Hi dear Community.
I am triying configure a certificate for each wasp (OC, AdminConsole and CABI).
I generated the .CSR of each wasp.
The customer send me the certificate (.CER) for each WASP.
Additionally they send me the root and intermediaty certificate.
I configure the certificates like ----->
keytool -import -trustcacerts -alias cabi.domain.local.cer -file cabi.domain.local.cer -keystore wasp.keystore
keytool -import -trustcacerts -alias adminconsole.domain.local.cer -file adminconsole.domain.local.cer -keystore wasp.keystore
keytool -import -trustcacerts -alias operatorconsole.domain.local.cer -file operatorconsole.domain.local.cer -keystore wasp.keystore
And I configured the root and intermediate like ---->
keytool -import -trustcacerts -alias ROOT.domain.local.crt -file ROOT.domain.local.crt -keystore wasp.keystore
keytool -import -trustcacerts -alias Intermediate.crt -file Intermediate.crt -keystore wasp.keystore
And at the wasp.keystore file I see this ----->
E:\Program Files (x86)\Nimsoft\probes\service\wasp\conf>keytool -list -keystore wasp.keystore
Enter keystore password:
Keystore type: jks
Keystore provider: SUN
Your keystore contains 4 entries
ROOT.domain.local.crt, 13/10/2021, trustedCertEntry,
Certificate fingerprint (SHA1): 36:92:7D:0A:16:FD:2A:E0:53:D1:5A:35:6E:4E:08:E2:2B:65:61:3A
cabi.domain.local.cer, 12/10/2021, trustedCertEntry,
Certificate fingerprint (SHA1): 27:01:62:2B:3D:54:42:6B:9E:DA:65:A8:CD:AB:8D:29:E4:B6:2C:D1
Intermediate.crt, 13/10/2021, trustedCertEntry,
Certificate fingerprint (SHA1): EB:D1:97:FE:18:2A:CA:F1:7D:43:7B:A7:71:24:E9:3F:22:2E:0F:D8
wasp, 11/10/2021, PrivateKeyEntry,
Certificate fingerprint (SHA1): E8:3D:83:19:B9:80:90:F2:74:00:3C:BE:7F:09:A4:CD:3E:BD:D2:78
Warning:
The JKS keystore uses a proprietary format. It is recommended to migrate to PKCS12 which is an industry standard format using "keytool -importkeystore -srckeystore wasp.keystore -destkeystore wasp.keystore -deststoretype pkcs12".
After to configure the cabi certificate for example, the browser indicate "Not Secure"
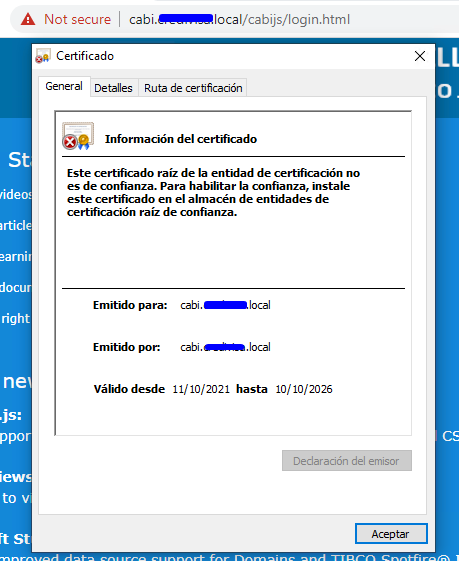
What am I doing bad?