Hello David,
We have upgraded the signature hash algorithm to sha384 in the secure version of the hub (hub_secure which is part of the SecureBus). We are planning to upgrade the same in the regular hub as well. i.e. When the hub is in a tunnel server mode (acting as a CA), it would create certs using hash algorithm as sha384.
What can be currently done till a new version of hub is released:
1. Third-party certificates can be used as well with the tunnels.
2. Temporarily deploy secure_hub to the tunnel server system. Cleanup and re-create the required certificates (will be having sha384). Deploy again the regular hub.
Note: Take required backup of the configurations and certs before applying these workarounds.
Reference:
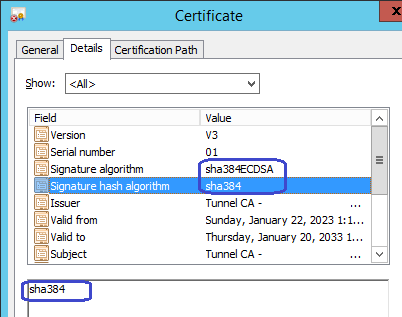
Regards