Team,
Using the openssl binary, we can view all ciphers provided by this command line tool.
Using this list, we can test each possible cipher category to a service that has TLS enabled, e.g. an LDAP server or Web Server
To list all cipher possible with openssl.
Ref: /docs/man1.1.0/apps/ciphers.html
openssl ciphers

To test the ciphers, you can execute openssl with the s_client switch.
openssl s_client -cipher RSA -connect vapp0001:20394 [SUCCESSFUL TEST]

Test with category: HIGH ""high" encryption cipher suites. This currently means those with key lengths larger than 128 bits, and some cipher suites with 128-bit keys."
openssl s_client -cipher HIGH -connect vapp0001:20394 [TEST SUCCESS]

openssl s_client -cipher ECDHE-RSA-AES256-GCM-SHA384 -connect vapp0001:20394 [TEST FAILURE]
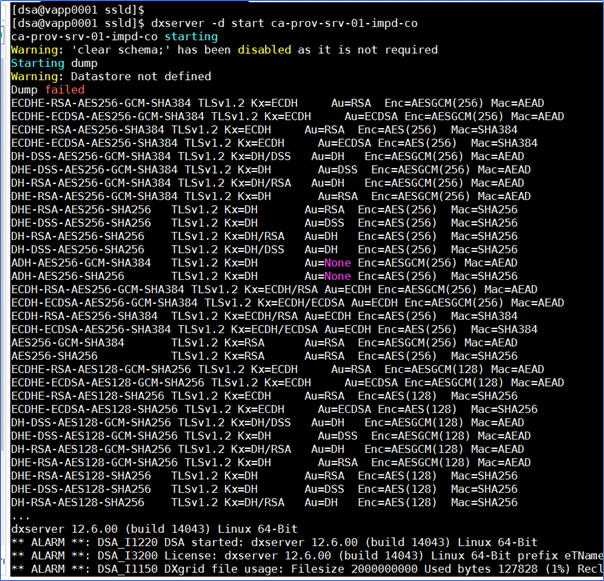
You may wish to skip these tests.
openssl s_client -cipher DEFAULT -connect vapp0001:20394
openssl s_client -cipher ALL -connect vapp0001:2039
openssl s_client -cipher NULL -connect vapp0001:20394
Other examples:
Success:
openssl s_client -cipher EDH -connect vapp0001:20394
Fail:
openssl s_client -cipher ECDH -connect vapp0001:20394
Best example of success for latest release of TLSv1.2
openssl s_client -cipher TLSv1.2 -connect vapp0001:20394
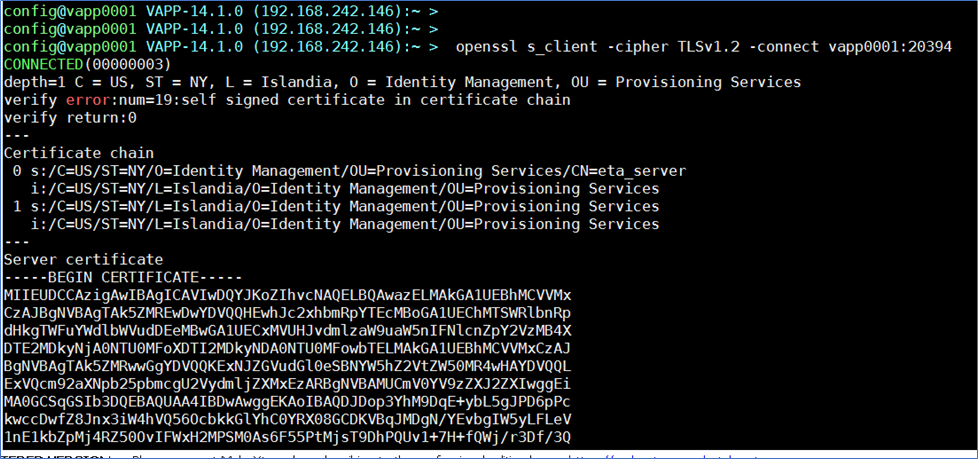
To directly view the CA Directory cipher used (if changed from defaults), you may view these files:
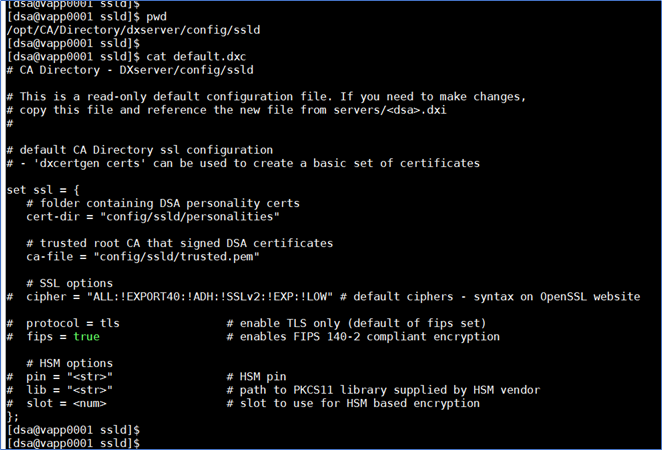
DXHOME/config/ssld/default.dxc
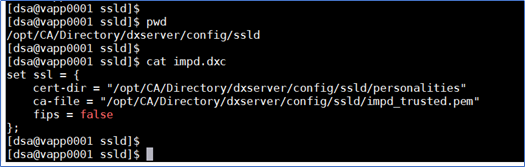
DXHOME/config/ssld/impd.dxc
To view all active CA Directory DSA cipher, open a DXconsole, and issue the command : get ciphers;
- Or add this setting to CA Directory setting <dsa name>.dxc and issue a dxserver init <dsa name>
- Then view the <dsa-name>-trace.logs.

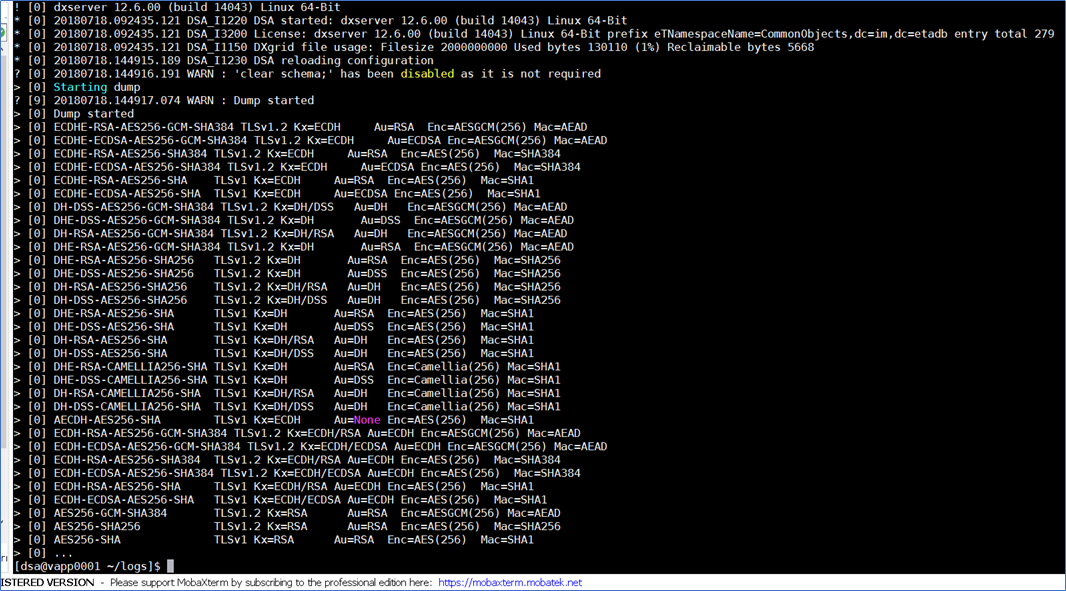
Ref: Encryption Formats for SSL - CA Directory - 12.6 - CA Technologies Documentation
Example to reduce ciphers to TLSv1.2 for CA Directory DSA upon startup:
Edit the DXHOME/config/ssld/impd.dxc (or default.dxc)
- Update the set ssl = { section as shown

Validate working with the -d switch for dxserver -d start <dsa_name>
- should only see validate TLSv1.2 ciphers.

Cheers,
Alan