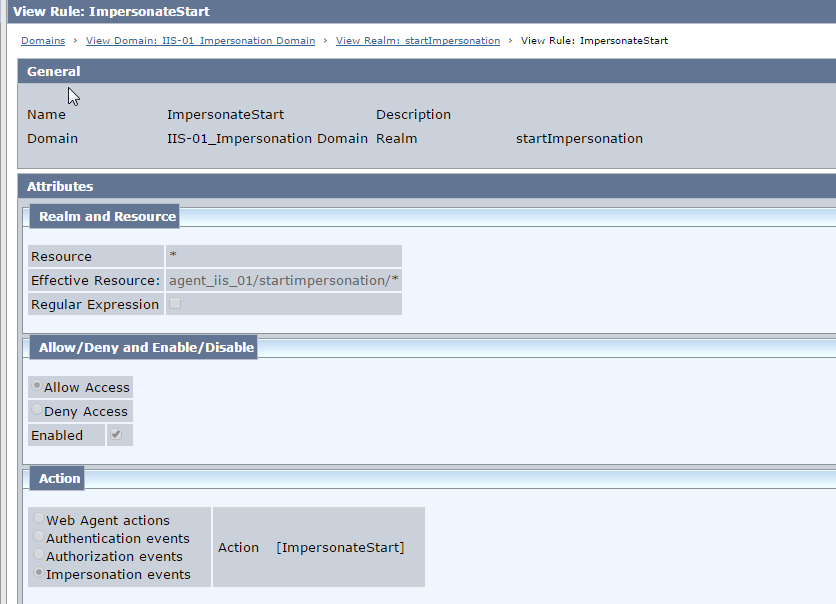
Fig 12 : ImpersonateStartUser -startImpersonation Realm
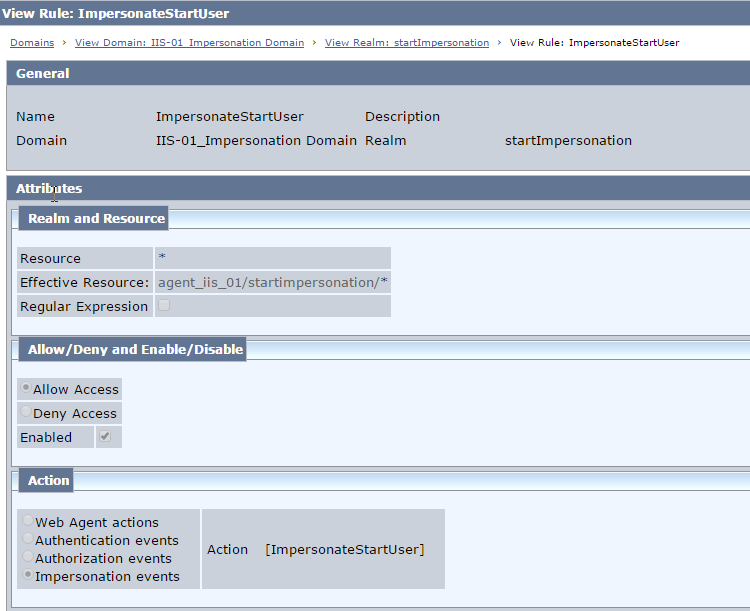
Fig 13 : Impersonators Policy-->Users

Fig 14 : Impersonators Policy --> Rules

Fig 15 : Impersonatees Policy --> Users
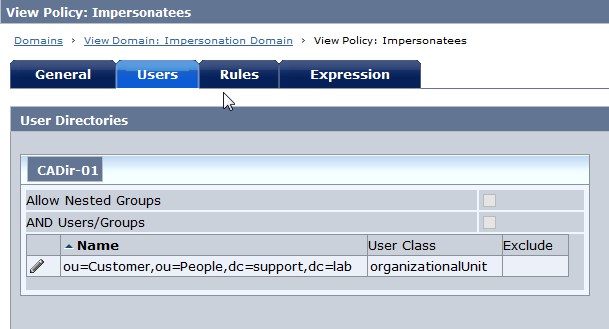
Fig 16 : Impersonatees Policy --> Rules

Fig 17 : StartImpersonation Policy --> Users
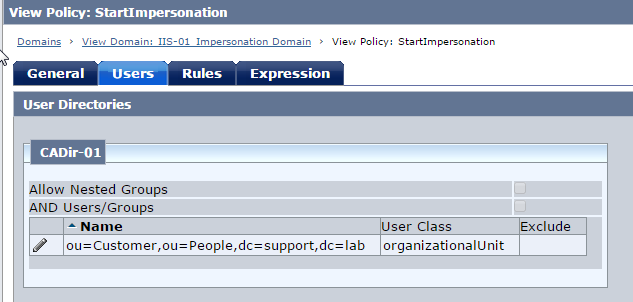
Fig 18 : StartImpersonation Policy --> Rules
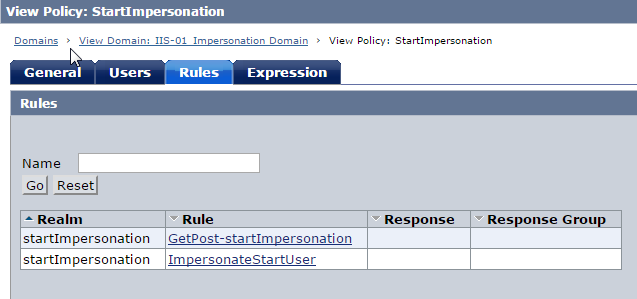
Fig 19 : ACO : OverrideIgnoreExtFilter

Fig 20: ACO : FCCCompatMode

Fig 21: Impersonatee Directory structure

Fig 22: Impersonator Directory structure
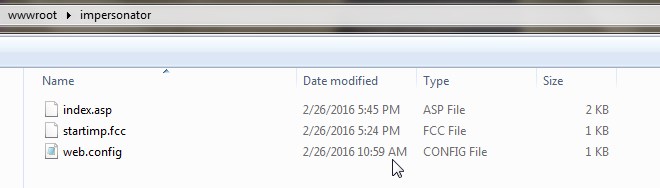
Fig 23: startImpersonation Directory structure

Fig 24: FCC to start Impersonation -startimp.fcc
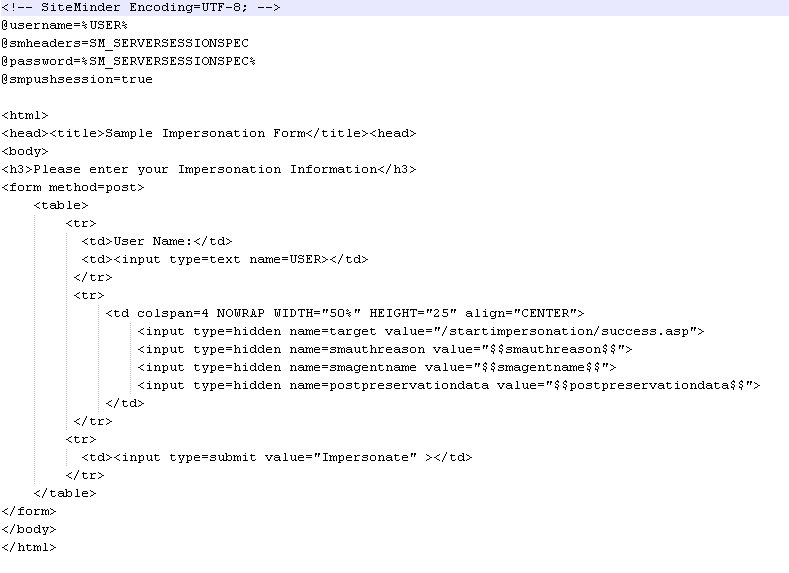
Fig 24: FCC to end impersonation - endimp.fcc
Screenshots - Testing
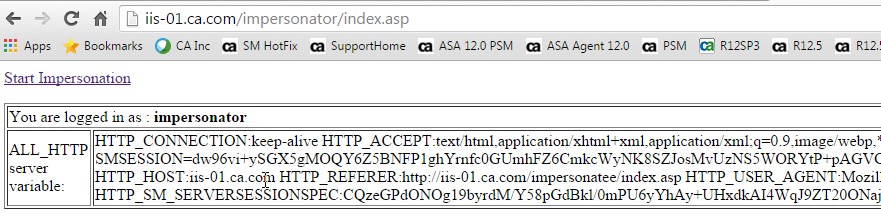
Fig 0: Access Impersonator resource and login as Impersonator
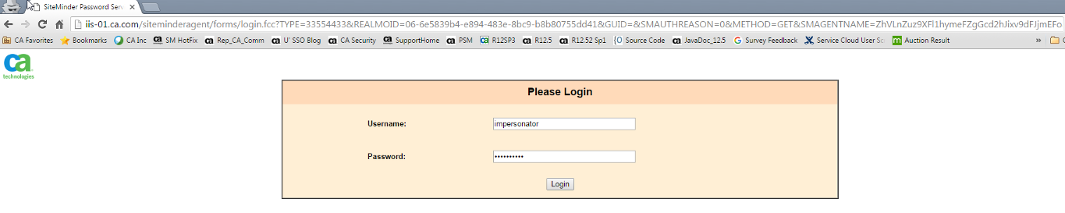
Fig 1: Click link - Start Impersonation

Fig 2: Provide User Id of the Impersonatee and click button - Impersonate

Fig 3 : Impersonation completes successfully and redirects to impersonatee resource /startimpersonation/success.asp which is protected by impersonation authentication scheme. Click link -Browse Impersonatee Realm to browse other impersonatee resources which are not protected by Impersonation authentication scheme (e.g protected by Basic/HTML or Custom Authentication scheme)
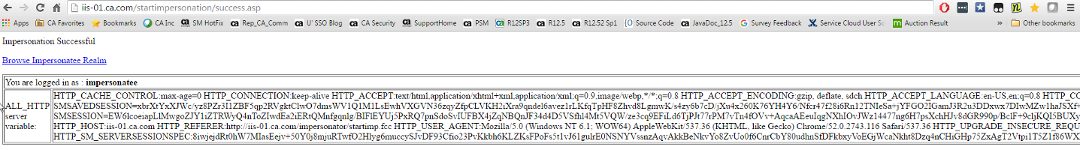
Fig 5: Impersonation completes and redirects to imeprsonatee resource /impersonatee/index.asp. Click link -End Impersonation to end Impersonation
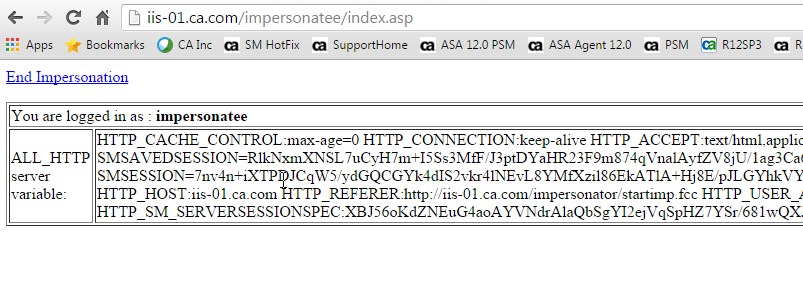
Fig 6: Impersonation ends and redirects back to the Impersonator resource /impersonator/index.asp
Attachments:
- All the sample files
- Fiddler from Impersonation Testing
References
Impersonation - CA Single Sign-On - 12.52 SP1 - CA Technologies Documentation