Useful information to identify which certificate is being used and how it was accepted or not.
Increase MS Windows schannel logging from default value of 1 to level 4.
[NOTE: Reserve the CA abbreviation for Certificate Authority in this discussion; to avoid confusion with product names]
- Do this for both the LDAP client server (Example: Identity Suite's CCS server; where im_ccs is running) and the MS Active Directory Domain Controller that will be used for validation.

When the error message "Confidentiality_Required" within the LDAP client (Example of Identity Suite's IMPS manager gui ) displays, then view the MS Windows event viewer for System/Schannel messages.
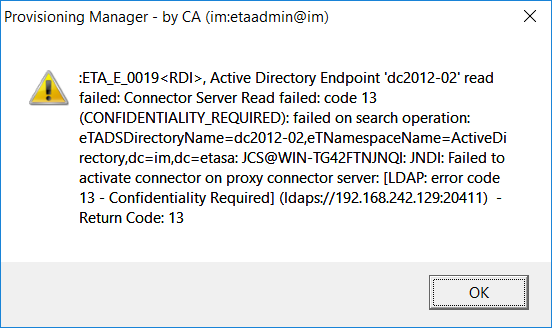
The follow message will be captured on the MS event viewer on the LDAP client server (Example: Identity Suites' CCS server) if the public root CA certificate is NOT deployed to the MS Windows keystore (certlm.msc) on the LDAP client server (Example Identity Suite's CCS server). No message will appear on the ADS DC event viewer.
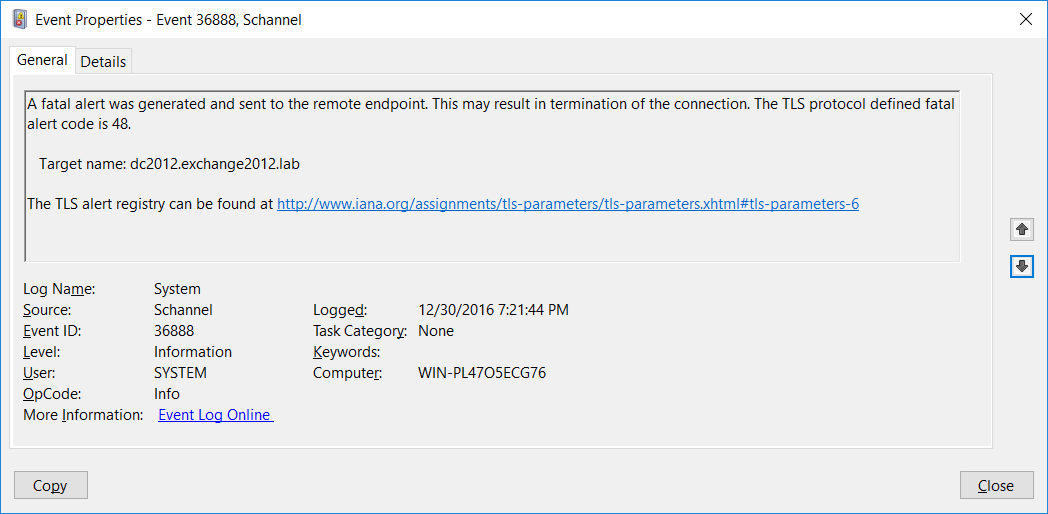
If the above hyperlink is selected, the website for IANA will display the TLS Alert Code value for error code: 48
Which is "unknown CA", e.g. the public root CA certificate (and/or intermediate CA certs)

For successful connection stream, to compare, see the following screens:
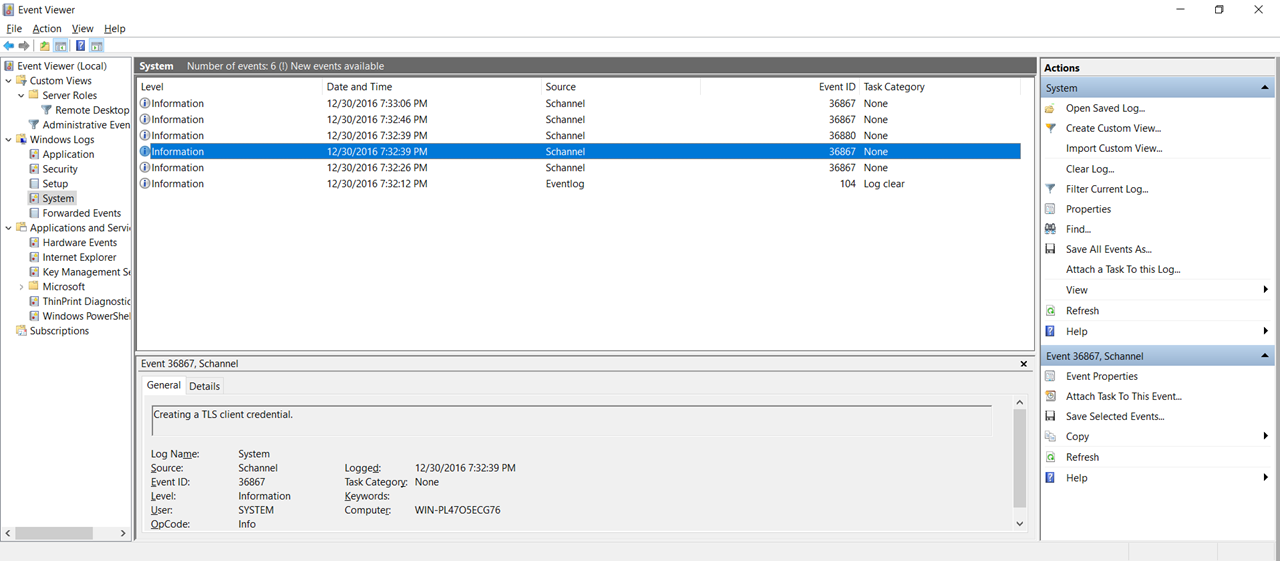
Schannel messages will be captured on BOTH the CCS server AND the ADS DC server.
CCS server below:

On the ADS (2012) Domain Controller server, we see the following:
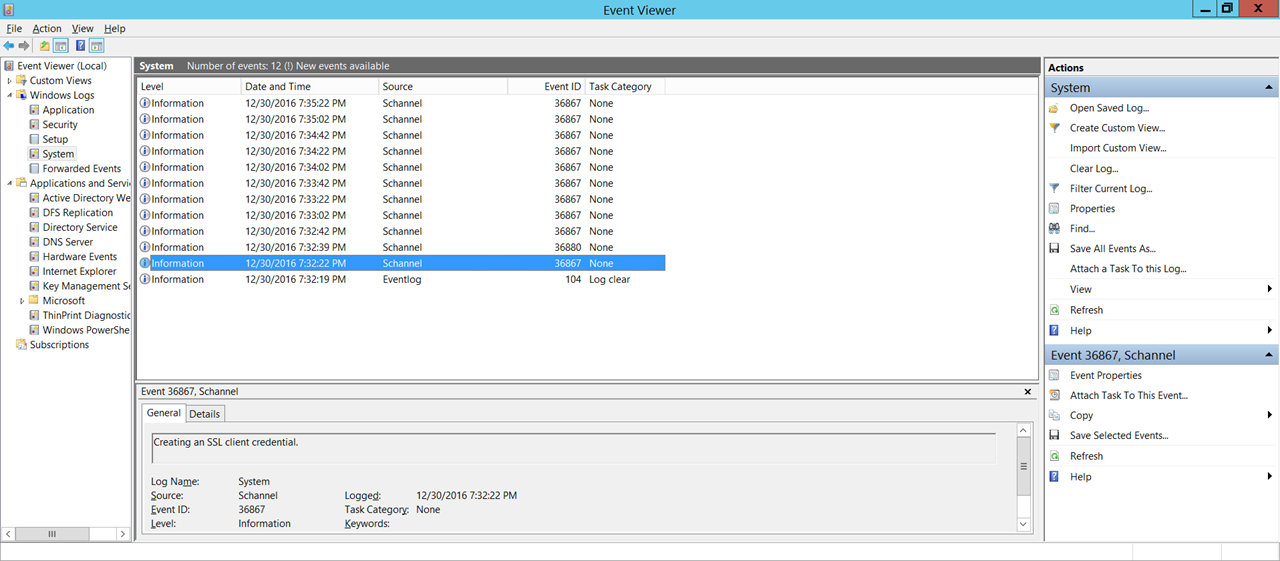
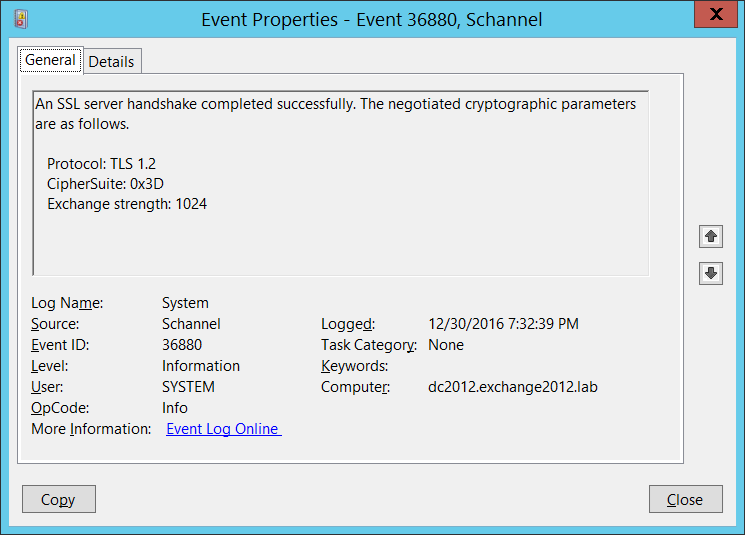
To view WHICH Cipher Suite was used, we can lookup 0x3D from the IANA web site, under the TLS Cipher Suite Registry section.
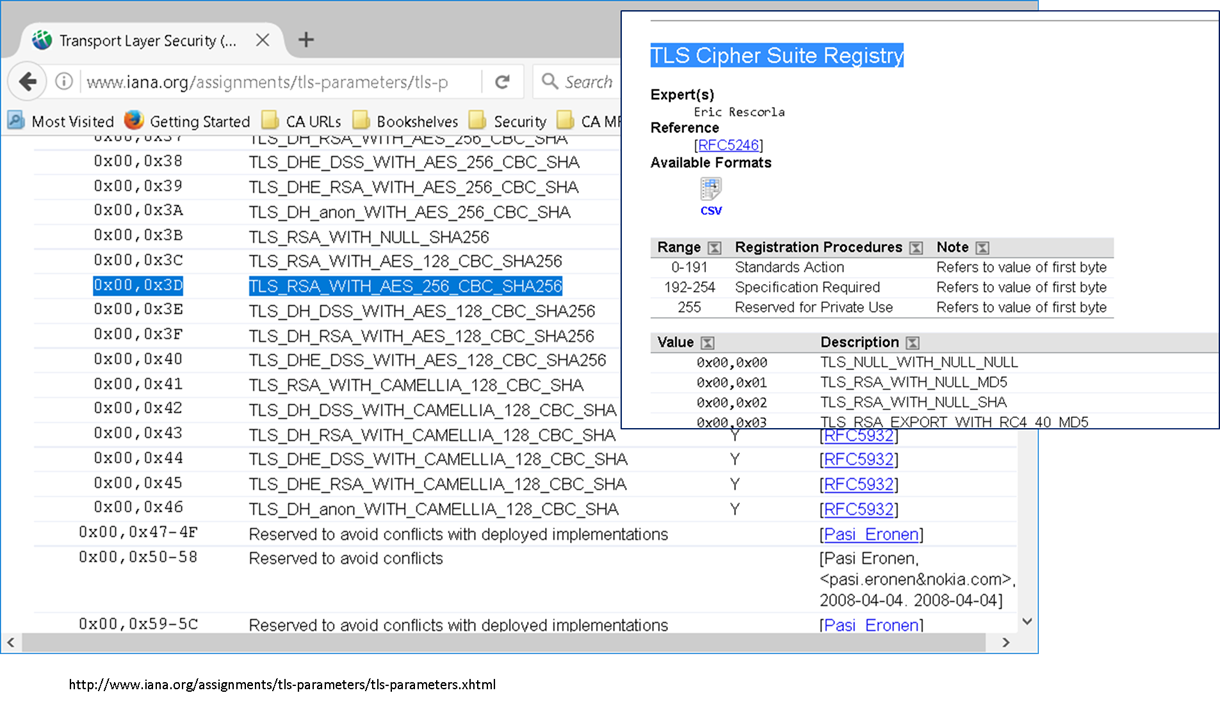
http://www.iana.org/assignments/tls-parameters/tls-parameters.xhtml
Note: The Identity Suite's CCS service does a call to the MS lsass service, which calls the MS schannel to determine which Cipher Suites to use for both LDAP client and LDAP server use. Ensure both of the MS schannel Cipher Suite match on the CCS and ADS DC servers, using gpedit.msc, to avoid a "confidentiality required" error message.
Let me know if you find this of value, for any solution.
Edit: 1/3/2017 - Avoid false error message "Confidentiality Required" due to increased transaction delays.
1. Remote Active Directory servers may increase transaction delay. [WAN or F/Ws]
2. New elliptical Cipher Suites may increase transaction delay during Hello / Exchange Cycle
3. Introduction of the IAMCS as the intermediate tier between the IMPS (prov server) and the CCS service may increase transaction delay
To address the above issue, increased the timeout, to ensure that the communication would complete, within the IMPS server, using the IMPS Manager GUI; from a default of 30 seconds to 120 seconds; and ensure the partial results list was checked.

Cheers,
A.