Hello,
Using CA API Gateway Version 9.2 CR7, I'm unable to use the HTTP(S) Route Assertion with Windows Integrated Authentication. I was wondering if anyone else ran into similar problems.
I currently am trying to publish a Web API that contains the following Policy Assertions. :
- Require Windows Integrated Authentication Credentials
- Route via HTTP(S) with the following Authentication selections.
- Use Windows Integrated
- Use Delegated Credentials
The URL that I'm performing the HTTP GET to in the Route Assertion is configured to use Windows Integrated Authentication as it is a ASP.NET Application hosted in IIS 8.
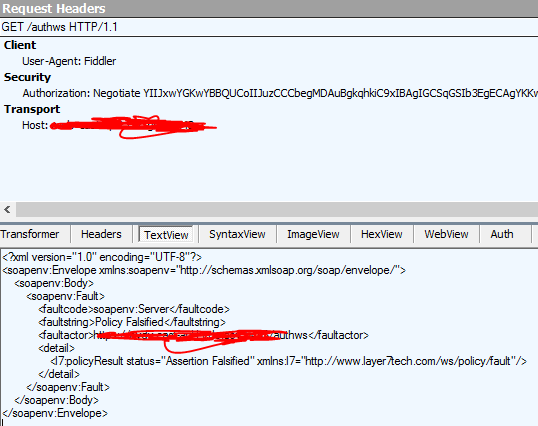
This is where I'm running into issues. The HTTP(S) Route Assertion is failing when I make these selections. Looking in the logs I'm seeing the following:
2018-01-19T09:10:14.737-0500 INFO 10121 com.l7tech.server.message: Processing request for service: AuthWSTest [/authws]
2018-01-19T09:10:14.738-0500 WARNING 10121 com.l7tech.server.policy.assertion.ServerHttpRoutingAssertion: 4043: Routing with Kerberos ticket failed with: Credentials for delegation not found
2018-01-19T09:10:14.738-0500 WARNING 10121 com.l7tech.server.MessageProcessor: 3016: Request routing failed with status 601 (Error in Assertion Processing)
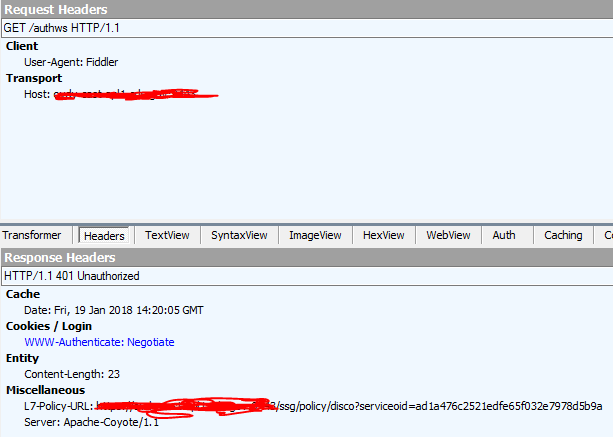
Using the Service Debugger, I've verified that the kerberos.data and kerberos.realm context variables are being populated as seen here:

When making the call via Fiddler I can see API Gateway return the initial 401 Status code with the Authorization: Negotiate header in the Response Headers. Additionally, I can see the client including the Authorization: Negotiate header in the Request after it receives the challenge from the API Gateway. This seems to indicate that Windows Integrated Authentication is working: