Summary:
The Enhanced Session Assurance with DeviceDNA™ has been completely redesigned in r12.6.
In this blog we will discuss about this new redesigned architecture, compare it with old architecture and also review the steps required to configure it in the new design.
Environment:
- Policy Server : R12.6
- CA Access Gateway : R12.6
So what has changed ?
To understand this, let's see what the earlier design was.
The existing design of session assurance implementation relied on following components :
Policy Server
- CA RiskMinder Service (aka CA Advanced Authentication Server)
CA Access Gateway
- Session Assurance Flow App - This App interacts with the Policy server using AgentAPI. This also interacts with CA RiskMinder services via JDBC-ODBC bridge.

Problems with the existing design
- Heavy footprint of CA Advanced Authentication components on both Policy server and CA Access Gateway servers.
- Difficult to maintain Resource.dat & Master Key file.
- Complex PS/Access Gateway upgrade path
The New Design
- Removed CA Advanced Authentication components on Policy server.
- Simplified Session Assurance Flow App on CA Access Gateway by developing it using CA Advanced Authentication SDK.

What this now mean is:
- Advanced Authentication Server is not installed on the Policy Server.
- Default domain “AdvAuthDEFAULTORG” and host configuration objects those were created in previous releases for use of Advanced Auth Server are no more created.
- No Master Key.
- DSN for Advanced Authentication Server is not created on PS & CA Access Gateway
- Resource.dat is not created in Policy server/bin directory.
- Previously deployed web apps - uiapp, aaloginservice,authapp is now replaced with just one new "sessionassuranceapp" on CA Access Gateway.
How do I configure Session Assurance now?
Following are the steps required to configure session assurance now :
CA Access Gateway
- Install CA Access Gateway 12.6
- Configure CA Access Gateway to use SSL for front end Apache
- Ensure SessAssurance Application is enabled in server.conf :
<Context name="SessionAssuarance Application">
docBase="sessionassuranceapp"
path="authapp"
enable="yes"
</Context>
- Ensure SACExt ACO parameter value is .sac
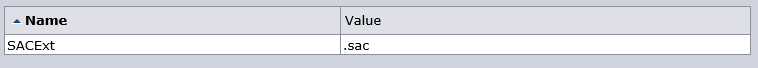
- Ensure IgnoreExt ACO parameter contains .sac extension

CA SSO Policy Server
- Install CA SSO Policy server to 12.6
- Create Session Assurance End Point as below :
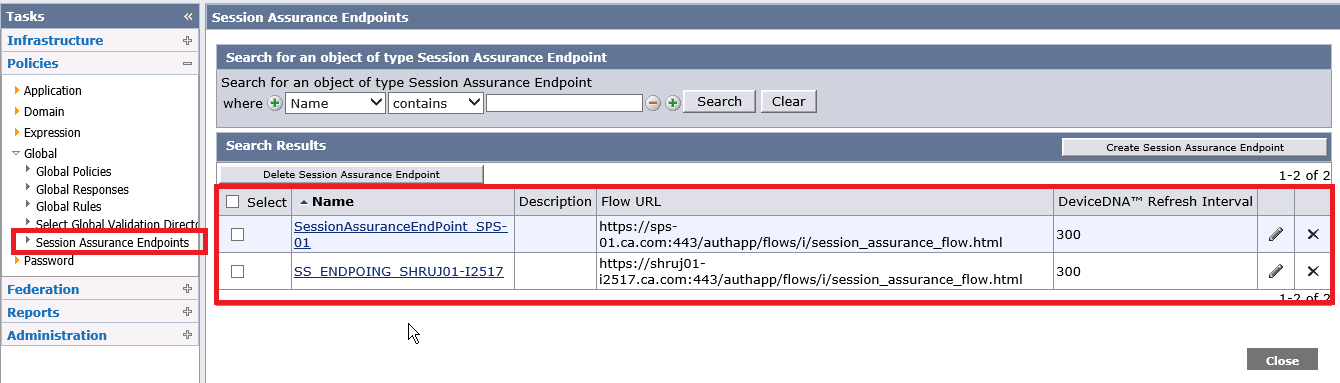

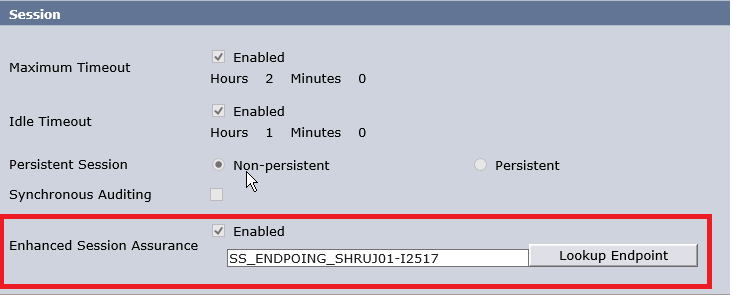
- Enable Session Server on the Policy server.

- Add Session Assurance End Point to the realm for which you want to enable the session assurance functionality.
(It is optional to configure realm as persistent)
Configure Log Files for Troubleshooting
1. Enable Audit Logs and also configure Enable Enhanced Tracing on the Policy server.
Navigate to following in the registry editor :
HKEY_LOCAL_MACHINE\SOFTWARE\Netegrity\SiteMinder\CurrentVersion\Reports
Add following dword :
"Enable Enhance Tracing"=1 The Audit logs contains authentication and authorisation activity related to Session Assurance flow.
The Audit logs contains authentication and authorisation activity related to Session Assurance flow.
2. Enable debug logging for Session Assurance Flow app on CA Access Gateway
Navigate to CA\secure-proxy\Tomcat\webapps\sessionassuranceapp\WEB-INF\classes and set the log level to DEBUG in log4j.properties as below:
# Define the root logger with appender SAFileAppender
log4j.rootLogger = DEBUG, SAFileAppender
# Set the appender named SAFileAppender to be a File appender
log4j.appender.SAFileAppender=org.apache.log4j.FileAppender
log4j.appender.SAFileAppender.File=${catalina.base}/../proxy-engine/logs/SessionAssuranceApp.log
log4j.appender.SAFileAppender.layout=org.apache.log4j.PatternLayout
log4j.appender.SAFileAppender.layout.conversionPattern=%d{yyyy-MM-dd HH:mm:ss} %-5p %c{1}:- %m%n
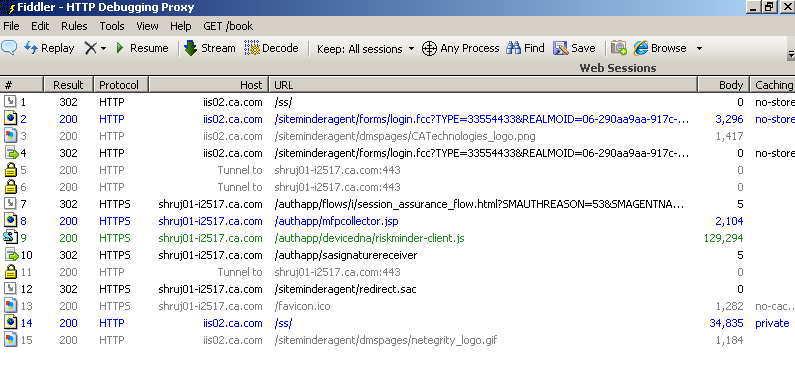
Testing:
Additional Information:
Configure Enhanced Session Assurance with DeviceDNA™ - CA Single Sign-On - 12.6.01 - CA Technologies Documentation