Hi.
We're using the attached script wrapped around logmon Rules to identify certificates that are about to expire.
It allows for Warning and Critical thresholds, lists all certificates (one per line) except those outside of -IgnoreDaysPast (default -15) and -IgnoreDaysFuture (default 1500). Indication via OK, WARNING or CRITICAL string, fingerprint, days and CN,OU, ... included to be used in variables.
Logmon setup is a bit complex, see screenshots below for examples. I had to set up alerts via Advanced tab to get consistent alerts/clears. Can't remember why unfortunately.
Suppression key uses the fingerprint from the reported entry.
Basic syntax for execution from cmd / logmon: powershell.exe Check-Cert.ps1 -CertStore <Cert Store Path> -WarningDays <Warning Days> -CriticalDays <Critical Days>
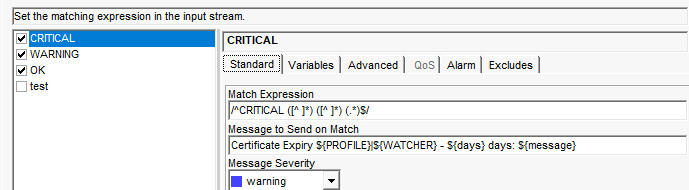



Maybe this helps.
Regards,
Thomas.