Check Protected Resource Against CA SSO Assertion fails with the same audit message for the the following conditions:
1. /hello1 is configured as unprotected resource in CA SSO
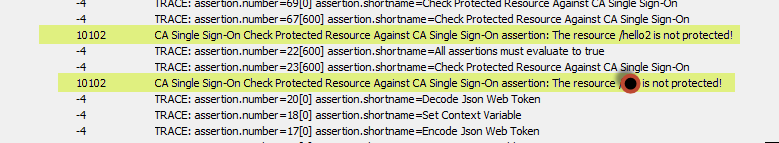
2. /hello2 is not configured at all in CA SSO.
As you can see from the below screen shot that both of them are returning the same audit message though /hello2 is not configured as either protected or unprotected in CA SSO.
I have the following requirement:
1. If the resource is protected, meaning if Check Protected Resource Against CA SSO returns true, then force Authenticate against CASSO
2. If the resource is configured as unprotected in CA SSO (Check Protected Resource Against CA SSO is returning false), then do not force Authenticate against CASSO and allow the user to access the resource.
3. If the resource is not at all configured in CA SSO, then return 401 error.
Since the Check Protected Resource Against CA SSO fails whether the resource is configured as UNPROTECTED or not configured at all in CA SSO, I cannot determine whether to fail with 401 or allow the user.
Is there anything else I can use within API Gateway that can help determine UNPROTECTED and NOT CONFIGURED resource scenarios in CA SSO?
Appreciate your help.