Summary:
In this guide, we will see how to protect Auth/AZ SPS web service with Basic Authentication and also how to configure web service client to pass the credential while invoking the Auth/AZ web service.
For this use case , we will test with REST web service but the procedure is exactly the same for SOAP web service call as well.
Environment:
- Web Agent : 12.52 and above
- OS : ANY
Instructions:
Protect CA Access Gateway Auth/AZ web service
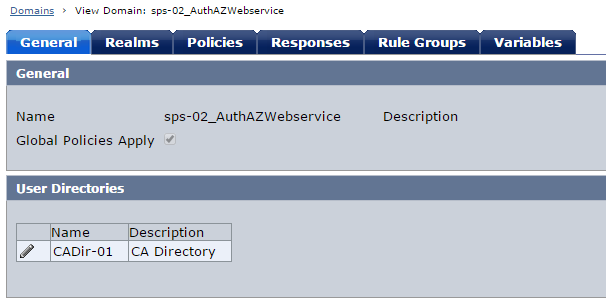
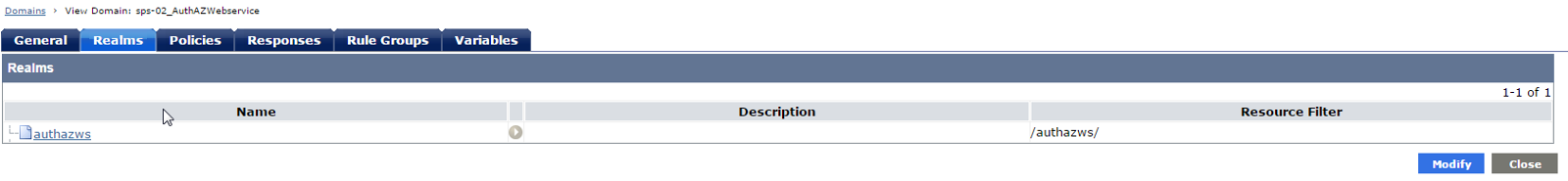
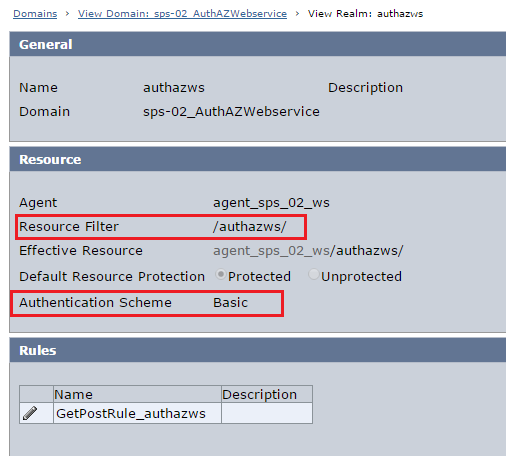
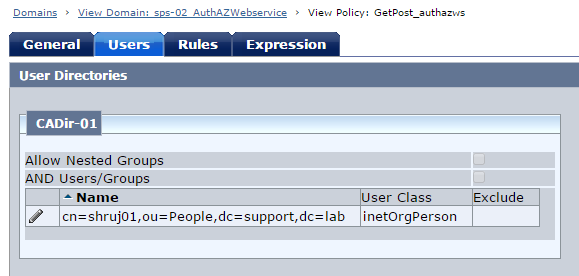
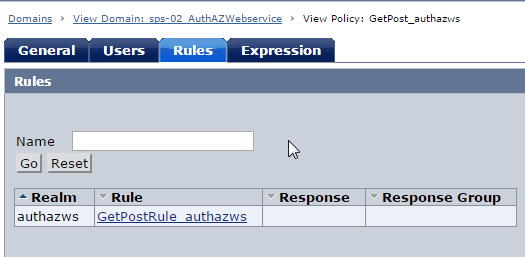
Create Domain/Realm/Rule/Policy to protect the root URL /authazws/. For this demo, only the user "shruj01" is authorised to access Auth/AZ web service resource.
TEST 1 : REST Client ( e.g SOAPUI)
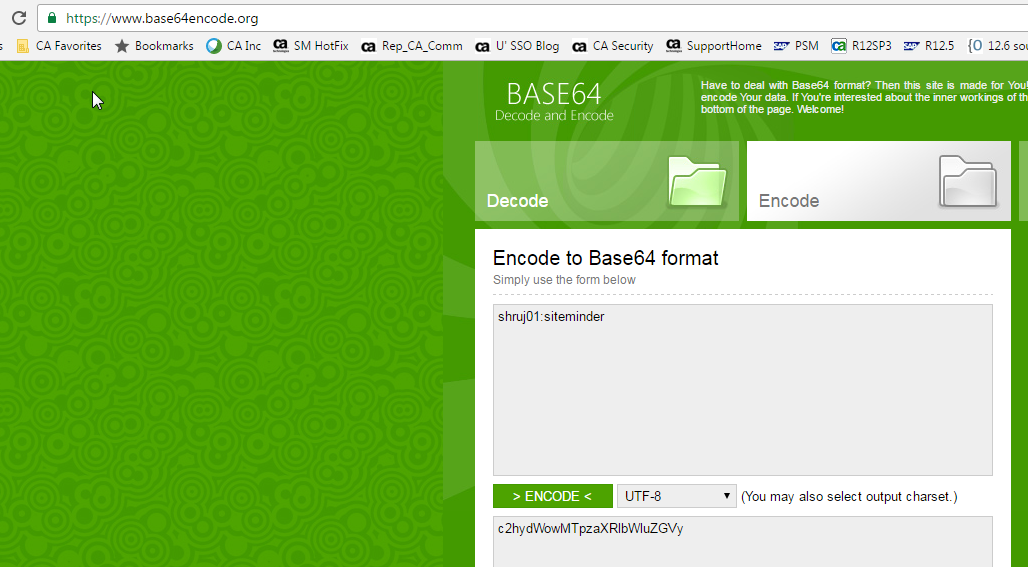
1. Base64 encode the Web service user credential in the format "username:password". This can be done using online tool Base64 Decode and Encode - Online
Copy the encoded output , this will be needed in next step while configuring the REST client.
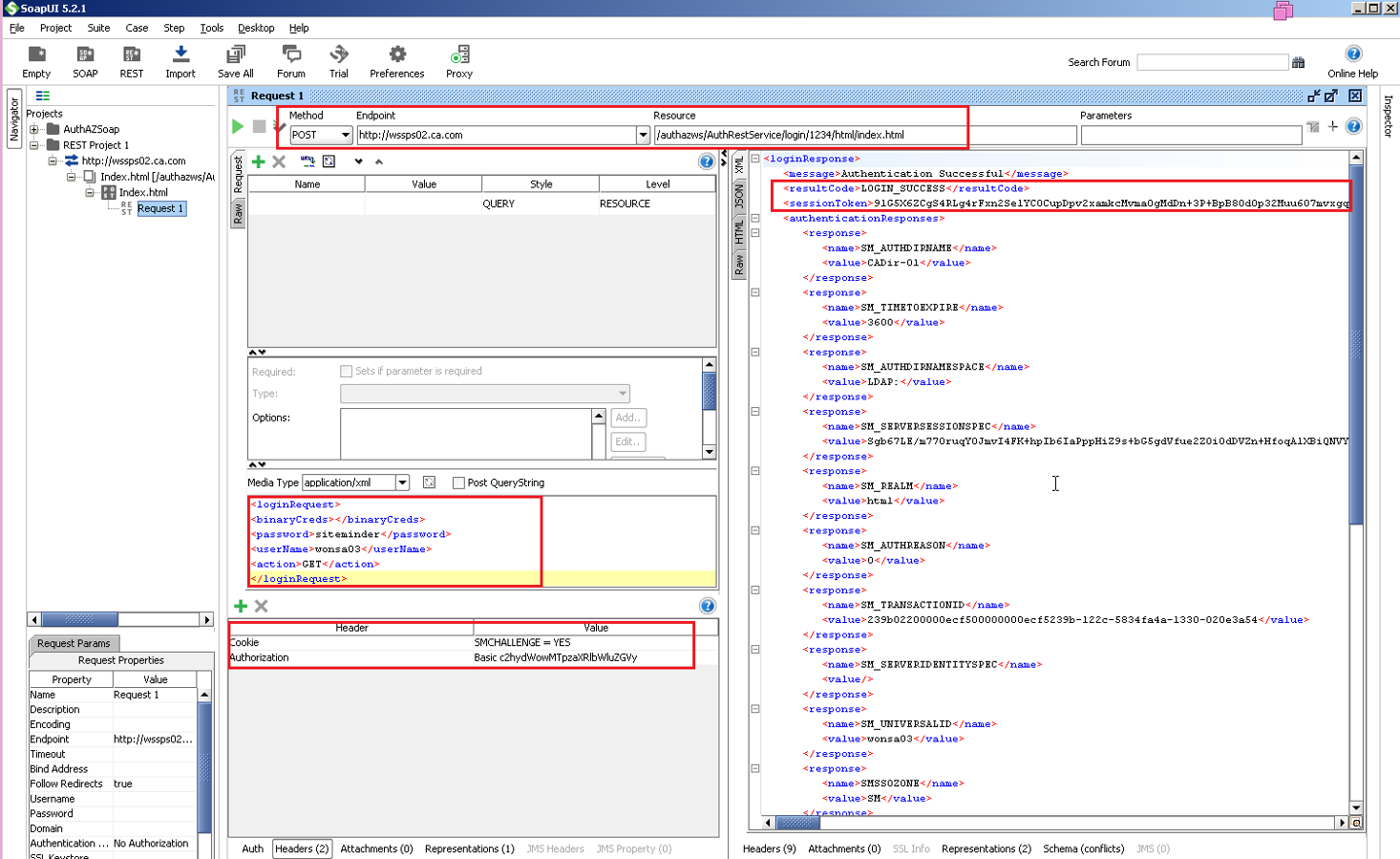
2. Configure the REST Post request as below.
The important thing to note is , as the web service is protected, we now need to send following headers along with the actual REST request.
a. Authorization: Basic <Based64 encoded value of username:password>
b. SMCHALLENGE=YES cookie header ( This is required if RequireCookies= YES in the ACO of the agent protecting the AuthAZ web service resource.
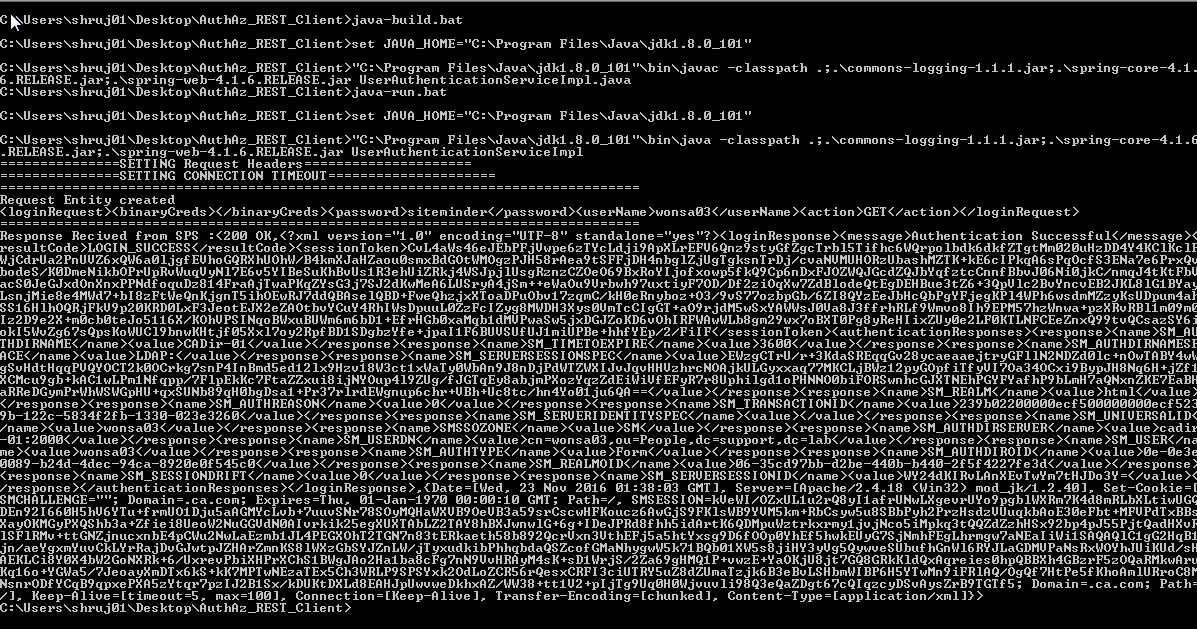
TEST 2: REST Client ( e.g Java)
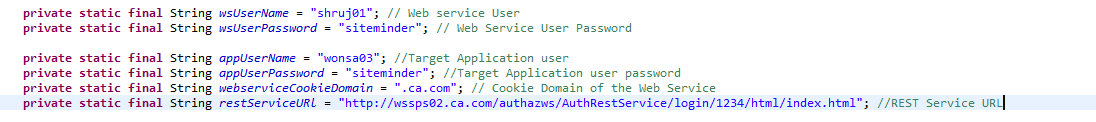
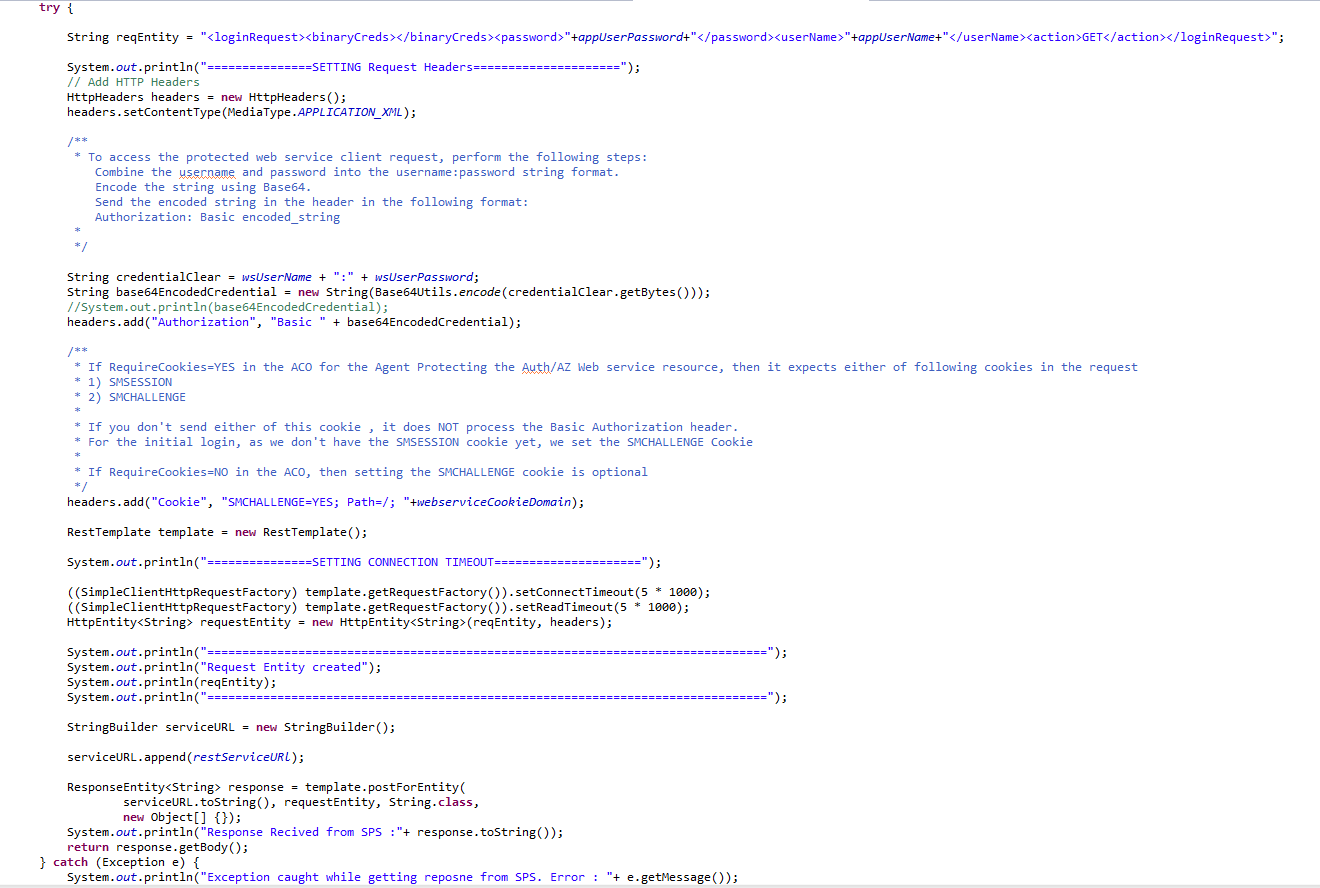
1. Modify the following properties in UserAuthenticationServiceImpl.java as per your environment
2. Modify the JDK home in the java-build.bat and java-run.bat (windows)
3. Compile the Test class by running java-build.bat (windows)/ java-build.sh (unix)
4. Execute the class by running java-run.bat (windows)/java.run.sh (unix)
Sample output :
Sample class :
Attachment:
1. Sample Java program
Additional Information:
Configuring the Authentication and Authorization Web Services - CA Single Sign-On - 12.52 SP1 - CA Technologies Document…